The Cost of a Data Breach Report 2023 by the IT giant IBM stated that the average cost of a data breach had reached an all-time high of USD 4.45 million in 2023. This represents a 2.3% increase from 2022. However, the average cost of a data breach for organizations with high levels of security skill shortages has risen to USD 5.36 million.
This is an example of cyber risk quantification.
Cyber risk quantification has gained significant importance in today’s cybersecurity landscape due to the escalating frequency and sophistication of cyberattacks, making it crucial for organizations to understand the financial implications of potential breaches.
The objective of this article is to delve deeper into the concept of cyber risk quantification, exploring its benefits, modules, and best practices.
What is cyber risk quantification?
Cyber risk quantification is the process of evaluating and measuring the potential financial impact of cyber threats and vulnerabilities on an organization. It means putting a price tag on cyber risks to understand how much a potential cyberattack could cost financially.
Cyber risk quantification holds significant significance in assessing cyber threats.
1. Risk Prioritization
One of its key roles is to aid in prioritizing risks effectively. By assigning monetary values to various risks, organizations can identify and focus their efforts on addressing the most critical vulnerabilities first. This approach enhances overall cybersecurity readiness and resource allocation.
For e.g., cyber risks such as malware infections, phishing attacks, and insider threats can impact the supply of goods in an industry.
2. Decision Making
Furthermore, cyber risk quantification facilitates informed decision-making within organizations. Decision-makers are provided with the necessary insights to make choices regarding cybersecurity investments. This allows for the effective allocation of resources, ensuring that investments are channeled into areas where they will have the most significant impact.
Carrying on the above example, the decision-makers will then provide a decision on how much should be invested in cybersecurity. They will prioritize the above risks and place a monetary value on each risk to make the decision.
3. Risk Mitigation
Cyber risk quantification also plays a pivotal role in risk mitigation. It helps organizations develop and implement strategies to mitigate risks effectively. By assessing the cost-effectiveness of various security measures, organizations can determine which ones will provide the best return on investment in terms of risk reduction.
Considering the return on investment (ROI) of cybersecurity is imperative as every organization doesn’t necessarily need Z-level security. You should consider the risk tolerance of your organization before investing heavily in cybersecurity.
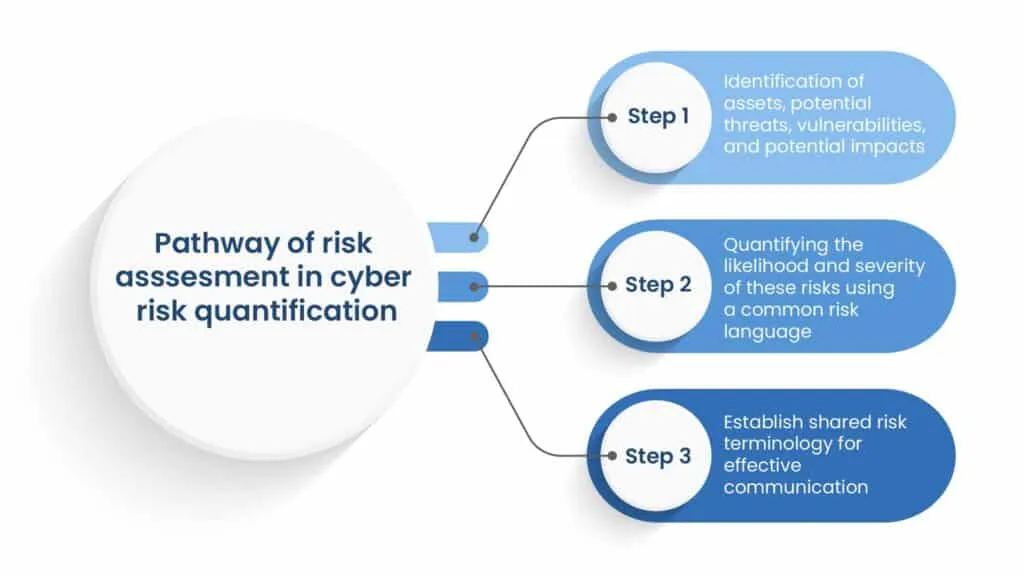
How does cyber risk quantification work?
The process of cyber risk quantification involves several steps, including:
- asset valuation,
- risk assessment, and
- financial estimation.
Each asset within an organization is assigned a value based on its importance to the business operations. Risk assessment takes into account factors such as vulnerabilities and potential threat actors. By combining asset valuation and risk assessment, cyber risk quantification quantifies the financial impact of potential cyberattacks. It calculates the potential monetary losses an organization could face in the event of a cyber incident.
The very basic formula for the calculation of cyber risk quantification is:
In essence, cyber risk quantification expresses cyber risks in financial terms, enabling organizations to make well-informed decisions, prioritize their cybersecurity efforts, and effectively manage their risk exposure. It provides a common language that resonates with business leaders, facilitating better communication and understanding of cybersecurity risks and their potential financial consequences.
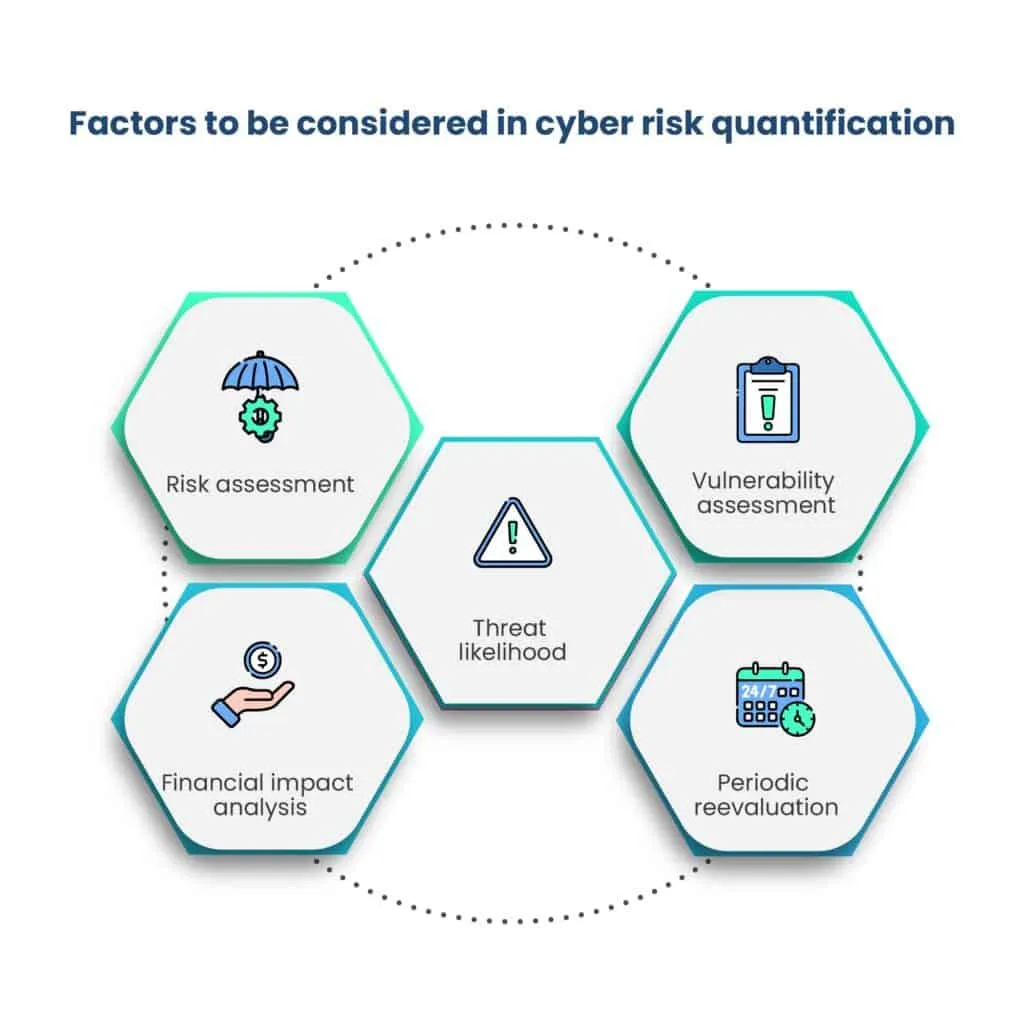
In cyber risk quantification, key concepts include financial analysis, threat likelihood assessment, vulnerability identification, and regular reevaluation. These ensure effective management of cyber threats, enabling informed decision-making amid evolving cybersecurity landscapes.
Factors to consider when quantifying cyber risks:
1. Risk assessment
Risk assessment in cyber risk quantification involves the systematic process of identifying, analyzing, and evaluating cyber risks that an organization faces.
2. Financial impact analysis
Cyber risk quantification evaluates the potential financial consequences of cyber threats through a financial impact analysis. This analysis quantifies the monetary losses an organization could incur due to cyber incidents.
Financial models play a crucial role in this process, as they help estimate the direct and indirect costs associated with data breaches, downtime, legal liabilities, and reputation damage. By quantifying these impacts, organizations can make informed decisions about cybersecurity investments, insurance coverage, and risk mitigation strategies.
3. Threat likelihood
In cyber risk quantification, the likelihood of specific cyber threats occurring is a fundamental consideration. It takes into account various factors, such as historical threat data, threat intelligence, and the organization’s industry and geographic location. Threat likelihood assessments help organizations prioritize their defenses and allocate resources effectively. Factors influencing threat likelihood include the sophistication of threat actors, the organization’s security posture, and emerging threat trends.
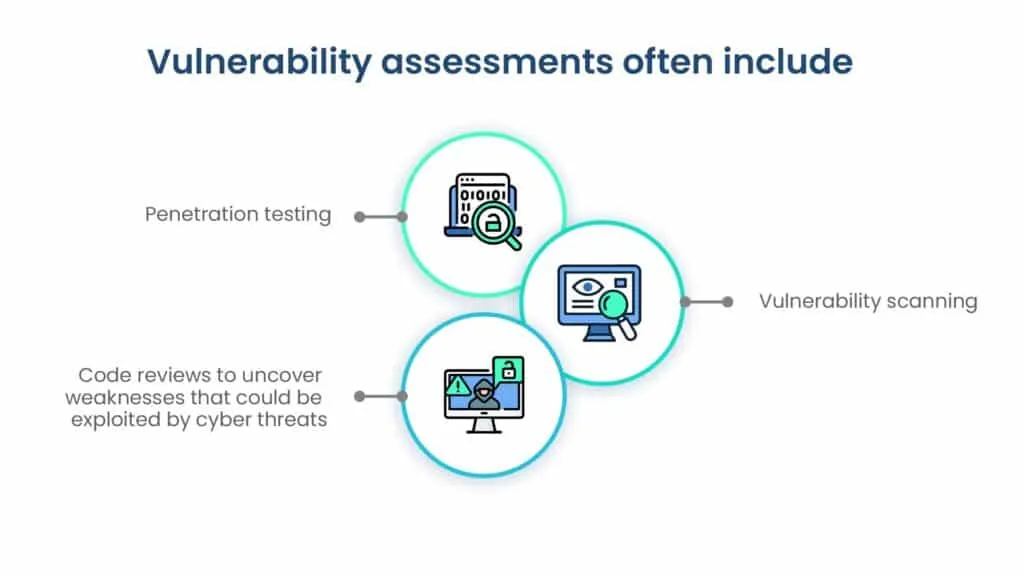
4. Vulnerability assessment
Vulnerability assessments are a critical component of cyber risk quantification, as they involve identifying security vulnerabilities within an organization’s systems, processes, and assets. Vulnerability assessments are closely tied to cyber risk quantification because identifying vulnerabilities is essential for quantifying the potential risks and financial impacts associated with cyber threats. Effective vulnerability management is key to reducing risk.
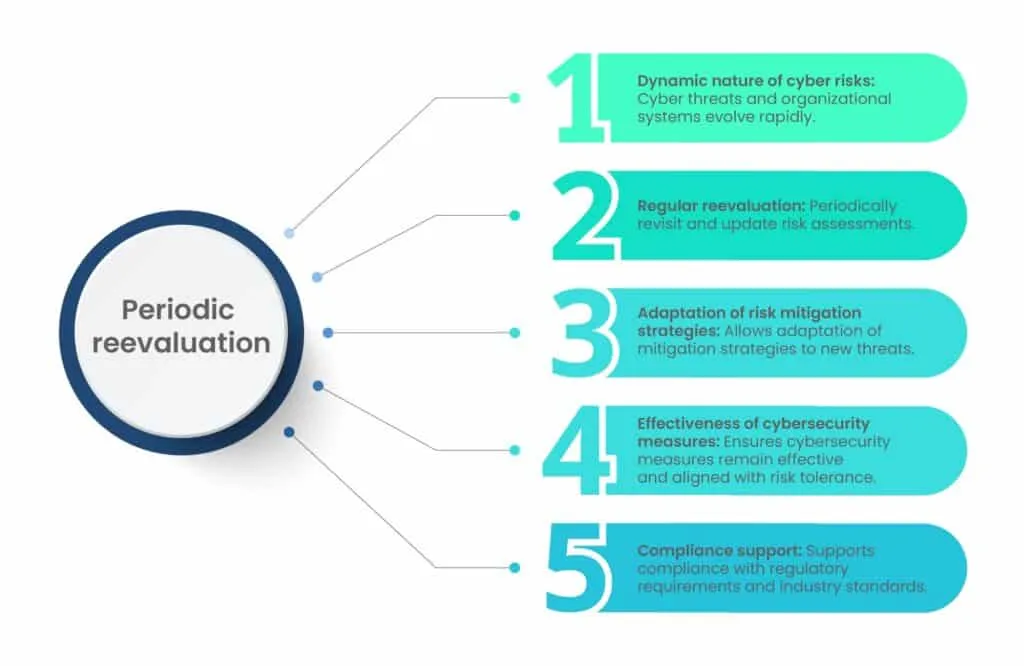
5. Periodic reevaluation
Cyber risk quantification models
Cyber risk can be quantified using various models. Each of these CRQ models provides valuable tools and methodologies for organizations to assess, quantify, and manage cyber risks effectively. The choice of model may depend on an organization’s specific needs, resources, and risk management objectives.
1. FAIR Model
The Factor Analysis of Information Risk (FAIR) model is a quantitative framework used to assess and quantify cyber risks based on financial loss probabilities. It is designed to provide a structured approach to understanding and managing information security and cyber risk in financial terms.
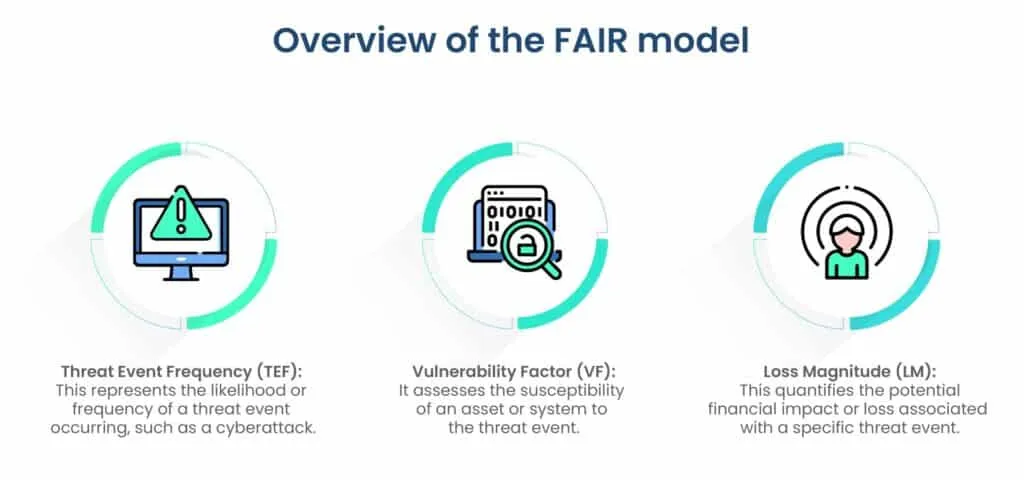
The FAIR model often employs a five-point scale for each component, ranging from “Very Low” to “Very High” to assign values to TEF, VF, and LM.
The output of the FAIR model is typically expressed in financial terms, such as dollars, and provides a clear understanding of the expected loss or risk exposure associated with specific cyber threats.
2. Monte Carlo simulations
Monte Carlo simulations are a statistical technique employed within cyber risk quantification models to estimate metrics like Value at Risk (VaR) or expected loss. These simulations entail the execution of numerous model iterations, each incorporating randomly generated input variables falling within predefined ranges.
In the realm of cyber risk quantification, these input variables encompass elements such as threat event frequencies, vulnerability factors, and loss magnitudes.
Through the execution of thousands or even millions of such simulations, Monte Carlo simulations yield a probability distribution that outlines potential outcomes. This distribution is instrumental in enabling organizations to gain a comprehensive understanding of the spectrum of conceivable financial losses, along with their associated probabilities.
Ultimately, Monte Carlo simulations equip decision-makers with valuable insights, facilitating a more informed approach to evaluating the potential financial impact of cyber risks, thereby aiding in risk mitigation strategies and budget allocation.
3. NIST 800-30
NIST 800-30 is a comprehensive framework developed by NIST for conducting risk assessments in information security and cyber risk management.
a. Structured risk assessment process:
Core of NIST 800-30 involves a structured risk assessment process covering stages such as risk identification, analysis, evaluation, and formulation of mitigation strategies. This systematic approach aids organizations in addressing cyber threats effectively.
b. Guidance on Risk Management Framework (RMF):
Provides guidance on integrating risk management principles into an organization’s cybersecurity program through the establishment of a Risk Management Framework (RMF). This ensures continuous and integral risk assessment within an organization’s security posture.
c. Emphasis on vulnerability assessments:
Places a strong emphasis on conducting Vulnerability Assessments to identify weaknesses and susceptibilities in an organization’s systems, processes, and assets. This aids in mitigating potential cyber threats effectively.
d. Asset valuation for financial impact assessment:
Assists organizations in quantifying the potential financial impact of cyber incidents by aiding in the valuation of assets. This step is crucial for understanding the financial implications of cyberattacks and data breaches, enabling informed decision-making and resource allocation.
4. CyberInsight:
CyberInsight adopts a structured and systematic approach, allowing organizations to methodically evaluate cyber threats and vulnerabilities, ensuring a comprehensive assessment of their cybersecurity landscape.
a. Financial perspective
Similar to the FAIR model, CyberInsight often utilizes a financial perspective for assessing cyber risks, enabling organizations to understand potential monetary losses from cyber incidents and devise effective risk management strategies.
b. Risk prioritization
CyberInsight assists in identifying and prioritizing high-risk areas with significant financial impact, allowing organizations to allocate cybersecurity resources efficiently and address critical vulnerabilities promptly [3].
c. Data-driven decision-making
It relies on data and rigorous analysis, empowering organizations to base their cybersecurity strategies on empirical evidence and insights, fostering a proactive and informed approach to cybersecurity and risk management.
Benefits of implementing cyber risk quantification
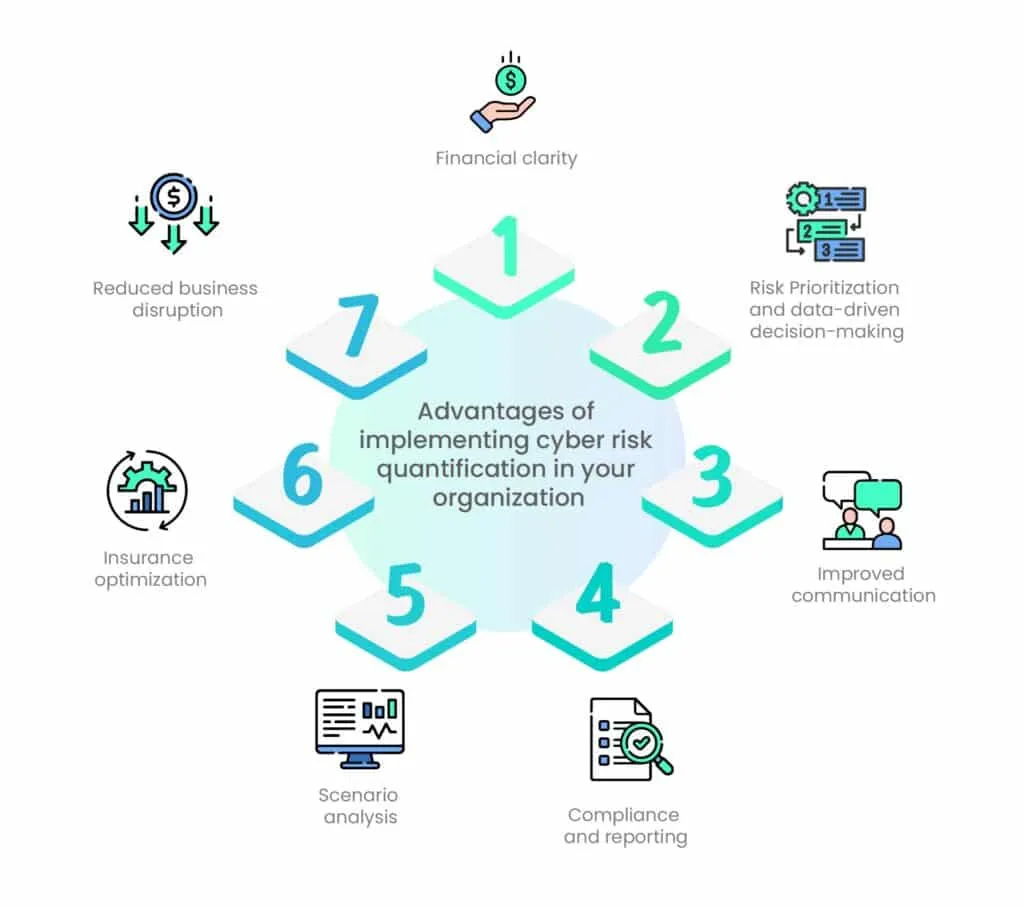
Implementing cyber risk quantification within an organization offers numerous benefits, which can help enhance cybersecurity efforts, improve risk management, and support informed decision-making. Some of the key advantages include:
1. Financial clarity
Cyber risk quantification provides a structured framework for quantifying cyber risks in financial terms. This enables organizations to understand the potential financial impact of cyber incidents, aiding in risk mitigation and budgeting. It helps in aligning cybersecurity investments with the organization’s risk tolerance and financial capabilities.
2. Risk Prioritization and data-driven decision-making
Cyber risk quantification enables organizations to prioritize cybersecurity efforts based on the financial impact of various threats and vulnerabilities, enhancing the overall security posture. Additionally, it relies on data and analysis to provide decision-makers with empirical insights into cyber risks, enabling informed choices regarding risk mitigation strategies, insurance coverage, and security investments.
3. Improved communication
By using a common risk language and presenting risk assessments in financial terms, cyber risk quantification facilitates better communication among various stakeholders, including executives, IT teams, and board members. This alignment of understanding enhances cooperation and collaboration in addressing cyber risks.
4. Compliance and reporting
Many regulatory frameworks and industry standards require organizations to assess and manage cyber risks effectively. Cyber risk quantification helps organizations meet these compliance requirements by providing a structured approach to risk assessment and reporting.
5. Scenario analysis
Cyber risk quantification models often allow organizations to conduct scenario analysis, simulating the potential impact of different cyber incidents. This helps organizations prepare for various threat scenarios and develop effective incident response plans.
6. Insurance optimization
Cyber risk quantification can aid organizations in optimizing their cyber insurance coverage. By quantifying potential financial losses, organizations can better determine the appropriate level of coverage and negotiate insurance premiums more effectively.
7. Reduced business disruption
By identifying and mitigating high-impact risks, cyber risk quantification can help prevent or minimize business disruptions caused by cyber incidents. This, in turn, can lead to cost savings and the preservation of the organization’s reputation.
Winding up
In conclusion, Cyber Risk Quantification (CRQ) is an essential tool in today’s cybersecurity landscape, helping organizations understand the financial implications of cyber threats. With data breach costs at an all-time high, cyber risk quantification plays a crucial role in risk prioritization, informed decision-making, and effective risk mitigation.
As cyber threats evolve, organizations embracing cyber risk quantification not only enhance their cybersecurity but also position themselves to proactively manage risks, make informed decisions, and safeguard their assets in an increasingly interconnected digital world.
Ready to take control of your organization’s cybersecurity and financial resilience? Start implementing Cyber Risk Quantification (CRQ) today to understand and manage your cyber risks effectively.
Reach out to our team of experts at Scrut for personalized guidance and solutions tailored to your organization’s needs. Don’t wait until the next data breach—secure your digital assets and financial stability now!
Cyber Risk Quantification is the process of evaluating and measuring the potential financial impact of cyber threats and vulnerabilities on an organization. It involves assigning monetary values to these risks to provide a clear understanding of their financial implications. CRQ is crucial because it helps organizations understand the financial consequences of potential cyberattacks. It enables informed decision-making, resource allocation, and prioritization of cybersecurity efforts.
Cyber risk quantification assigns monetary values to risks, allowing organizations to focus on addressing the most critical vulnerabilities first. This approach enhances overall cybersecurity readiness.
Yes, cyber risk quantification assists organizations in determining the appropriate level of cyber insurance coverage by quantifying potential financial losses, making negotiations with insurers more effective.





































