Choose risk-first compliance that’s always on, built for you.
Go back to blogs
What is CSPM? Everything You Need to Know in 2023
Last updated on
January 20, 2025
26
min. read

The rise of cloud computing has transformed the way businesses operate by providing increased flexibility, scalability, and cost savings.
However, with the increased adoption of cloud infrastructure and services, there has been a significant increase in security risks.
This has led to the development of cloud security tools such as Cloud Security Posture Management (CSPM). In fact, CSPM has become an essential aspect of securing cloud-based environments these days.
In this guide, we will provide you with all the information you need to know about CSPM in 2023. We will cover the basics of CSPM, including its definition, benefits, and capabilities. We will also compare CSPM with other cloud security solutions and factors to consider when choosing a CSPM solution.
By the end of this guide, you will have a solid understanding of CSPM and how it can help to secure your cloud infrastructure.
What is CSPM?

CSPM is a security solution that provides visibility into the security posture of cloud infrastructure and services.
It helps organizations identify and remediate security vulnerabilities, misconfigurations, and compliance violations across multiple cloud platforms.
CSPM solutions automatically check the cloud environment to identify and mitigate security and compliance risks. Furthermore, they also continuously monitor gaps in security policy enforcement.
Simply put, a CSPM solution can give you the assurance that your cloud services are implemented/configured according to industry best practices.
How does CSPM work?
CSPM solutions basically solve the issue of visibility in a cloud environment.
At a high level, CSPM scans and analyzes cloud services such as IaaS, PaaS, and SaaS on a regular basis. The scan frequency depends on the CSPM solution used and often is configurable.
CSPM provides visibility into cloud assets and configurations — knowing what assets exist and where they are located — which is a significant challenge for many cloud-based companies. It assists organizations in automatically detecting activity related to metadata, misconfigurations, network, security changes, and the extent of the attack surface.
A CSPM tool is capable of comparing cloud application configurations to industry compliance frameworks like HIPAA, PCI DSS, GDPR, etc., allowing any violations to be quickly identified and remedied.
To get a better understanding of how a CSPM tool works, let’s do a deeper dive and dissect the features and functions offered by it. With that in mind, let us look at how Scrut CSPM works.

- Connect cloud platform: Scrut CSPM integrates cloud security with your cloud platforms using pre-built integrations, which take less than 10 minutes to integrate.
- Customize controls: You can use the preconfigured CIS benchmarks or add custom controls. These controls are mapped to the compliance frameworks you want to adhere to, through pre-built mapping.
- Monitor cloud security: Scrut’s user-friendly dashboard allows you to keep track of your cloud security posture, misconfigurations, and the status of corrective actions.
- Remediation tasks: You can create, assign, and track remediation tasks.
Through real-time risk detection, Scrut continuously monitors cloud environments for potentially malicious activity and unauthorized access events.
Scrut CSPM tool integrates with DevSecOps, DevOps, or SecOps tools like Crowdstrike and Synk, making it easier to adopt new cloud security archetypes.
CSPM tools, as an agentless solution based on Software as a Service, implement the CSPM concepts discussed above regarding visibility, configuration, compliance, and ongoing cloud environment management. In doing so, they essentially provide cloud governance, risk management, and compliance (GRC) capabilities.
Why is CSPM important?
The recent rise in cloud adoption has created new security challenges for most organizations today. Unlike the on-prem world, the nature of the cloud environment is different.
- There is a lack of a definite perimeter to protect
- Cloud is dynamic and periodic checks are not sufficient
- Due to the lack of centralization, it is difficult to know what is happening inside the cloud
The two key challenges unique to cloud security are:
- Complexity: The majority of cloud providers offer a diverse range of services including computing, storage, databases, analytics, networking, security, and much more. There are dozens of unique settings and granular configurations in each of them, making it difficult to ensure that organizations meet compliance and security requirements.
- Lack of Visibility: Developers can now deploy new servers in the cloud without dealing with the complications associated with on-premise deployments, such as provisioning and budgeting. InfoSec teams, on the other hand, might be unaware of all the instances that are being spun up.
Both these challenges lead to misconfigurations in the cloud.
What are cloud misconfigurations and how do they occur?
Cloud misconfigurations are mistakes made during the setup or ongoing management of a cloud computing system that leaves it vulnerable to attack.
A cloud misconfiguration occurs when proper controls for applications, containers, infrastructure, and other software components are not implemented.
Misconfigurations are common in cloud environments and happen often by accident. According to a report by Synk.io, cloud misconfigurations account for almost half (45%) of data breaches in the cloud.
Furthermore, the share of data breaches due to misconfiguration will only increase in the future. According to a Gartner estimate, by 2025, more than 99% of cloud breaches will be due to misconfigurations.
Capital One was a high-profile example of cloud misconfigurations that resulted in real-world losses. A hacker exploited a flaw in the company’s cloud-based firewall to steal information from 100 million credit applicants and active cardholders.
These are just a couple of cloud misconfiguration examples. Today, cloud misconfigurations can take many forms such as:
- Failing to properly secure access to cloud data and services, such as using weak passwords or leaving open ports that should be closed.
- Leaving data or services exposed to the public internet when they should be behind a firewall or other security measures.
- Using outdated or unpatched software that is vulnerable to attack.
- Failing to properly configure logging and monitoring systems that can detect and alert administrators to potential threats.
Such cloud misconfigurations can occur for many different reasons. Some of these reasons mainly include:

- Lack of knowledge or expertise — Cloud computing is a complex field, and many organizations lack the expertise needed to properly set up and manage cloud systems. This can lead to mistakes that leave the system vulnerable to attack.
- Rushing to deploy — In many cases, organizations are under pressure to deploy cloud systems quickly in order to meet business needs. This can lead to shortcuts being taken or important security measures being overlooked.
- Complexity — Cloud systems can be incredibly complex as they have many moving parts and dependencies. This complexity can make it difficult to properly configure the system, leading to misconfigurations.
- Human error — Even with the best of intentions, humans can make mistakes. In a complex cloud system, even a small mistake can have major security implications.
Since eliminating misconfigurations is not possible entirely, organizations retort to finding them once they occur. CSPM solutions help cloud users identify and resolve these misconfigurations.
What is the role of CSPM in preventing cloud misconfigurations?
As you’ve learned, cloud misconfigurations can pose a serious risk that could end up in hefty financial losses and sometimes even legal issues.
Fortunately, CSPM can help prevent these misconfigurations from occurring in the first place.
To elaborate, CSPM can provide organizations with the tools and processes needed to monitor and manage the security of their cloud systems.
Some of the ways that CSPM can help prevent cloud misconfigurations include:
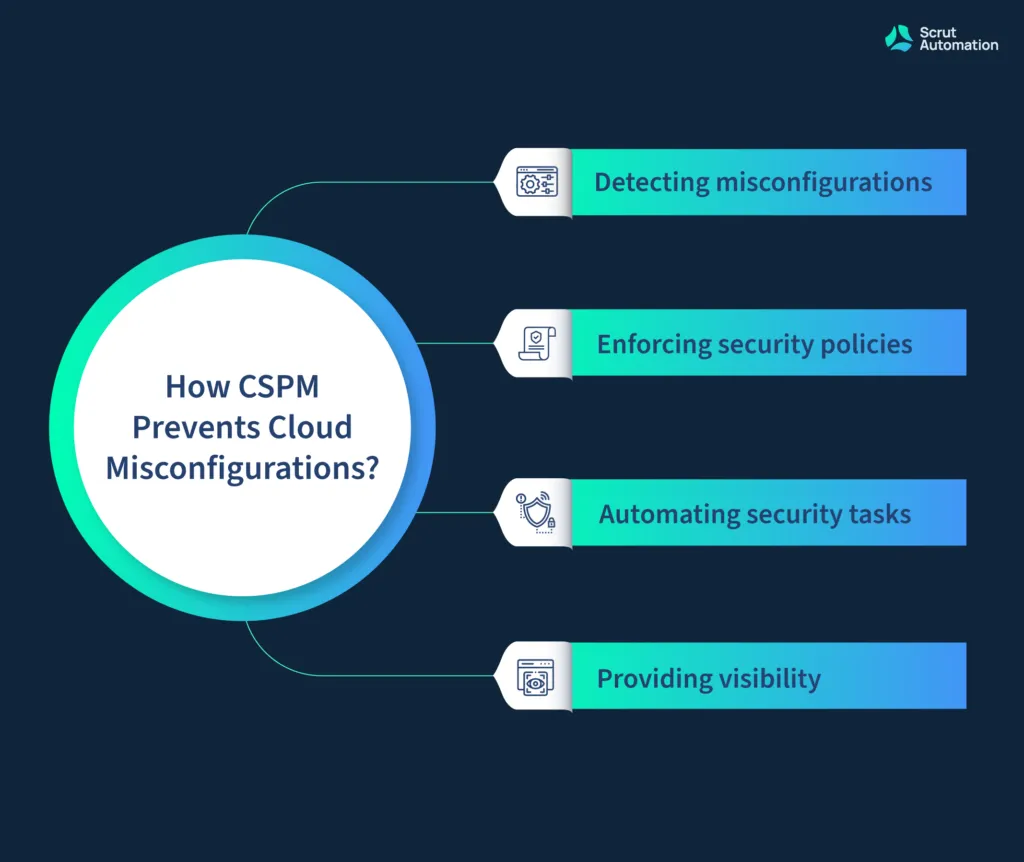
- Detecting misconfigurations — CSPM tools can be used to scan cloud systems for misconfigurations, such as open ports, weak passwords, and unsecured data. This can help organizations identify and address potential security risks before they can be exploited by attackers.
- Enforcing security policies — CSPM tools can be used to enforce security policies, such as access control policies and data encryption policies. As a result, it can prevent misconfigurations caused by human error or other factors.
- Automating security tasks — CSPM tools can be used to automate security tasks, such as patch management and vulnerability scanning. Thanks to this, organizations can ensure that cloud systems are always up-to-date and secure.
- Providing visibility — CSPM tools can provide organizations with visibility into the security of their cloud systems, including details about misconfigurations, vulnerabilities, and other security risks. This enables organizations to make informed decisions about how to improve the security of their cloud systems.
Overall, CSPM is most certainly a must-have tool for cloud misconfigurations and other security risks in your organization.
Cloud services covered by CSPM
As you may already know, there are three types of cloud services including IaaS, PaaS, and SaaS, and the CSPM solution covers all of them.
Let’s understand how CSPM covers each cloud service in detail.
- IaaS (Infrastructure as a Service) — IaaS is a cloud computing service that provides virtualized computing resources, such as servers, storage, and networking, over the internet. CSPM solutions for IaaS can help organizations monitor and manage the security of their cloud infrastructure, including virtual machines, storage buckets, and network configurations.
- PaaS (Platform as a Service) — PaaS is a cloud computing service that provides a platform for building, deploying, and managing applications over the Internet. CSPM solutions can help organizations using PaaS to monitor and manage the security of their cloud platforms, including web applications, databases, and development tools.
- SaaS (Software as a Service) — SaaS is a cloud computing service that provides access to software applications over the internet. CSPM solutions can also help organizations using multiple SaaS applications by monitoring and managing the security of their cloud applications, including email services, collaboration tools, and customer relationship management systems.
An important note: CSPM solutions do not cover the underlying PaaS and IaaS used by a SaaS since the responsibility for their security lies with the SaaS provider. However, some SaaS applications may allow customers to configure certain details of the PaaS and IaaS components.
Benefits of CSPM
Let’s now discuss the key benefits of CSPM tools.
A Gartner research found that CSPM implementations can reduce cloud security incidents caused by misconfigurations by up to 80%. CSPM solutions allow you to continuously monitor dynamic cloud environments and identify discrepancies between your security posture and policies.
- One place for visibility of cloud security. With CSPM tools, you get centralized visibility across a multi-cloud environment. They help you identify, assess, and manage risks across all your cloud resources. This is a more efficient approach than conducting assessments separately for each cloud account or resource. A comprehensive CSPM solution provides visibility into many aspects of your environment. This visibility includes:
- Inventory across all your cloud environments
- Cloud resources not adhering to the security policies
- Accounts’ permissions
- Accounts with no multi-factor authentication
- Unencrypted databases
- Helps you comply with security and privacy frameworks: As we discussed in the previous section, companies need to comply with different regulations and standards depending on the geographies they operate in and their industry type. This helps your customers, employees, partners, and government authorities know that you will keep their data secure. CSPM tools help you maintain a strong compliance posture. As CSPM solution continuously monitors your cloud environment, they will notify you if there are any deviations from the compliance requirements.
- Manage risks in your cloud environment. CSPM tools use real-time risk detection to identify risks in an organization’s security posture. Some cloud security tools like Scrut classify them according to their severity. This helps you significantly alleviate the pain of alert fatigue. Security teams already receive thousands of alerts that make it impossible to work on all the issues. A CSPM tool gives context on the risks to prioritize which issues to work on first. For example, a public Amazon S3 bucket (logical container) is considered a high priority because it could result in a major data leak. Meanwhile, an S3 bucket that can be accessed by multiple users but is not accessible to the public via the Internet would be categorized as a lower priority. It’s a risk that the team should look into because it could be a case where the least privilege isn’t being followed. But it’s not as serious as the risk that could expose data to anyone on the Internet.
- Reduce DevOps challenges in your organization. With a CSPM solution, your DevOps team can proactively monitor and manage your cloud resources to ensure they are configured securely and in compliance with industry best practices and regulatory requirements. Furthermore, a CSPM solution can also help reduce the workload on your DevOps team, freeing them up to focus on other tasks that are critical to your organization’s success by automating many of the processes involved in cloud security management. This can be especially valuable for organizations that are struggling to keep up with the demands of a rapidly evolving technology landscape. Additionally, a CSPM solution can help foster collaboration between your DevOps and security teams by providing a single platform for managing and monitoring cloud security. This can help ensure that all stakeholders are on the same page when it comes to security and compliance and can help prevent security gaps or misconfigurations that could lead to security incidents.
Capabilities of CSPM
Now that you’ve learned about the CSPM benefits, let’s explore the various capabilities of CSPM solutions and how they can help your organization manage its cloud security.
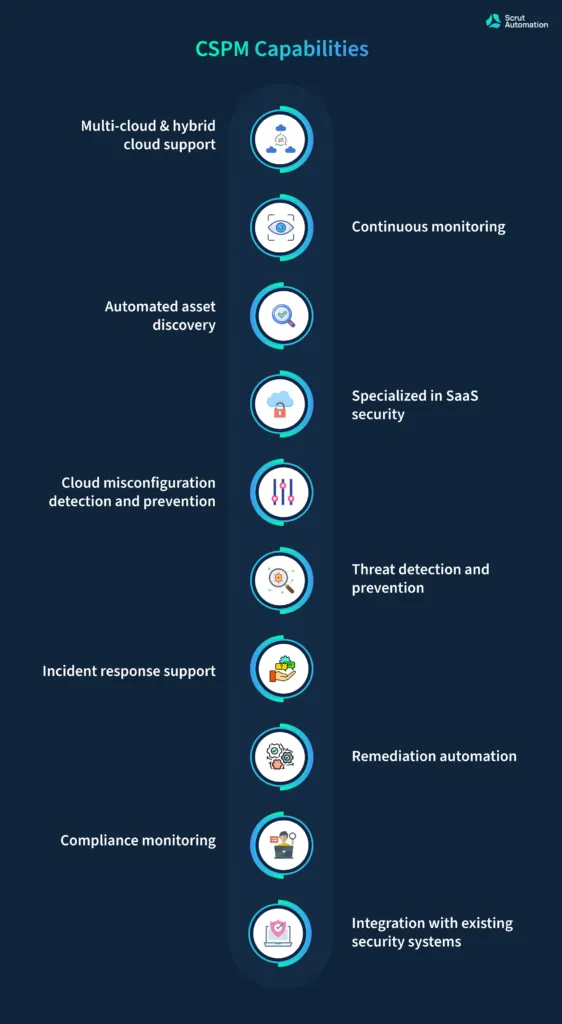
- Multi-cloud & hybrid cloud support – If your organization is leveraging multiple cloud providers or a hybrid cloud environment to meet your business needs, you must consider investing in a CSPM solution with multi-cloud and hybrid cloud support. Such a CSPM solution can provide you with a unified view of your cloud resources across multiple clouds as well as environments. This, in turn, can let you monitor & manage your cloud security from a single dashboard, giving your organization greater visibility and control over your entire cloud infrastructure.
- Continuous monitoring – CSPM solutions offer continuous monitoring of your cloud resources to ensure that they are configured securely and in compliance with industry standards and regulatory requirements. Simply put, by providing real-time alerts for any security misconfigurations, vulnerabilities, or compliance violations, CSPM solutions help you identify and mitigate security risks before they can be exploited by attackers.
- Automated asset discovery – Given the dynamic nature of cloud environments, most organizations find it challenging to keep track of all their resources in their cloud infrastructure. But a CSPM solution with automated asset discovery capabilities can help by automatically identifying all your cloud assets and their configurations. As a result, you can ensure that all your cloud resources are secure as well as in compliance with necessary regulatory requirements.
- Specialized in SaaS security – Software-as-a-Service (SaaS) applications have become an integral part of many organizations’ operations across the world. CSPM solutions with specialized SaaS security capabilities can help you monitor and manage the security of your SaaS applications, including identifying misconfigurations, vulnerabilities, and compliance violations.
- Cloud misconfiguration detection and prevention – As mentioned earlier, misconfigured cloud resources can lead to security incidents, data breaches, and other issues that can compromise your organization’s security posture. CSPM solutions can help detect and prevent misconfigurations by identifying security gaps and providing recommendations for how to remediate them.
- Threat detection and prevention – CSPM solutions can help you detect and prevent threats by monitoring your cloud resources for suspicious activities, such as unauthorized access or data exfiltration. Plus, they also send you real-time alerts and automated responses, which can help you quickly respond to threats and prevent them from causing irreversible damage to your organization.
- Incident response support – In the event of a security incident, a CSPM solution can provide incident response support by providing real-time alerts, contextual information about the incident, and automated responses to mitigate the impact of the incident. This can help you minimize the damage caused by the incident and ensure that your organization is back up and running as quickly as possible.
- Remediation automation – Many CSPM solutions can automate the remediation of security issues, reducing the workload on your security and DevOps teams. Not only that but organizations can even provide automated recommendations for how to remediate certain security issues and begin the remediation process automatically. As a result, it can save you a lot of time and effort required to maintain a secure cloud infrastructure.
- Compliance monitoring – Many organizations operate in regulated industries that require them to meet specific compliance requirements, such as HIPAA, PCI-DSS, or GDPR. A CSPM solution can help you monitor your cloud infrastructure for compliance violations and provide recommendations for how to remediate them.
- Integration with existing security systems – CSPM solutions can integrate with your existing security systems like SIEM, CASB, CWPP, and more. This enables security teams to have a centralized view of their security posture and to leverage their existing tools and processes for threat detection, incident response, and remediation. CSPM solutions offer a comprehensive set of capabilities to help organizations monitor and manage their cloud security posture. So by leveraging CSPM solutions, every organization can proactively detect and prevent misconfigurations, threats, and compliance violations, and ensure the security and resilience of their cloud environment.
Which types of organizations would benefit from CSPM solutions?
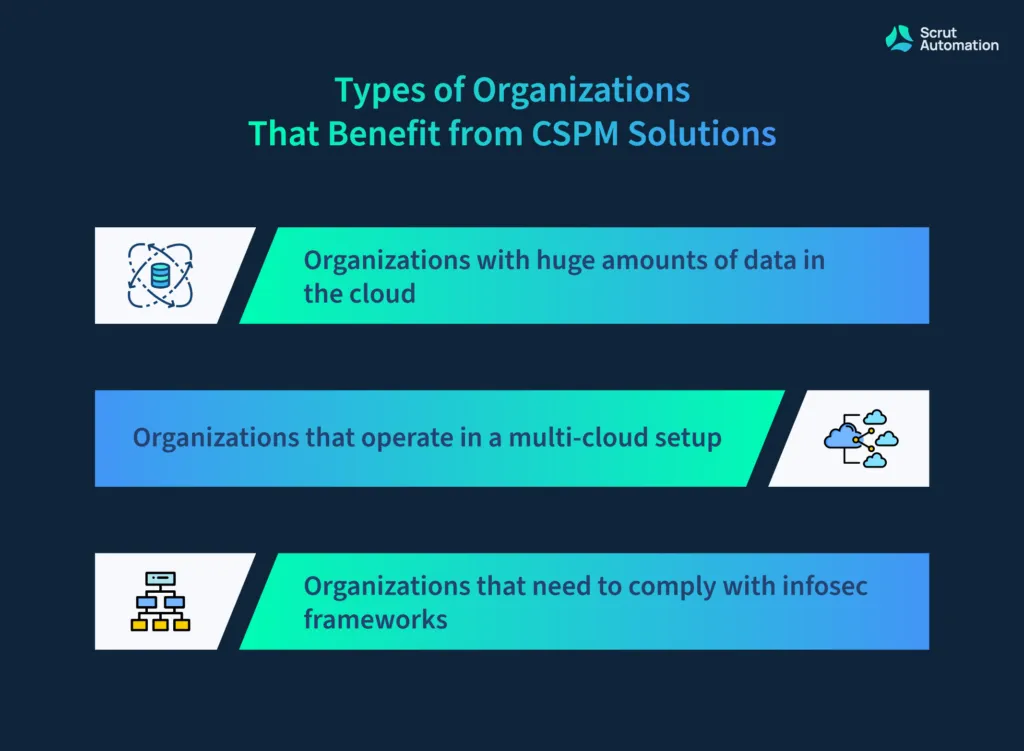
Any organization using cloud services can benefit from it. However, CSPM is best suited for the following three types of organizations:
1. Organizations with huge amounts of data in the cloud – The more data you have in your cloud, the more important asset it becomes for you. Simultaneously, it also becomes a lucrative target for attackers. Furthermore, this growth in data — and consequently growth in users — implies higher fines in case of data breaches.
Hence, organizations with a huge amount of data in the cloud can get significant gains by using a CSPM solution. CSPM tool can ensure that all of your resources are protected and that extra security efforts are focused on critical workloads.
2. Organizations that operate in a multi-cloud setup – Nowadays, organizations are adopting a multi-cloud strategy. This strategy is becoming common for several reasons, such as to avoid vendor lock-ins and for leveraging the unique and cost-efficient services offered by different cloud service providers.
However, multiple-cloud accounts increase the likelihood of misconfigurations. This is due to a lack of standardization in cloud services across different providers, making these cloud environments very complex. And consequently difficult to track. Additionally, cloud services and security best practices are constantly evolving, making it difficult to comply with the security guidelines from the security providers.
CSPM solutions solve these issues by monitoring cloud services across thousands of services automatically, no matter how complex the cloud environment is.
According to Gartner, 81% of organizations are using more than one cloud provider. This means the majority of organizations using cloud services will benefit from CSPM solutions.
3. Organizations that need to comply with infosec frameworks – CSPM solutions help in ensuring compliance with security and privacy frameworks by assisting you in auditing your cloud resources and demonstrating compliance with the required frameworks.
These frameworks may be in the form of laws and regulations like CCPA, HIPAA, and GDPR or voluntary standards like SOC 2 and ISO 27001. These tools also alert you if there are any deviations from compliance requirements.
Suppose your company operates in a regulated industry, such as healthcare or finance. In that case, you must adhere to specific regulatory standards such as HIPAA/HITECH and PCI DSS, as well as infosec frameworks such as SOC 2 and ISO 27001.
You may consider implementing a CSPM system to ensure that your cloud security standards and security posture meet regulatory compliance.
How does CSPM stack up against other cloud security tools?
With so many cloud security tools available in the market today, it can be confusing to know where CSPM fits in the overall cloud security tech stack.
To help you make an informed decision, we have compared CSPM with all major cloud security tools below.
CSPM Vs CASB
Cloud Access Security Brokers (CASBs) are security tools that help organizations secure data and applications that are stored in the cloud. They are mainly focused on securing access to cloud applications, whether they’re hosted in the public cloud or in a private data center.
While CASB solutions are great for managing user access and preventing data loss, they don’t provide the same level of visibility and control over cloud infrastructure as CSPM.
CSPM Vs CWPP
Cloud Workload Protection Platforms (CWPPs) are designed to protect cloud-based applications and workloads from cyber threats. They offer a range of capabilities, including vulnerability management, intrusion prevention, and compliance monitoring.
However, like CASBs, CWPPs focus primarily on securing applications and workloads, whereas CSPM focuses on securing the underlying cloud infrastructure.
In short, CSPM is critical for ensuring that the infrastructure is secure, which is a fundamental requirement for any cloud-based application or workload.
CSPM Vs CIEM
Another cloud security tool to compare with CSPM is Cloud Infrastructure Entitlement Management (CIEM). They offer a range of capabilities, including identity and access management, policy management, and auditing.
While CIEM tools are essential for managing access to cloud resources, they do not address misconfigurations or other security issues that can arise when deploying cloud infrastructure.
CSPM, on the other hand, is specifically designed to address these issues and ensure that cloud infrastructure is configured correctly.
CSPM Vs CNAPP
Cloud Native Application Protection Platform (CNAPP) is a tool that provides security for cloud-native applications. CNAPPs focus on securing containerized applications by providing runtime protection, vulnerability management, and compliance monitoring.
CSPM, on the other hand, focuses on the security posture of cloud resources. It provides visibility into the security posture of the underlying cloud infrastructure, such as network configuration and storage permissions.
CSPM Vs CAASM
Both CSPM and CAASM (Cyber Asset Attack Surface Management) tools provide comprehensive security for cloud environments. But they have some notable differences. CSPM is primarily focused on securing the infrastructure of cloud environments.
On the other hand, CAASM is designed to manage and secure the cyber asset attack surface of cloud environments. It provides a comprehensive view of all assets in the cloud, including applications, infrastructure, and data. CAASM then analyzes this data to identify potential attack vectors and provide recommendations for risk reduction.
All in all, CSPM is ideal for organizations that need to secure their cloud infrastructure quickly and effectively, while CAASM is better suited for organizations that require a more comprehensive view of their entire cloud environment.
How to choose a CSPM solution for your organization: 5 factors to consider
With so many CSPM solutions available, choosing the right one for your organization can be a daunting task.
To help you make the right decision, we’ve shared the five most important factors to consider when selecting a CSPM solution for your organization.
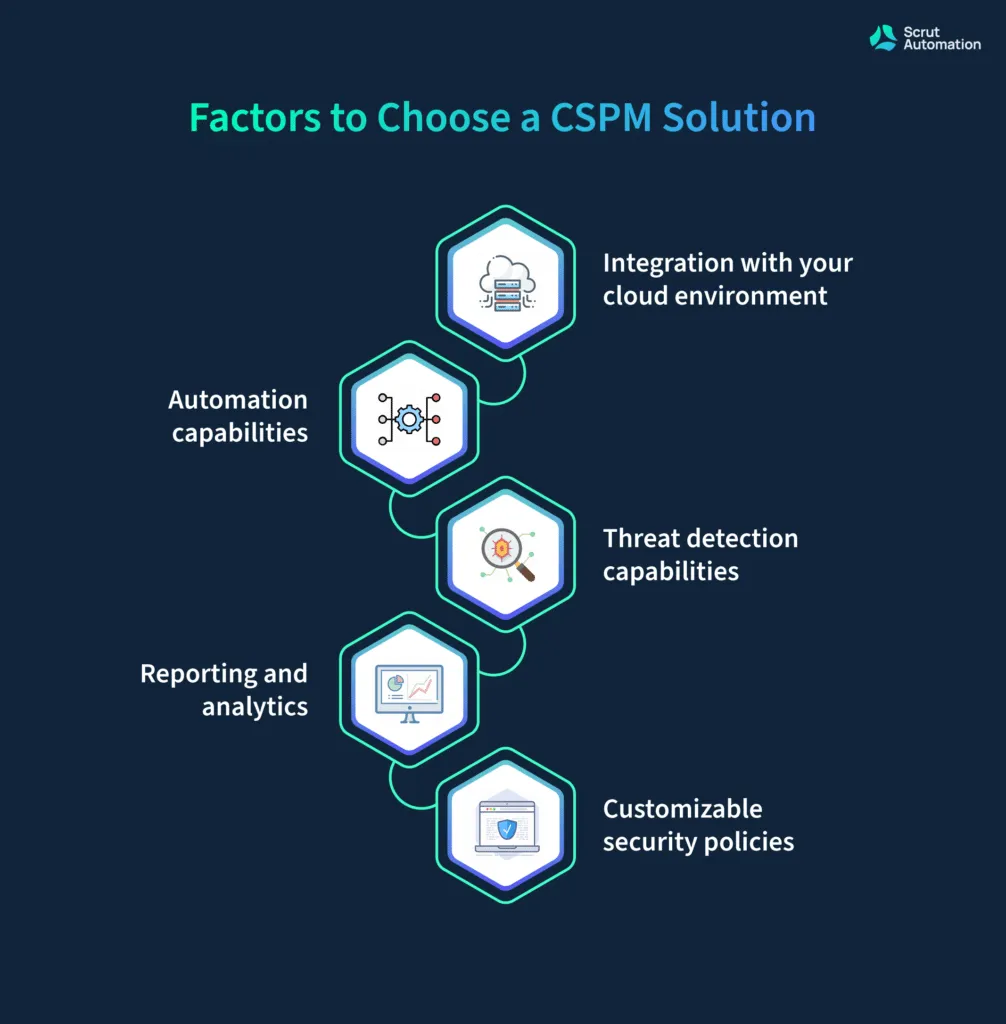
Factor #1. Integration with your cloud environment
One of the most critical factors to consider when choosing a CSPM solution is its ability to integrate with your existing cloud environment. Whether you’re using public, private, or hybrid clouds, you need a CSPM solution that can seamlessly integrate with your infrastructure.
When evaluating CSPM solutions, look for those that offer APIs, multi-cloud support, and native cloud integrations. APIs allow your CSPM solution to integrate with your existing cloud services, enabling you to access data and configuration information easily.
Multi-cloud support is essential for organizations that use multiple cloud providers, while native cloud integrations allow for more straightforward deployment and management of the CSPM solution.
Factor #2. Automation capabilities
Automation can significantly streamline CSPM processes, saving time and resources. When evaluating CSPM solutions, look for those that offer automation capabilities such as continuous monitoring, automated remediation, and security policy enforcement.
Continuous monitoring allows for real-time monitoring of your cloud environment, while automated remediation automatically corrects any security issues that are detected. Security policy enforcement ensures that your organization’s security policies are being adhered to, reducing the risk of security breaches.
However, when evaluating the automation capabilities of CSPM solutions, make sure to consider the level of customization and ease of use as well.
Factor #3. Customizable security policies
Customizable security policies are essential for meeting your organization’s specific security needs and compliance requirements. CSPM solutions can offer different types of security policies such as compliance checks, configuration assessments, and risk prioritization.
When evaluating CSPM solutions, look for those that offer policy flexibility, policy customization, and policy enforcement. The ability to customize policies allows for greater flexibility in meeting your organization’s specific security needs.
Policy enforcement ensures that policies are being adhered to, while policy customization allows for the creation of policies that meet specific security requirements.
Factor #4. Threat detection capabilities
Threat detection capabilities are critical for identifying and responding to security threats in real time.
CSPM solutions can offer different types of threat detection capabilities, such as anomaly detection, threat intelligence, and incident response.
When evaluating CSPM solutions, consider the level of threat visibility, the ability to detect new and emerging threats, and the speed of threat response.
Factor #5. Reporting and analytics
Reporting and analytics are essential for monitoring and improving your organization’s cloud security posture.
Different CSPM solutions come with different reporting and analytics features like dashboards, compliance reports, and risk assessment reports to name a few.
Ideally, you should consider a CSPM solution that has the ability to track progress over time, and the ease of reporting.
The ability to track progress over time allows for monitoring the effectiveness of security measures, while the ease of reporting allows for simplified reporting to management and stakeholders.
Overview of Scrut automation’s CSPM solution
Scrut Cloud Security is more than a traditional cloud security posture management tool. It scans and monitors misconfigurations in your public cloud accounts—AWS, Azure, Google Cloud Platform, and more.
Continuously monitor against CIS benchmarks: Scrut Cloud Security automatically tests your cloud configurations against 200+ cloud controls to maintain a strong InfoSec posture.
At Scrut, we take a different approach to security and compliance. We believe that if you have run your groundwork for cloud security, you are better prepared to get compliant. Compliance is a byproduct of being secure.
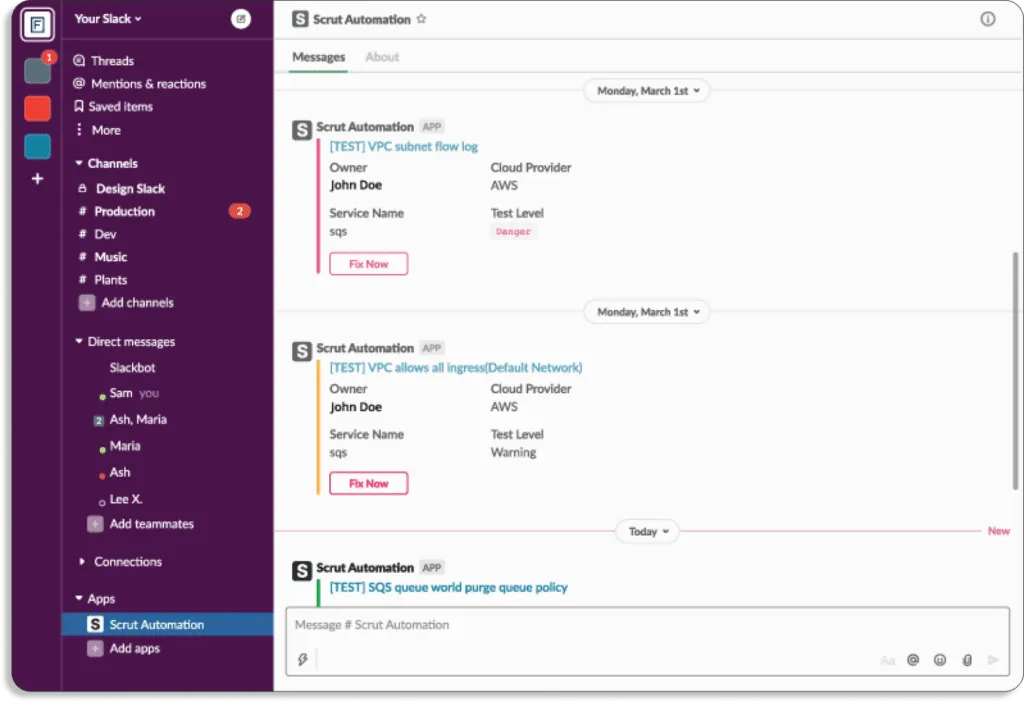
Fix cloud misconfigurations preemptively: Scrut Cloud Security ensures that your public cloud accounts are always compliant and secure.
When misconfigurations occur, Scrut gives you alerts with actionable recommendations for remediation.
Moreover, you can delegate tasks to team members for misconfiguration fixes.
Furthermore, you get notifications directly on your existing tools, like Slack.
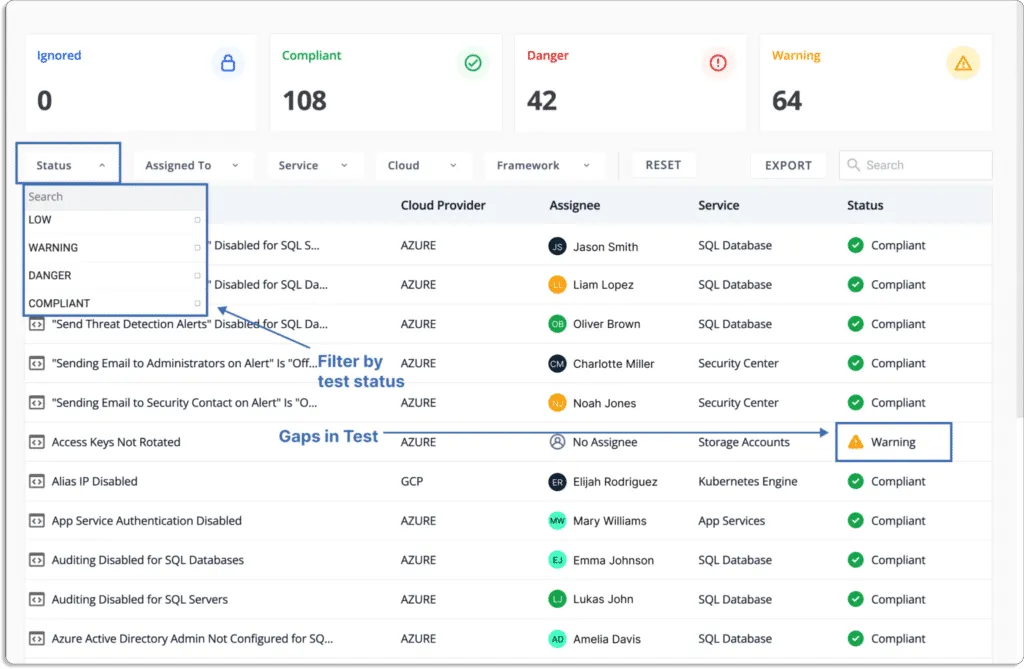
Unlike other CSPM platforms, Scrut doesn’t just bombard your security teams with alerts. During an internal research study, we found that one of the key reasons customers preferred us over other CSPM platforms was our contextual and accurate alerts. So, we developed Scrut Cloud Security in such a way that it is easy to act on them.
With their previous CSPM tool, one of our current customers was getting many false positives that wasted their security team’s time.
The issues were resolved as soon as they moved to Scrut resolved. Through a unified dashboard for all the risks and automated classification of status, you know what to work on first.
Status
Danger – Most critical issues. Work on these first.
Warning – After you’ve addressed the issues marked as “danger”, you can move on to these.
Low – These are low-priority risks that can be addressed last.
Compliant – Everything is fine. You don’t need to do anything.
Strengthen your cloud-native security: Scrut Cloud Security helps you establish full-stack security for all your cloud-native deployments, across compute instances, databases, containers, and serverless, by implementing best-practice security policies consistently across your hybrid and multi-cloud infrastructure.
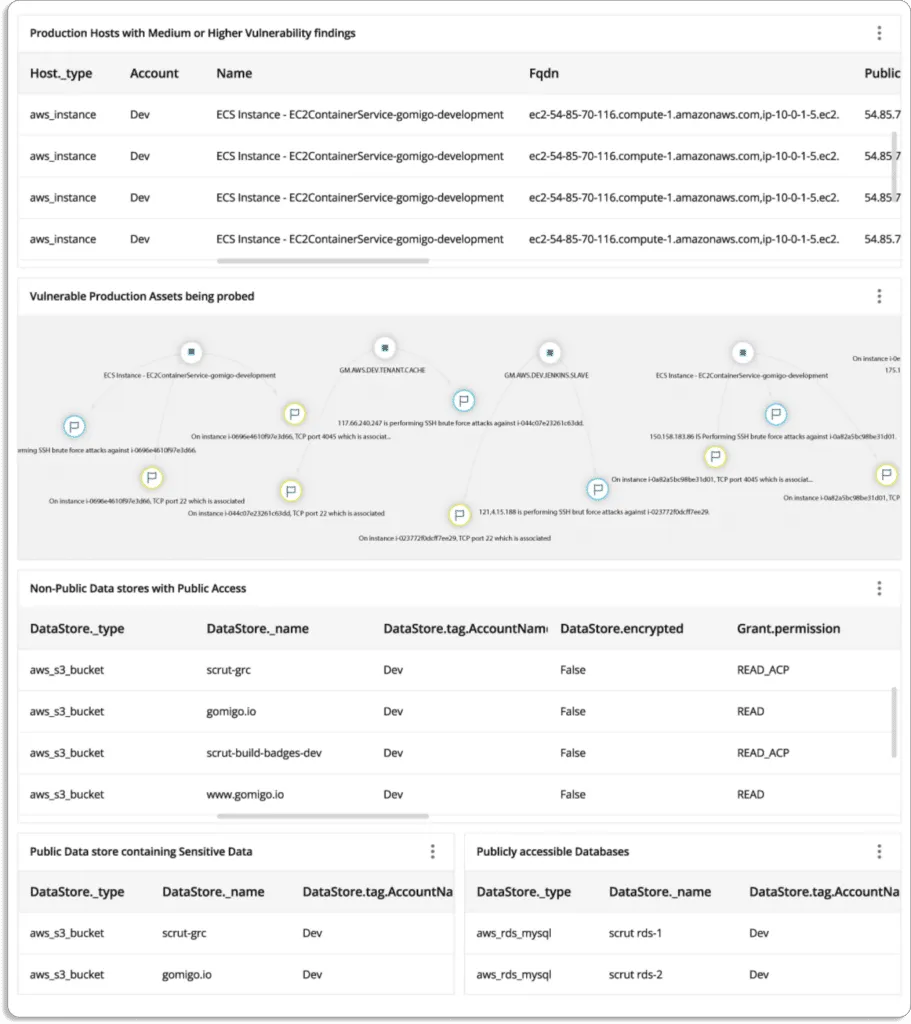
Now, let’s see a case study on how Scrut Cloud Security helped Typesense improve their cloud security posture and get SOC 2 Type 2 compliant 5x faster.
One of our customers, Typesense, wanted to build a secure cloud posture to get compliant with SOC 2 Type 2 but needed more visibility into their cloud risks. So, they turned to Scrut Automation.
During our initial discussion, we found that they had thousands of EC2 instances, which were difficult to monitor. Scrut solved those issues with automated monitoring across their cloud environment.
As a result, they completed their SOC 2 audit at 5x speed.
Here is what Jason Bosco, founder, and CEO of Typesense has to say about Scrut.
Concluding remarks
It is clear that with the increasing use of cloud services, CSPM has become a crucial component of any organization’s security posture.
But as cloud technology evolves, the need for a robust and dynamic cloud security approach becomes more pressing. CSPM is definitely here to stay, and it will undoubtedly play a vital role in securing the cloud environments of organizations in the years to come.
So, don’t get left behind, stay ahead of potential security threats, and maintain a strong security posture in the ever-changing cloud landscape with Scrut’s CSPM solution.
It’s an all-in-one cloud security solution that enables organizations to gain visibility into your cloud environment, identify potential security threats and vulnerabilities, and take action to address them before they can be exploited by attackers.

FAQs
What is an example of a CSPM?
There are several CSPM solutions available in the market today. But the most popular CSPM solution right now is from Scrut Automation.
What does CSPM provide?
CSPM, or Cloud Security Posture Management, provides comprehensive security for an organization’s cloud environment.
What is the difference between CWPP and CSPM?
CWPP and CSPM are both cloud security solutions, but they differ in their focus and scope. CWPP, or Cloud Workload Protection Platforms, is designed to protect individual workloads or virtual machines (VMs) in the cloud environment, while CSPM provides a comprehensive approach to securing an organization’s entire cloud environment.
What are the benefits of cloud security posture management?
Cloud Security Posture Management (CSPM) provides several benefits to organizations that use cloud services such as improved security, increased compliance, reduced risk, and simplified management.
Table of contents


















