Security in a multi-cloud world entails continuously managing cloud threats and ensuring cloud resiliency. Cyber incidents, like data loss, unauthorized access across various cloud environments, and non-compliance, are more likely in unprotected cloud environments.
Cloud security tools solve these issues by providing visibility into your cloud infrastructure, controlling your cloud assets, and helping you protect your critical business assets.
Most cloud providers follow higher-than-industry-standard security practices by default and actively protect the integrity of their servers and infrastructure. However, it’s the responsibility of organizations to protect their data, applications, and workload in the cloud.
According to Verizon’s Annual Data Breach Investigation Report, 82% of breaches occur due to human errors or social attacks on the client’s end, with almost no mention of cloud service providers causing the breach.
Cloud security in a hybrid and multi-cloud environment requires tools that work in sync across public and private cloud providers and on-premises deployments.
There are different types of challenges in securing the cloud, and each challenge requires a different type of solution.
For example,
- You need cloud security posture management (CSPM) for misconfigurations in the cloud.
- You need a cloud access security broker (CASB) to provide visibility and enforce security policies.
- For protecting workloads deployed in public, private, and hybrid clouds, you need a cloud workload protection platform (CWPP).
- You need cloud infrastructure entitlement management (CIEM) to control identities and privileges.
- For managing customer identities, preferences, and profile data at scale, you will require a customer identity and access management (CIAM) tool.
In the following section, let’s concentrate on each category of cloud security tool and how it helps safeguard cloud environments.
Tools for Cloud Security
Hundreds of tools deal with various aspects of cloud security and have different security and compliance capabilities.
Let’s examine the most popular categories with the top tools for each of the categories.
Cloud Security Posture Management (CSPM) Tools
CSPM tools give organizations visibility across their cloud infrastructure, allowing them to automate the detection and remediation of security risks through security assessments and automated compliance monitoring. CSPM can also detect misconfigurations that can lead to data breaches.
1. Scrut Cloud Security
Scrut Cloud Security is more than a traditional cloud security posture management tool. It scans and monitors misconfigurations in your public cloud accounts—AWS, Azure, Google Cloud Platform, and more. The platform can integrate with your cloud infrastructure and application landscape within minutes.
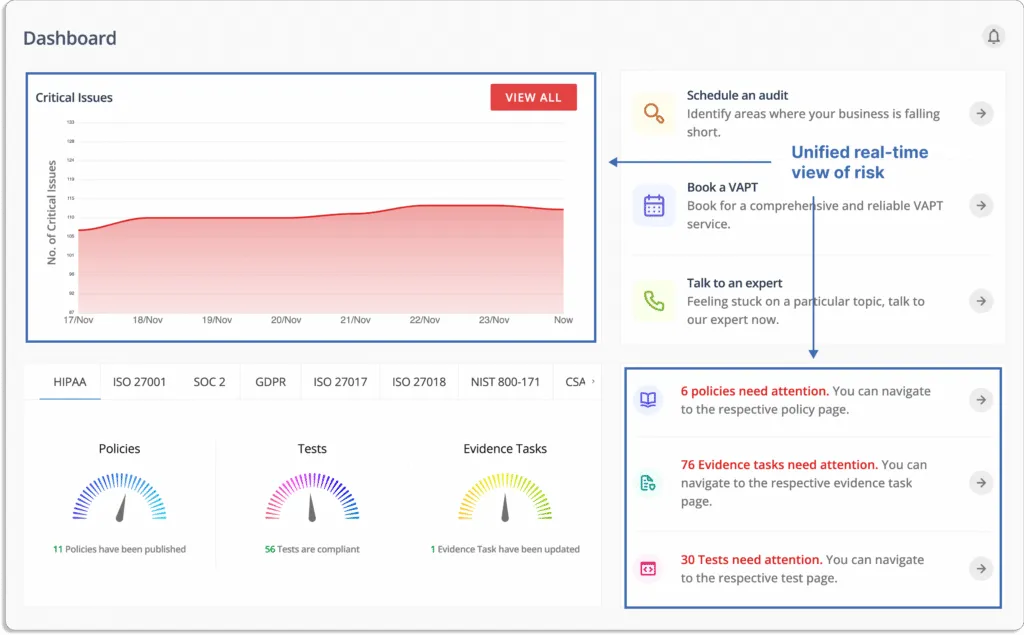
From security to compliance and governance, Scrut got you covered!
Here are some features to consider:
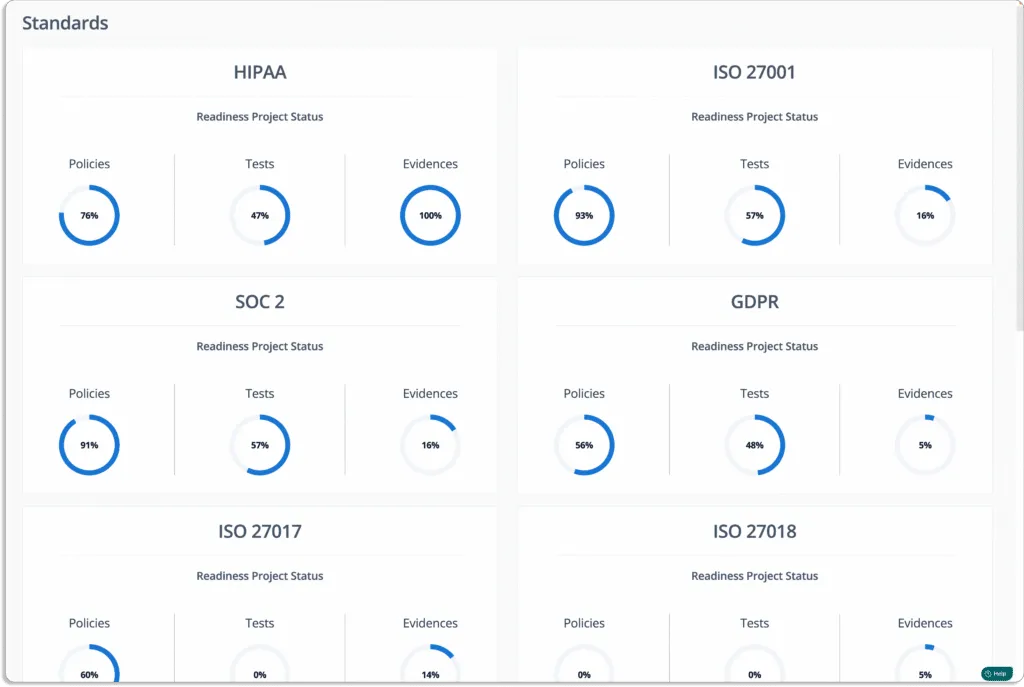
- Continuous cloud monitoring: Scrut Cloud Security automatically tests your cloud configurations against 200+ cloud controls across CIS Benchmarks to maintain a strong InfoSec posture.
Scrut automatically maps controls against different standards and shows their latest status to understand whether they are compliant or not. You won’t need to do anything in order to check your compliance.
- Fix cloud misconfigurations preemptively: Scrut Cloud Security ensures that your public cloud accounts are always compliant and secure.
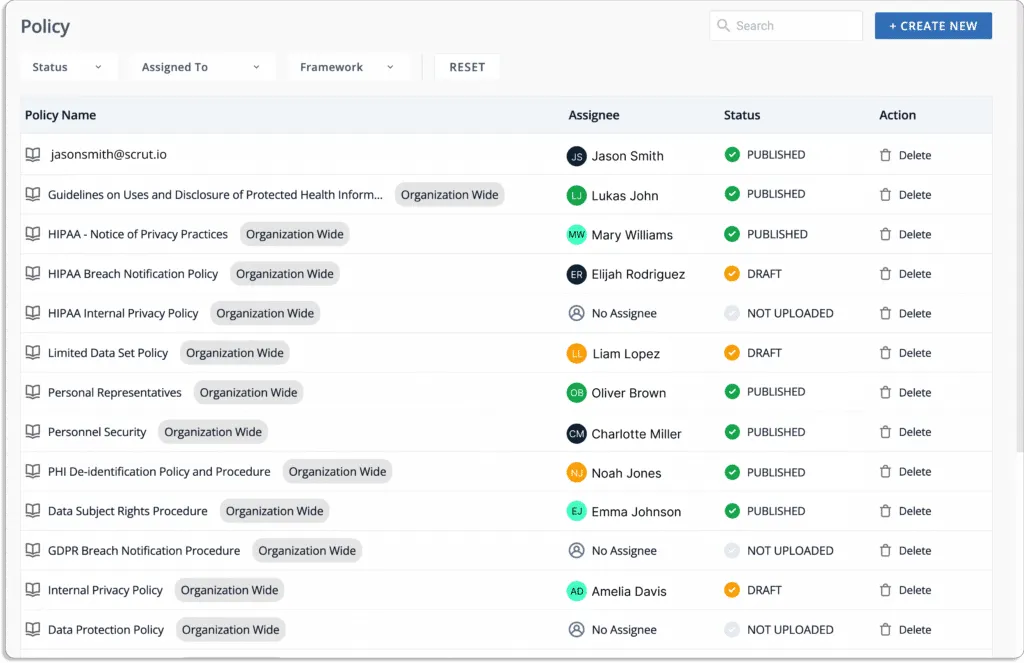
The platform provides alerts and a step-by-step guide for remediation to fix misconfigurations, as shown in the screenshot below.
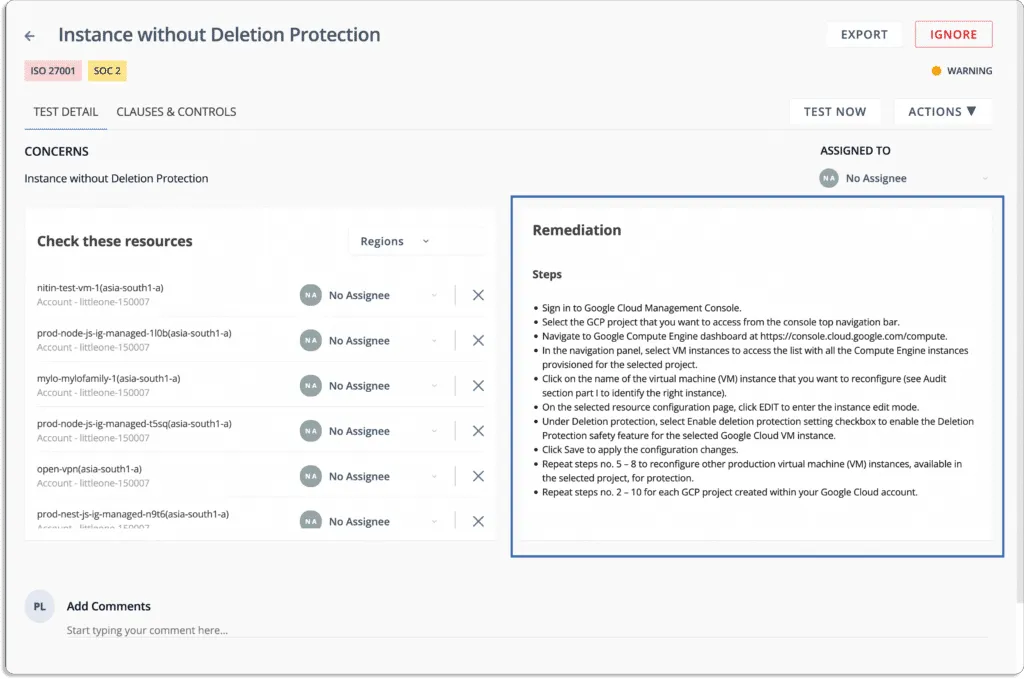
Further, the platform allows you to assign different remediation tasks to team members to fix misconfigurations.
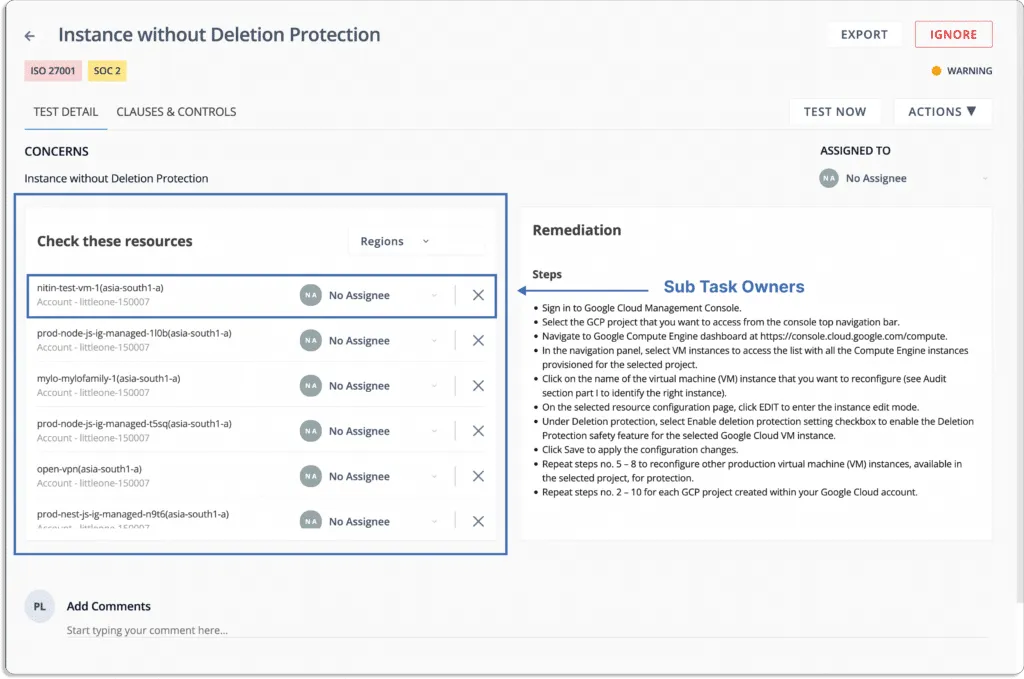
- Prioritize cloud risks based on the criticality
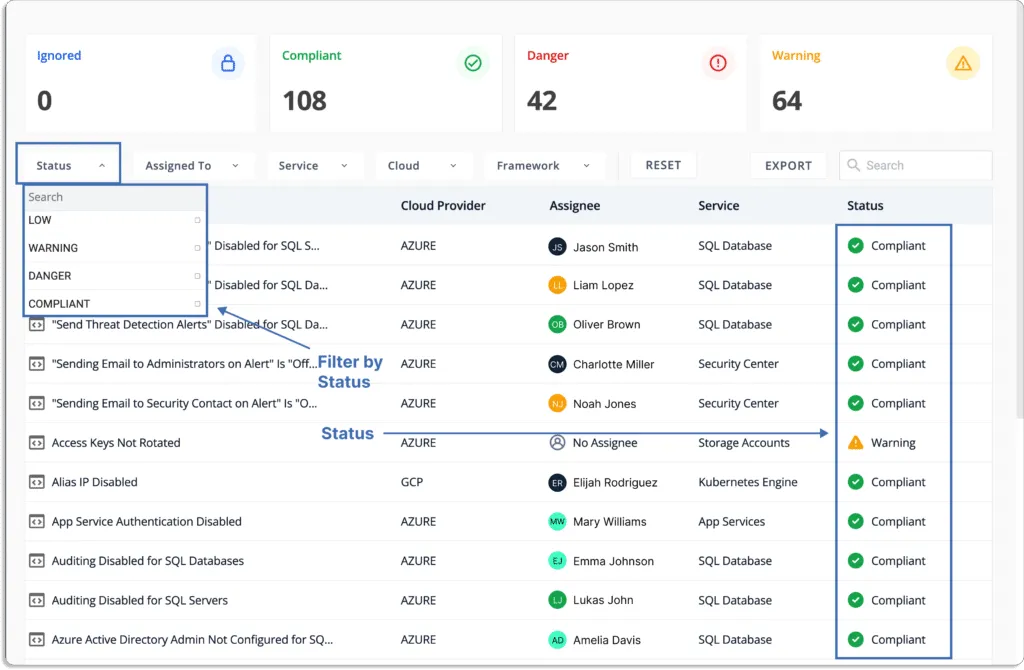
Through a unified dashboard for all the risks and classification of status, you know what to work on first.
Status
- Danger – Most critical issues. Work on these first.
- Warning – After working on the issues marked as danger, next, you can work on these.
- Low – These risks are informational in nature and should be worked on last.
- Compliant – Everything is fine. You don’t need to do anything.
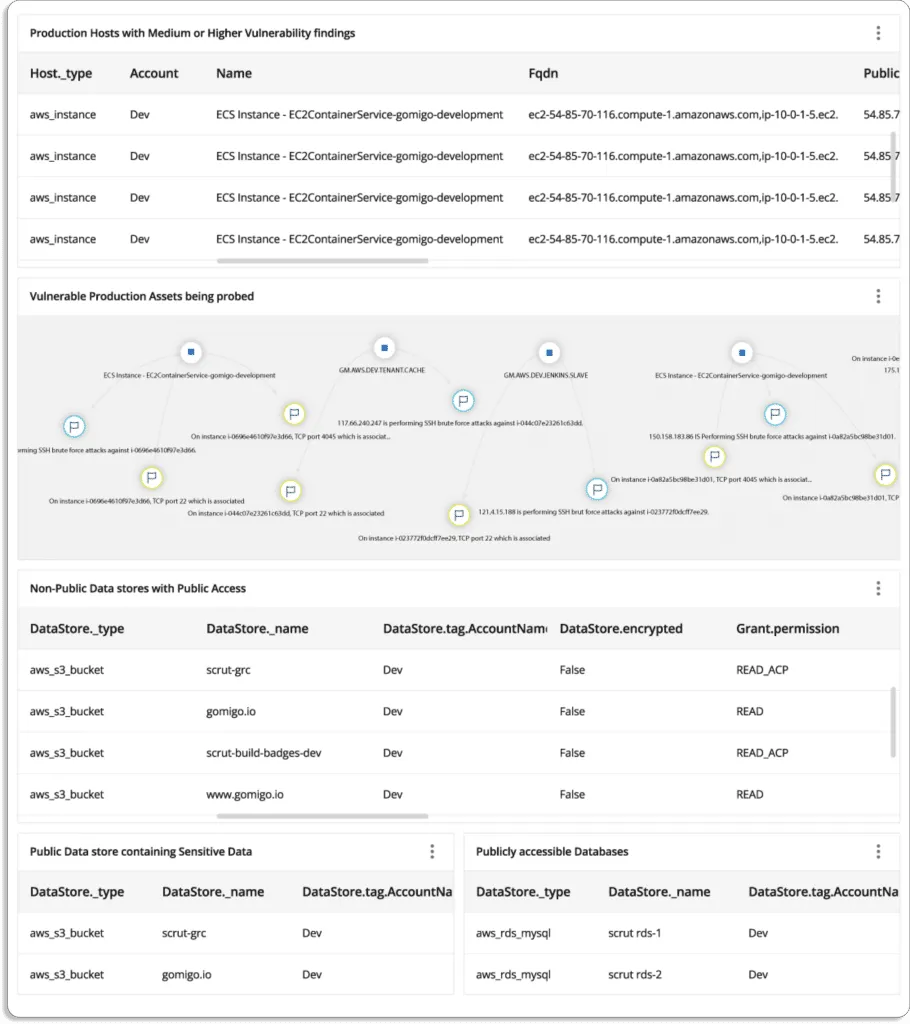
- Full-stack security: Scrut Cloud Security enables you to establish complete security for all your cloud-native deployments, across compute instances, databases, containers, and serverless, by helping you implement the best security practice policies consistently in your hybrid and multi-cloud infrastructure.
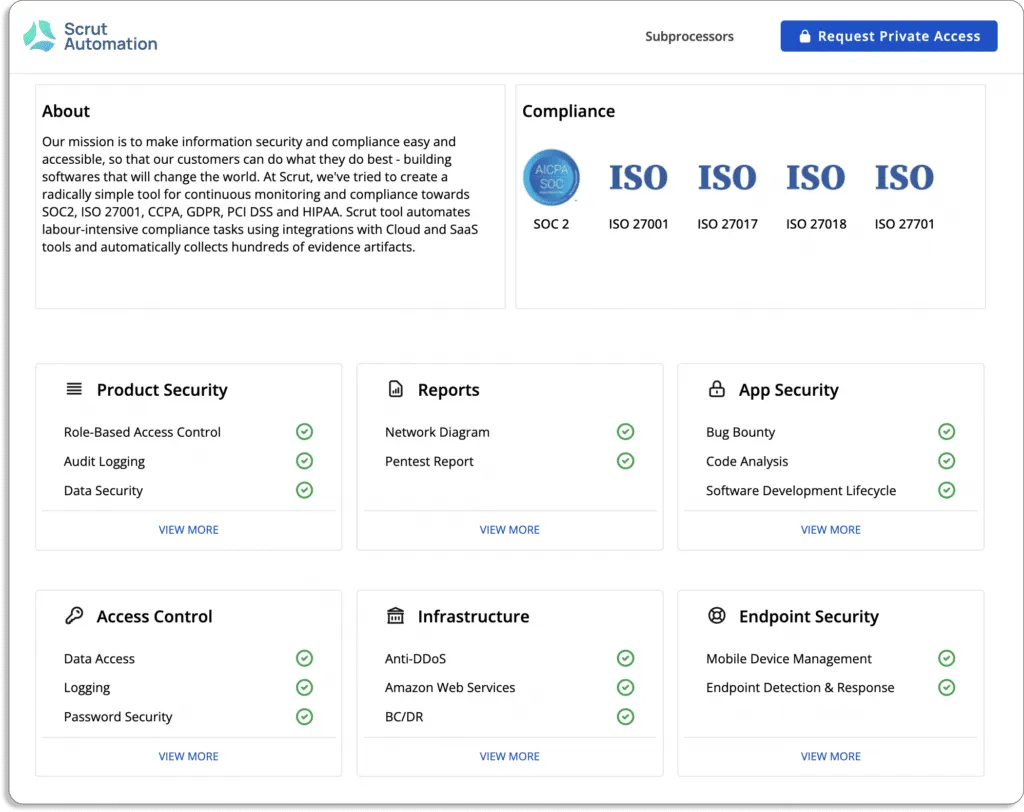
- Manage evidence of compliance and demonstrate trust: With Scrut’s Trust Vault, you can easily manage evidence of compliance. Customers can see your security and compliance posture in real-time hassle-free. All evidence documentation required to demonstrate compliance can be stored and managed in Trust Vault.
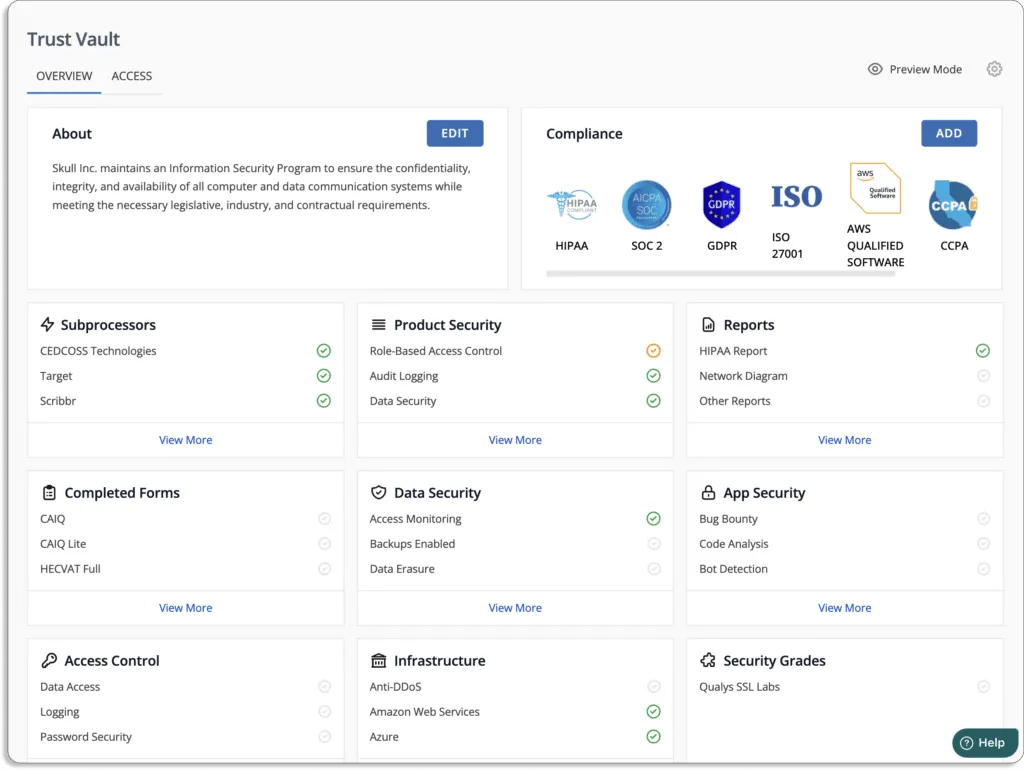
You can see Scrut’s Trust Vault page below.
- Perform risk management with ease: To automate risk identification, it scans your ecosystem for risks across the code base, infrastructure, applications, vendors, containers, databases, and more.
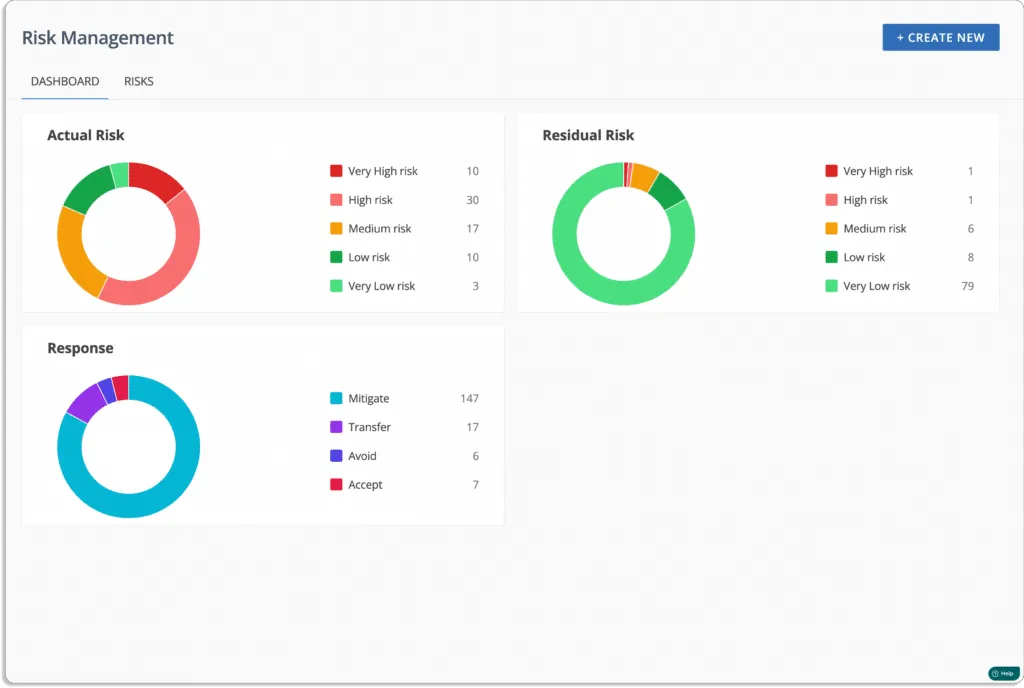
Scrut automates risk assessment by risk scoring. Afterward, you can see risks heatmaps to visualize the results.
Learn how Prozo, an end-to-end supply chain company, uses Scrut Automation to detect potential misconfigurations in its cloud infrastructure early and continuously.
Customer Rating
- G2: 5/5
2. JupiterOne
JupiterOne is a cloud compliance platform enabling InfoSec teams to understand their cloud ecosystem and vulnerability footprint better. The platform shows asset relationships in a way that allows for information on the potential impact of vulnerabilities. It automatically gathers and stores asset and relationship data, giving you deeper security insights and immediate search results.
Pros
- Performs cloud network mapping and vulnerability tracking.
- Easy to build a query and get it running quickly.
Cons
- Integrations with SaaS are underdeveloped, and some important data points may not be pulled.
- Steep learning curve.
Customer Rating
- G2: 5/5
3. Wiz
Wiz is a cloud security platform that reduces risks in popular cloud provider instances (AWS, GCP, Azure, etc.), containers, serverless operations, data stores, and Kubernetes environments. It was specifically developed for complex multi-environment, multi-workload, and multi-project cloud estates. It connects in minutes using a completely API-based method that scans all workloads and platform configurations.
Pros
- It provides a single pane of glass for your operations teams to monitor all environments.
- It takes a snapshot of your compute instance and then applies all scans and processes to it to reduce the impact on your production compute instances.
Cons
- Reports are only available as PDF or CSV files rather than dashboard-style views.
- There is a steep learning curve for the syntax for gathering metrics that are not available by default and for using the graph feature.
Customer Rating
- G2: 4.8/5
Cloud Security Access Broker (CASB) Tools
A cloud access security broker (CASB) is a point where security policies are enforced between cloud service consumers and cloud service providers so that security gaps can be addressed as cloud-based resources are accessed. A CASB, besides providing visibility, enables organizations to extend the reach of their security policies from on-premises infrastructure to the cloud and create new policies for cloud-specific context.
1. ZScaler
The multitenant Zscaler cloud security platform was created specifically to provide security as a service. It uses Zscaler secure access service edge (SASE) on top of its flagship products to give visibility and control over Zscaler private access and Zscaler internet access through a single interface. Using zero-trust network access, ZScaler eliminates the danger of adding remote users to the network.
Pros
- It uses a Zero Trust exchange and can be deployed and managed without any physical or virtual hardware.
- Internet security is enabled, protecting your computer from viruses and alerting you if you enter a potentially dangerous website.
Cons
- The documentation is complex to read, even for simple tasks.
- Does not provide DLP (data loss prevention).
Customer Rating
- G2: 4.3/5
2. Netskope
Netskope Cloud Security is a platform that gives visibility, real-time data and threat protection when accessing cloud services, websites, and private apps from any location and using any device. It blocks malware and ransomware from the cloud and the web in real-time and identifies and quarantine threats like malicious payloads kept in cloud services.
Pros
- The tool has built-in DLP, Web protection, API protection, and Threat Intelligence to monitor the traffic from a single console.
- Performs SSL inspection and deep inspection on all data.
Cons
- Does not provide a complete raw log of endpoint navigation.
- There is limited ability to restrict access to a specific user group.
Customer Rating
- G2: 4.4/5
3. Forcepoint
Forcepoint CASB secures access to cloud applications and their data through a reverse proxy service that offers high-performance cloud security. Forcepoint CASB integrates with identity providers (IdPs) like Ping Identity and Okta. Within Forcepoint ONE, you can use previously established groups and organizational units. It also has an integrated identity service to support identity-based access controls and Zero Trust.
Pros
- It offers detailed user risk scoring and automated policy enforcement using behavior-based analytics in real-time.
- The extensive cybersecurity database covers a variety of threats.
Cons
- It does not provide API integration with traditional SIEM solutions.
- Does not provide granularity in user entity behavior analytics.
Customer Rating
- G2: 4.1/5
Cloud Workload Protection Platform (CWPP)
Cloud workload protection platform protects workloads deployed in public, private, and hybrid clouds. Enterprises can integrate security solutions early in the application development lifecycle and continuously throughout. The workloads within an organization’s on-premises infrastructure and cloud-based deployments are initially discovered by solutions in this category. When these workloads are identified, the solution will perform a vulnerability scan to identify any potentially dangerous security flaws.
1. Trend Micro Hybrid Cloud Security
Trend Micro Cloud is a security services platform for cloud builders to gain complete visibility and control via integrated CNAPP capabilities. All major cloud platforms are supported, as well as solutions that integrate directly into your DevOps processes and toolchain. Trend Micro provides automated scanning and response to provide direct feedback to your developers about container security threats and vulnerabilities.
Pros
- The virtual patch feature protects your legacy server from vulnerabilities.
- Whether you are working with workloads, network security, or applications security, it has unified services all under one hood.
Cons
- At times, the user interface between various modules, such as between Workload Security and Snyk, looks incoherent.
- False positive alerts make it difficult to decide which vulnerabilities to fix first.
Customer Rating
- G2: 4.6/5
2. Orca Security
Orca is a cloud security platform that analyzes your cloud configuration for vulnerabilities, malware, misconfigurations, lateral movement risk, weak and leaked passwords, and unencrypted PII. The tool combines core cloud security capabilities, such as multi-cloud compliance and posture management, container security, and others in a single, purpose-built solution.
Pros
- Orca helps create asset inventory, which is important for constantly creating and destroying ephemeral assets.
Cons
- False positives frequently show security vulnerabilities in outdated kernel versions or in things that were already been patched.
Customer Rating
- G2: 4.6/5
3. Lacework
The Lacework Polygraph Data platform protects your multi-cloud environment and prioritizes risks using your data and automation. Machine learning is used in polygraph technology to baseline normal behavior and flag unusual activity automatically. With very few false positives, you can spend less time remediating and more time focusing on what matters most. Moreover, because of the streamlined deployment process, you can have Lacework up and running in under an hour.
Pros
- Lacework provides native container security solutions that reduce the attack surface and detect threats in your container environment.
Cons
- It won’t provide remediation steps in the reports for misconfigurations.
- The setup and integration processes are challenging.
Customer Rating
- G2: 4.5/5
4. SentinelOne Singularity
SentinelOne is an endpoint protection tool that employs artificial intelligence to defend faster, at a larger scale, and with greater accuracy across their entire attack surface. With extensive AI models, every endpoint and cloud workload can autonomously stop, identify, and recover from threats. It detects threats and automatically maps them to the MITRE ATT&CK® Framework.
Pros
- The ability to centrally control windows firewall increases the security.
Cons
- Traditional features such as USB blocking and HDD encryption are missing.
- As with all EDRs, users experience false positives.
Customer Rating
- G2: 4.7/5
Cloud Infrastructure Entitlement Management (CIEM) Tools
Cloud infrastructure entitlement management is the process of controlling identities and privileges in cloud environments (CIEM). In order to identify and reduce risks connected to access entitlements that grant more access than is necessary, it is important to understand which access entitlements are present across cloud and multi-cloud environments. This is done by automatically scanning access control policies, rules, and configurations using CIEM tools.
Security teams can control cloud identities, entitlements, and the application of the least-privileged access principle to cloud infrastructure and resources with CIEM solutions. With the help of CIEM solutions, businesses can lessen the risk of access breaches brought on by overly permissive users in the cloud.
1. Authomize
Authomize enables organizations to minimize IAM risk with extensive visibility across their IaaS environments, real-time monitoring, and automated remediation. It provides centralized authorization controls for all IaaS environments. Authomize offers trigger-based workflows for continuous security implementation to help you automate your remediation efforts.
Pros
- The ability to conduct zero trust user access reviews with custom apps to map them to security incidents.
- Access control maps are available for every user.
Cons
- There is no native Jira/Atlassian connector for incident alerts and task creation,
- Does not offer much flexibility in customizing email templates.
Customer Rating
- G2: 4.5/5
2. Ermetic
With Ermetic, your AWS, Azure, and GCP environments can be understood and secured. Ermetic is an identity-first cloud infrastructure security solution. It applies full-stack analytics to continuously discover your entire inventory of multi-cloud assets and contextually identify risk. Organizations use Ermetic to proficiently manage access permissions, guarantee cloud compliance, and shift left on least privilege, limiting their cloud attack surface.
Pros
- Show you what vulnerabilities exist in your cloud accounts, which entities have excessive privileges, and where they come from.
- It allows you to get a complete picture of everything related to AWS.
Cons
- There is little room for customization when it comes to reporting capabilities.
- There is no way to assign metadata to resources in the form of tags.
Customer Rating
- G2: 4.8/5
3. SailPoint Cloud Governance
SailPoint is a predictive identity tool that automates access management and control, providing access to the appropriate identities and technological resources at the proper time by utilizing the capabilities of artificial intelligence and machine learning. The platform can automatically provision and deprovision worker access for remote work, and manage passwords and self-service access.
Pros
- All use cases and scenarios of identity management, access governance, and system integration can be handled very effectively by out-of-the-box connectors.
- By utilizing a variety of connectors available in the New Developer portal, SailPoint can communicate with on-premises systems, including legacy components.
Cons
- The IdentityNow platform allows for minimal customization, which can sometimes be a bottleneck.
- The task-based nature of IdentityIQ’s operations causes delays in processing updates from credible sources.
Customer Rating
- G2: 4.4/5
Cloud-Native Application Protection Platform (CNAPP)
By integrating the functions of tools like Cloud Security Posture Management (CSPM), Cloud Workload Protection Platforms (CWPP), and Cloud Infrastructure Entitlement Management (CIEM) into a single platform, CNAPP streamlines cloud security. It emphasizes the necessity for businesses to concentrate on cloud-native security solutions that offer a complete lifecycle approach to cloud application security compared to a patchwork of tools, according to how Gartner originally defined it.
1. Prisma Cloud
Prisma Cloud secures applications from the code to the cloud, enabling security and DevOps teams to collaborate successfully to speed up the development and deployment of secured cloud-native applications. It lets you monitor and defend cloud workloads against malicious activity in real-time. Your current SecOps and workflow platforms can be integrated with Prisma Cloud to provide configurable logging and alert streaming.
Pros
- The zero-day threat prevention feature can defend against recently created malware and threats and provide complete visibility.
- Integration with CI/CD, IaC, container-based environments, and serverless functions is simple.
Cons
- Very few reporting and compliance templates.
- It is difficult for a beginner to manage because it requires someone with a solid foundation to configure it.
Customer Rating
- G2: 4.4/5
2. Aqua
Aqua Security provides scalable security for cloud-native applications throughout the containerized application development-to-deployment lifecycle. The tool checks your cloud services, Infrastructure-as-Code templates, and Kubernetes setup against best practices and standards to ensure that the infrastructure on which applications are running is securely configured and in compliance.
Pros
- Users can generate security alerts based on Severity/Domain/Category/Plugin via various notification channels.
- Customizable dashboards for cloud security and image scanning help visualize the overall security posture.
Cons
- False positives frequently occur when performing host vulnerability assessments.
- Role-based access control is not granular enough.
Customer Rating
- G2: 4.5/5
3. Checkpoint CloudGuard
CloudGuard is an agentless cloud security platform that combines threat prevention with policy orchestration in the cloud. Organizations can use CloudGuard to visualize and assess their cloud security posture, detect misconfigurations, model and actively enforce security best practices, and protect against identity theft and data loss.
Pros
- It uses machine learning techniques to identify which areas are most critical in securing cloud workloads, allowing it to scale across multi-cloud, hybrid-cloud, and private cloud infrastructures.
- Can detect anomalies and protect the environment’s perimeter.
Cons
- No access to the dashboard’s remediation logs to identify failed remediation measures.
- For example, Lambda functions, require the installation of additional “agents” on your cloud IaaS to perform serverless scanning.
Customer Rating
- G2: 4.5/5
Customer Identity and Access Management (CIAM) Tools
Organizations can manage customer identities, preferences, and profile data at scale using CIAM software. Customers can self-register for services, login and authenticate, and manage their user profiles, including consent and other preferences, using these solutions as well.
Businesses use CIAM software to provide seamless, user-friendly online experiences for their customers while observing data privacy laws like the CCPA and GDPR.
1. Okta
Okta integrates applications into its identity management service for you; you deploy these pre-integrated applications to your users as needed while maintaining strict security policies. It works with an organization’s existing directories, identity systems, and over 4,000 applications.
Because Okta is built on an integrated platform, businesses can implement the service quickly and at a low total cost.
Pros
- Signing in with a single log-in for all of your apps saves you time and effort from having to open them all in separate windows. This keeps your tabs organized and your virtual workspace tidy.
- Once a user enters the password, it gives instant and real-time notification for approval or denial of login access.
Cons
- The mobile app is not user-friendly.
Customer Rating
- G2: 4.4/5
2. Azure Active Directory
Azure Active Directory is an identity and access management solution with integrated security. All internal and external users are connected to all apps and devices through Azure Active Directory (Azure AD), which also helps prevent identity compromise. With single sign-on, passwordless access, and a user portal, it offers a seamless and secure user experience.
Pros
- It’s one of the most popular programs for MDM and account management because it integrates with almost every website you use.
- It supports conditional access, which allows users to define different access policies depending on where they connect.
Cons
- The process of configuring Active Directory SSO with any software is time-consuming and has very little documentation.
- It can be quite confusing to set up for newcomers, especially if you don’t have much experience with the ins and outs of an active directory.
Customer Rating
- G2: 4.5/5
3. OneLogin
OneLogin makes identity management easier by providing secure one-click access to all applications (cloud or on-premise) for employees, clients, and partners across all device types.
Identity infrastructure is a set of technologies and processes that allows you to manage all of your users digital identities at any given time. With OneLogin, you can quickly extend your on-premises security framework to the cloud.
By deleting worker information from Active Directory, OneLogin facilitates IT identity policy enforcement and quickly disables app access for workers who leave or change roles.
Pros
- The ability to control access your apps’ access from a single location.
- Since the one-time password is used for authentication each time you log in, the data is kept secure.
Cons
- There are no integrations with Git and Jira.
- Users are not notified when their password is about to expire or has expired.
Customer Rating
- G2: 4.3/5
4. Auth0
The Identity Platform Auth0 adopts a modern approach to identity and is customizable, simple, and flexible as needed by development teams. Auth0 offers enterprise customers convenience, privacy, and security while protecting billions of login transactions monthly so they can concentrate on innovation.
Pros
- One of the most useful features Auth0 has to offer is hooks, which allow for custom behavior using code similar to custom code.
- Provides connectors with almost all data sources, including any IAM cloud provider or on-premises source.
Cons
- The learning curve is steep, and it is difficult to train staff members who are not particularly tech-savvy.
Customer Rating
- G2: 4.3/5
5. Frontegg
Frontegg is a tool to handle your user journey, from signup to subscription, with a scalable user and access management infrastructure. The platform offers a self-registration and self-service portal, which gives you visibility and control over personal and organizational settings for a comprehensive user experience. It also helps in monitoring your information security management system.
Pros
- It is a swift solution to add advanced login features to your product, such as social login, Single Sign-On, MFA, and others.
- The setup of multiple environments (dev, stage, and production) is simple, and changes can be transferred between these environments with the click of a button.
Cons
- The user interface is cluttered.
Customer Rating
- G2: 4.8/5





































