Choose risk-first compliance that’s always on, built for you.
Go back to blogs
FedRAMP Rev 5: A guide to transition, baseline, and beyond
Last updated on
April 17, 2025
16
min. read

The Federal Risk and Authorization Management Program, commonly known as FedRAMP, is a pivotal framework devised by the U.S. government to ensure the security and compliance of cloud services used in federal agencies. It offers a standardized approach for assessing and authorizing cloud products and services, fostering efficiency, cost-effectiveness, and security across the federal landscape.
FedRAMP has been instrumental in modernizing government IT systems, enabling agencies to leverage the advantages of cloud computing while maintaining the highest standards of cybersecurity and compliance. Since its inception, it has played a crucial role in the government’s digital transformation efforts.
The release of FedRAMP Revision 5 (Rev 5) marks a significant milestone in the program’s evolution. Building upon the foundations laid by its predecessors, Rev. 5 introduces crucial updates and enhancements designed to keep pace with the ever-evolving technology landscape and the growing complexity of cyber threats.
FedRAMP Rev 5 brings about fundamental changes, such as revised security baselines, updated controls, and a more streamlined transition process. These changes impact cloud service providers, federal agencies, and the broader ecosystem of stakeholders involved in FedRAMP compliance. Understanding and adapting to these changes is not only necessary but also strategically advantageous.
Overview of the FedRAMP Rev 5 transition
The transition to FedRAMP Rev 5 represents a significant shift in the federal government’s approach to cloud security and compliance. Here we provide an overview of what this transition entails, the key changes and improvements it brings to the table.
A. Key changes and improvements
FedRAMP Rev 5 introduces several critical changes and improvements, including:
- Revised security baselines: One of the most notable changes is the updated security baselines. These FedRAMP Rev 5 baselines have been refined to align more closely with the evolving threat landscape and best practices in cybersecurity. Expect changes in controls, requirements, and focus areas.
- Enhanced flexibility: Rev. 5 places a greater emphasis on flexibility, allowing cloud service providers (CSPs) to tailor their security solutions to better meet the unique needs of federal agencies. This flexibility promotes innovation and efficiency in compliance efforts.
- Streamlined authorization process: The FedRAMP transition aims to streamline the authorization process, reducing the time and effort required for CSPs to achieve compliance. This means faster access to the federal market for compliant cloud services.
- Incorporation of NIST SP 800-53: FedRAMP Rev 5 incorporates the latest version of the National Institute of Standards and Technology (NIST) Special Publication 800-53, enhancing the rigor and comprehensiveness of security controls.
B. Benefits of transitioning to FedRAMP Rev 5
Transitioning to FedRAMP Rev 5 offers a multitude of benefits for both cloud service providers and federal agencies:
- Enhanced security: The updated security baselines and controls ensure that cloud services meet the highest standards of cloud security assessment, safeguarding federal data and systems against modern cyber threats.
- Faster authorization: The streamlined authorization process accelerates the time it takes for CSPs to gain FedRAMP compliance, reducing barriers to entry into the federal market.
- Cost savings: By offering more flexibility and efficiency, Rev. 5 can lead to cost savings for CSPs, making compliance more accessible and affordable.
- Alignment with industry standards: FedRAMP Rev 5 aligns more closely with industry standards and best practices, fostering interoperability and ease of integration with existing security frameworks.
- Improved collaboration: The FedRAMP transition encourages collaboration between federal agencies and CSPs, promoting a partnership-based approach to cybersecurity and compliance.
- Continuous improvement: FedRAMP is committed to continuous improvement. Transitioning to Rev. 5 ensures that CSPs stay current with evolving security requirements, positioning them for long-term success in the federal market.
Understanding these changes and benefits is essential for any organization looking to thrive in the federal cloud space. In the following sections, we dive deep into the FedRAMP Rev 5 transition process to help you navigate it effectively.
Timeline for FedRAMP Rev 5 transition
Continuing our exploration of the transition to FedRAMP Rev 5, let’s delve into the timeline for this critical process. Timely and well-informed transitions are essential for ensuring that CSPs and federal agencies can adapt to the new framework seamlessly.
Not every organization is immediately required to transition to FedRAMP Rev 5, but for those that do, it’s imperative.
For a better understanding of the timelines applicable to organizations at different approval stages, refer to the official FedRAMP CSP Transition Plan.
According to FedRAMP, CSPs are expected to do two things:
- transition all services and components within the authorization boundary to comply with NIST SP 800-53, Rev. 5, and
- assess the impact and risks of using IaaS and PaaS services that aren’t yet FedRAMP NIST SP 800-53, Rev. 5, compliant.
To determine the correct timeline for your organization, you need to identify your current FedRAMP authorization phase. This will help you choose the appropriate timeline based on your organization’s current status.
There are three authorization phases outlined in the Rev 5 transition guide: planning, initiation, and continuous monitoring. We’ll outline each of these phases and their associated timelines below.
A. Planning phase
CSPs fall into the planning phase if any of the following apply:
- They are applying to FedRAMP or undergoing readiness review.
- They haven’t partnered with a federal agency before May 30, 2023.
- They haven’t contracted with a 3PAO for a Rev. 4 assessment before May 30, 2023.
- They have a JAB prioritization but haven’t started an assessment after the release of the Rev. 5 baseline and templates.
Timeline for the planning phase:
For organizations in the planning phase, the timeline revolves around implementing the new Rev. 5 baseline and updated FedRAMP templates. After this, you must test all new Rev. 5 controls before submitting an authorization package.
B. Initiation phase
CSPs fall into the initiation phase if any of the following apply:
- They are prioritized for the JAB and are under contract with a 3PAO or undergoing a 3PAO assessment, aiming for P-ATO package submission or have initiated the JAB P-ATO review process before May 30, 2023.
- They have partnered with a federal agency, are under contract with a 3PAO, are undergoing a 3PAO assessment, or have submitted the package for Agency ATO review before May 30, 2023.
Timeline for the initiation phase:
The timeline for organizations in the initiation phase is more complex.
- First, you need to complete ATO or JAB P-ATO using the Rev. 4 FedRAMP baseline and templates.
- Then, by September 1, 2023, or before receiving an ATO or JAB-ATO (whichever is later), you must identify the differences (delta) between your Rev. 4 implementation and Rev. 5 requirements. Plans to address these differences must be documented in the system security plans (SSP) and plans of actions and milestones (POA&M) and posted to the CSP’s package repository. It’s also essential to update plans based on “leveraged CSP information,” like shared controls.
- Finally, during the POA&M management process or the next annual assessment, assess the overall implementation of the Rev. 4 to Rev. 5 transition plan. According to FedRAMP, “implementation of the Rev. 5 controls must be completed by the next Annual Assessment to support testing of the controls implementation.”
C. Continuous monitoring phase
CSPs are in the continuous monitoring phase if they meet any of the following criteria:
- They are in continuous monitoring with a current FedRAMP authorization.
Timeline for the continuous monitoring phase:
- By September 1, 2023, CSPs in the continuous monitoring phase must “identify the delta between their current Rev. 4 implementation and the Rev. 5 requirements.” Similar to the initiation phase, this includes developing plans to address the delta, documenting those plans in the SSP and POA&M, and posting them to the CSP’s package repository.
- By October 2, 2023, organizations should also “update plans based on leveraged CSP information (e.g., shared controls).” During either the POA&M management process or the next annual assessment, businesses must assess the “implementation of the steps above.”
The timeline varies depending on when the last assessment was completed, with a maximum of one year from the date of the last assessment for some CSPs.
Official FEDRAMP REV 5 Transition Timelines
Common challenges faced during the FedRAMP Rev 5 transition
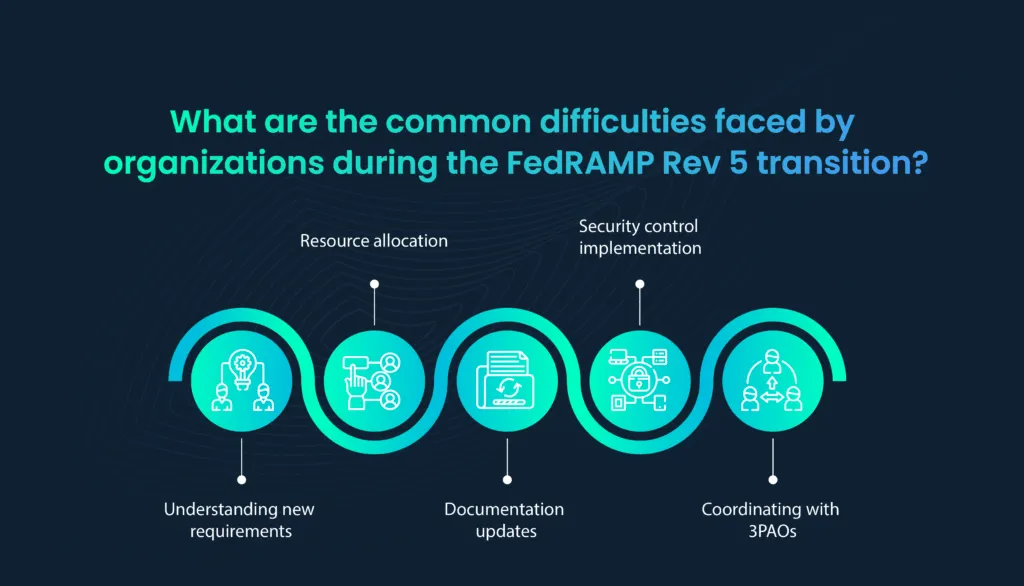
As organizations embark on the transition to FedRAMP Rev 5, they are likely to encounter various challenges and considerations. This section will highlight common challenges faced during the transition, offer mitigation strategies and best practices, discuss the role of 3PAOs, and emphasize the importance of ensuring continued compliance and security beyond the transition.
Transitioning to FedRAMP Rev 5 can pose several challenges, including:
- Understanding new requirements: The updated FedRAMP Rev 5 baselines and controls may introduce complexity and unfamiliar requirements, making it challenging for organizations to fully grasp the changes.
- Resource allocation: Adequate resource allocation, including time, personnel, and budget, can be a challenge, particularly for smaller organizations with limited resources.
- Documentation updates: Updating and maintaining comprehensive documentation to align with FedRAMP Rev 5 requirements can be time-consuming and resource-intensive.
- Security control implementation: Implementing new security controls and integrating them effectively into existing systems can be a technical challenge.
- Coordinating with 3PAOs: Coordinating with qualified 3PAOs for cloud security assessments can be logistically challenging, requiring effective communication and planning.
Key Steps to Follow During FEDRAMP REV 5 Transition
Examining the Transition Plan
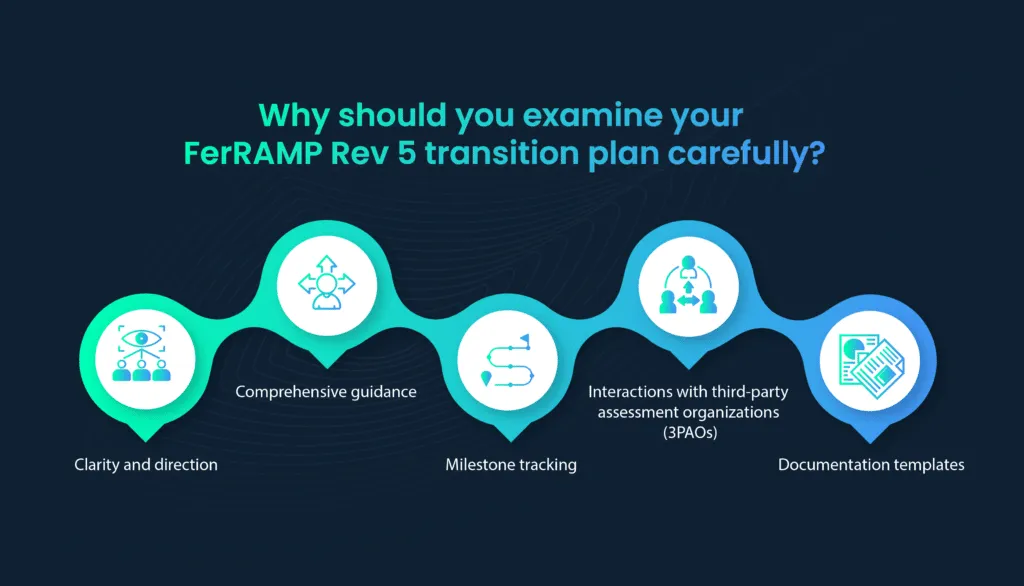
The FedRAMP-NIST Rev. 5 Transition Plan serves as a comprehensive guide for CSPs, federal agencies, and other stakeholders involved in the transition process. This plan outlines the roadmap for transitioning to Rev. 5 and provides detailed insights into the transition’s intricacies.
Examining this plan is of utmost importance for several reasons:
- Clarity and direction: The Transition Plan offers clarity on the transition process, helping organizations understand what is expected at each stage. It provides a structured framework to follow.
- Comprehensive guidance: It offers detailed guidance on security controls, documentation requirements, and assessment procedures specific to Rev. 5. This guidance is invaluable for CSPs working to align their services with the new FedRAMP Rev 5 baseline.
- Milestone tracking: The plan should include milestones and deadlines, enabling organizations to track their progress and ensure they meet critical transition milestones within the specified timeframe.
- Interactions with third-party assessment organizations (3PAOs): CSPs can find information on how to engage with third-party assessment organizations (3PAOs) for cloud security assessments and audits, a crucial aspect of the transition.
- Documentation templates: The Transition Plan often includes templates and examples for updated documentation, making it easier for CSPs to create the necessary artifacts required for Rev. 5 compliance.
Implementation Best Practices
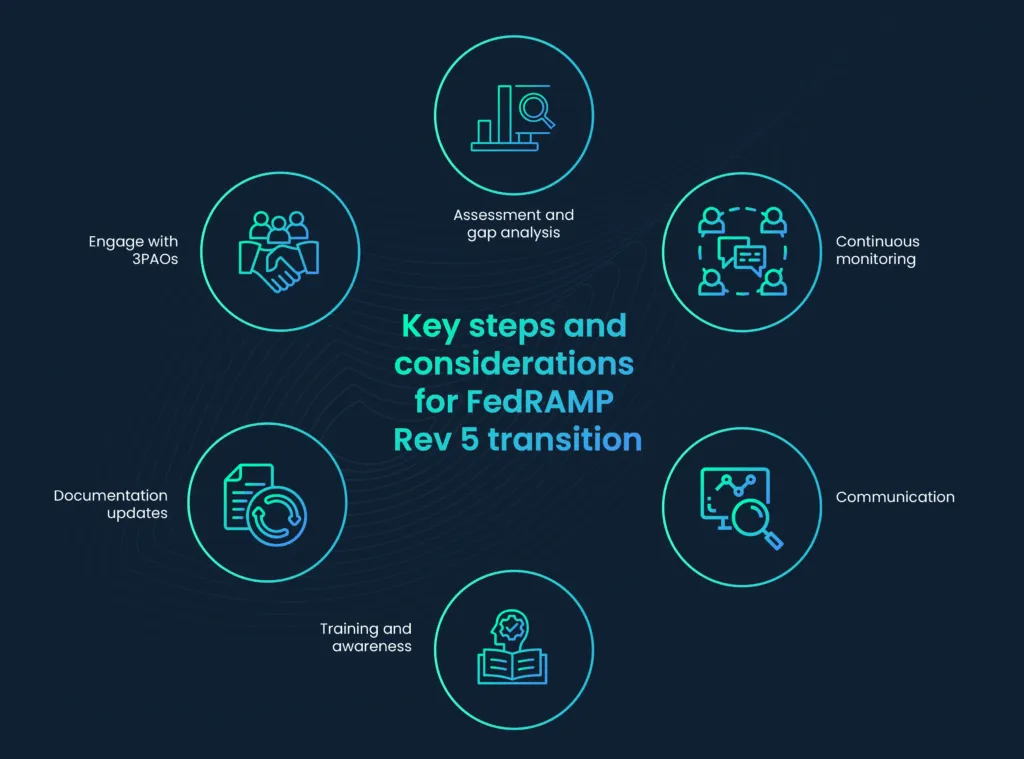
As organizations embark on their transition journey to FedRAMP Rev 5, there are key steps and considerations to keep in mind:
- Assessment and gap analysis: Begin by conducting a thorough assessment of your existing security controls and documentation. Identify gaps and areas where adjustments are needed to align with Rev. 5 requirements.
- Engage with 3PAOs: Select a qualified 3PAO to conduct security assessments and audits. Ensure a clear understanding of expectations and timelines for these assessments.
- Documentation updates: Revise and update your security documentation, including security plans, system security documentation, and any other relevant artifacts, to align with Rev. 5 requirements.
- Training and awareness: Ensure that your team is trained and aware of the new security controls and requirements introduced in Rev. 5. This is crucial for maintaining a compliant environment.
- Continuous monitoring: Establish a robust continuous monitoring process to proactively identify and address security vulnerabilities and compliance issues post-transition.
- Communication: Maintain open and transparent communication with federal agencies and FedRAMP officials throughout the transition process. Address any inquiries or clarifications promptly.
A well-executed transition plan is vital for achieving FedRAMP Rev 5 compliance efficiently and effectively. It reduces the risk of disruptions to service and ensures that organizations can continue to provide secure and compliant cloud services to federal agencies.
In the upcoming sections, we will explore the nuances of navigating the FedRAMP Rev 5 baselines and provide practical tips for compliance.
Navigating the FedRAMP Rev 5 Baselines
Security baselines are the foundation of FedRAMP compliance. They represent a predefined set of security controls and requirements that CSPs must adhere to when offering cloud services to federal agencies.
These FedRAMP Rev 5 baselines are designed to establish a consistent and high level of security across the federal government’s cloud environment. They encompass various security domains, including access control, data protection, and incident response, among others.
Key differences between Rev 4 and Rev 5 baselines
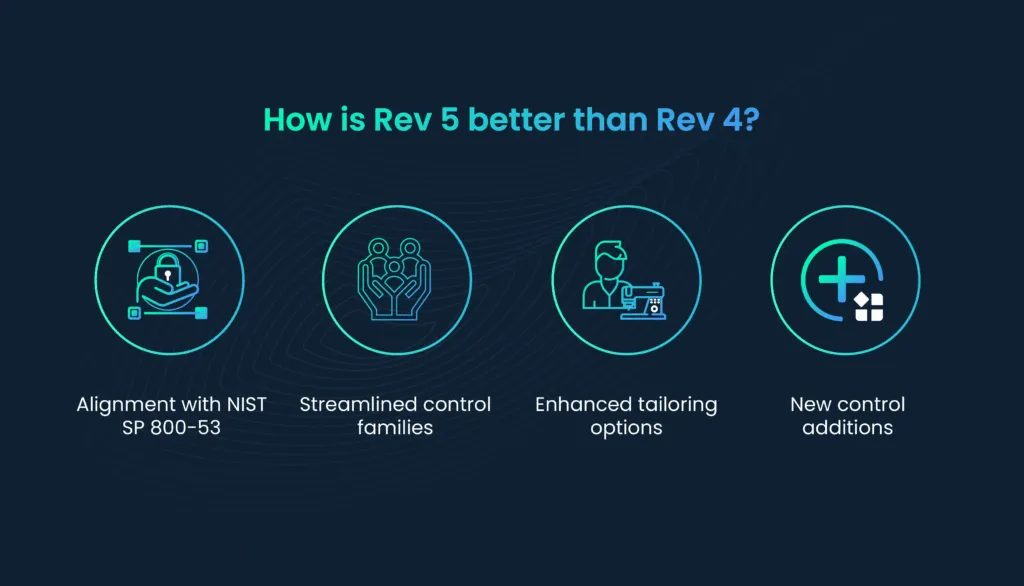
The transition to Rev 5 introduces several notable differences and updates to the security baselines:
- Alignment with NIST SP 800-53: FedRAMP Rev 5 aligns more closely with the latest version of NIST Special Publication 800-53, offering a more robust and comprehensive set of security controls.
- Streamlined control families: Some control families have been streamlined or restructured in Rev. 5 to improve clarity and relevance. CSPs should review these changes carefully.
- Enhanced tailoring options: Rev. 5 provides greater flexibility in tailoring security controls to match the specific security needs of a cloud service. This allows CSPs to implement controls that are more proportionate to the risks they manage.
- New control additions: New controls have been introduced in Rev. 5 to address emerging threats and vulnerabilities. CSPs must understand and incorporate these controls into their security strategy.
Impact of FedRAMP Rev 5 on existing and new CSPs
The transition to Rev. 5 has differing impacts on existing and new CSPs:
- Existing CSPs: Existing CSPs must evaluate their current security posture and identify gaps in compliance with the FedRAMP Rev 5 baselines. They should plan to update their security documentation, conduct assessments, and make necessary adjustments to meet the new requirements.
- New CSPs: New CSPs entering the federal market will start their journey with the FedRAMP Rev 5 baselines. They have the advantage of building their security programs around the latest requirements from the outset, potentially streamlining the compliance process.
Ensuring continued compliance and security beyond the transition
Achieving FedRAMP Rev 5 compliance is a milestone, but it’s essential to focus on ongoing efforts to maintain compliance and security:
- Establish a robust continuous monitoring program to continuously assess, identify, and mitigate security risks.
- Stay informed about evolving security threats and vulnerabilities and adapt security measures accordingly.
- Regularly update and review documentation to ensure it accurately reflects your security posture.
- Foster a culture of security awareness and training among your staff and stakeholders.
One should not forget that compliance is continuous, and maintaining a proactive security stance is vital for long-term success.
By recognizing and addressing common challenges, implementing mitigation strategies, collaborating with 3PAOs effectively, and focusing on continued compliance and security, organizations can navigate the complexities of the transition to FedRAMP Rev 5 with confidence and resilience.
How can Scrut help you in FedRAMP Rev 5?
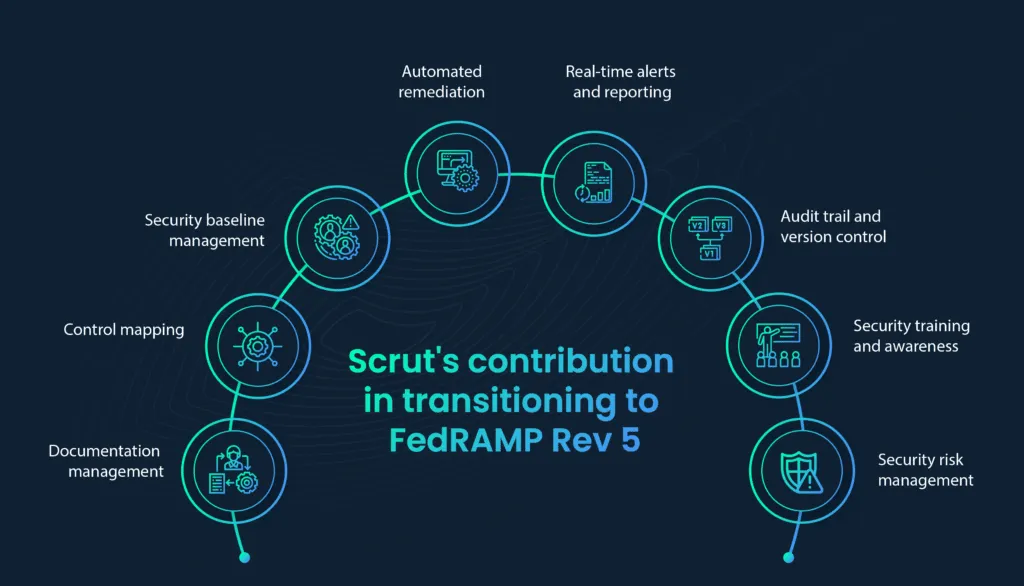
Scrut can play a significant role in helping organizations achieve and maintain FedRAMP compliance. Here are several ways in which Scrut can assist with FedRAMP compliance efforts:
A. Documentation management
FedRAMP requires extensive documentation, including SSPs, POA&M, and security control assessments. Scrut can streamline the creation, management, and storage of these documents, ensuring they are up-to-date and readily accessible during audits.
B. Control mapping
It can help organizations map their existing security controls and practices to the specific FedRAMP requirements. This mapping simplifies the process of identifying gaps and addressing them to meet FedRAMP standards.
C. Security baseline management
FedRAMP requirements can evolve over time. Compliance tools can help organizations keep up with changes by providing updated security baselines and templates that align with the latest FedRAMP standards.
D. Automated remediation
When compliance violations or security vulnerabilities are identified, Scrut experts can automate the remediation process by providing guidance on how to address issues and track progress until they are resolved.
E. Real-time alerts and reporting
Scrut can generate real-time alerts when non-compliance issues are detected or when changes in the environment may impact security. It also offers robust reporting capabilities, which are invaluable during audits and assessments.
F. Audit trail and version control
Maintaining an audit trail and version control of security policies, procedures, and configurations is crucial for FedRAMP compliance. Scrut can ensure that all changes are tracked, logged, and can be easily reviewed.
G. Security training and awareness
FedRAMP compliance includes requirements for security training and awareness programs for employees. Scrut can help manage and track employee training and awareness efforts with ease and flexibility.
H. Security risk management
Scrut can assist organizations in identifying, assessing, and managing security risks. It can provide risk assessment frameworks and support risk mitigation strategies.
Ready to simplify your FedRAMP Rev 5 compliance? Contact Scrut today and let our experts streamline your transition effortlessly. Elevate your compliance game with Scrut now.
Summing up
Achieving FedRAMP Rev 5 compliance is an achievement, but it’s imperative to prioritize ongoing efforts to uphold compliance and security. This involves establishing a robust continuous monitoring program to consistently assess, identify, and mitigate security risks. Staying vigilant and informed about evolving security threats and vulnerabilities is essential, allowing you to adapt security measures accordingly. Regularly updating and reviewing documentation ensures that it accurately reflects your security posture. Additionally, fostering a culture of security awareness and providing training to staff and stakeholders is crucial.
It’s vital to remember that compliance is a continuous commitment, and maintaining a proactive security stance is essential for long-term success. By recognizing and addressing common challenges, implementing effective mitigation strategies, collaborating effectively with 3PAOs, and maintaining a strong focus on ongoing compliance and security, organizations can confidently navigate the complexities of the transition to FedRAMP Rev 5 with resilience.
FAQs
1. What is FedRAMP, and why is it significant?
FedRAMP stands for the Federal Risk and Authorization Management Program. It’s crucial because it ensures the security and compliance of cloud services used by U.S. federal agencies, modernizing government IT systems while maintaining high cybersecurity standards.
2. What are the key changes introduced in FedRAMP Rev 5?
FedRAMP Rev 5 brings significant updates, including revised security baselines, enhanced flexibility for cloud service providers (CSPs), a streamlined authorization process, and alignment with NIST SP 800-53 standards.
3. How does Rev. 5 benefit CSPs and federal agencies?
Rev. 5 benefits CSPs by offering more flexibility, faster authorization, and alignment with industry standards, making compliance more accessible. Federal agencies benefit from enhanced security and interoperability.
4. What role do 3PAOs play in the transition process?
3PAOs play a critical role in conducting independent security assessments and audits to verify FedRAMP compliance. They provide expert guidance and recommendations and ensure objectivity in assessments.
5. Why is FedRAMP Rev 5’s alignment with NIST SP 800-53 significant?
Alignment with NIST SP 800-53 ensures that security controls are in line with industry best practices, enhancing the rigor and comprehensiveness of security measures and promoting stronger cybersecurity.
Table of contents


















