Choose risk-first compliance that’s always on, built for you.
Go back to blogs
Buyer's guide to cloud security vendors
Last updated on
April 17, 2025
16
min. read

Cloud storage is no longer a “future tech" but has become a necessity for every individual and every business. Storing data on physical drives is next to impossible as business data is rising exponentially. While the cloud offers numerous benefits, such as scalability, flexibility, and cost-efficiency, it also introduces a host of security challenges.
Protecting sensitive data, ensuring compliance with regulations, and safeguarding against cyber threats are paramount concerns in the cloud environment. Therefore, the importance of cloud security cannot be overstated.
As the demand for robust cloud security solutions continues to rise, the market has witnessed a proliferation of cloud security vendors. These vendors offer a wide range of products and services designed to address the unique security needs of cloud-based operations. This proliferation has created a complex landscape, making it challenging for organizations to choose the right cloud security vendors that align with their specific requirements.
The purpose of this Buyer's Guide is to assist organizations, IT professionals, and decision-makers in navigating the crowded and ever-evolving cloud security market. We will provide valuable insights, criteria, and considerations to help you make informed decisions when selecting cloud security providers.
How to assess your cloud security needs?

Cloud security needs are ever-evolving, driven by the dynamic nature of cloud environments and the evolving landscape of cyber threats. Organizations must continuously assess and adapt their security measures to protect sensitive data, applications, and infrastructure in the cloud, all while staying compliant with industry regulations and standards.
1. Assessing your organization's risk profile
Before diving into the selection of cloud security providers, it's crucial to conduct a thorough assessment of your organization's risk profile. This involves evaluating the specific risks and threats that your organization faces in the cloud environment. Consider factors such as the sensitivity of your data, industry regulations, and potential threats like data breaches, insider threats, and DDoS attacks.
Questions to ask:
- What types of data are you storing in the cloud, and how sensitive is this data?
- What are the potential risks and threats that could impact your cloud infrastructure and data?
- Do you have a clear understanding of your organization's risk tolerance?
- Have you conducted a risk assessment to identify vulnerabilities and prioritize security measures?
2. Identifying compliance requirements
Many organizations operate within regulated industries or must adhere to specific compliance standards. It's essential to identify and understand the compliance requirements that apply to your organization's use of the cloud. Compliance standards such as GDPR, HIPAA, SOC 2, and PCI DSS have stringent data security and privacy requirements that must be met.
Questions to consider:
- Which compliance standards or regulations does your organization need to adhere to?
- What are the specific security and privacy requirements outlined in these regulations?
- Are there any data residency or localization requirements that impact your cloud deployments?
- Have you documented the necessary compliance controls and measures required for your cloud environment?
3. Defining your budget
Cloud security providers come in a wide range of pricing models, from pay-as-you-go to subscription-based services. It's essential to define a clear budget for your cloud security initiatives. Consider not only the cost of security tools and services but also the costs associated with ongoing maintenance, training, and incident response.
Key budget-related questions:
- What is your allocated budget for cloud security?
- Are you looking for cost-effective solutions, or are you willing to invest in premium security offerings?
- Have you factored in the total cost of ownership (TCO) for cloud security providers, including training and operational expenses?
- Are there any budget constraints that may impact your choice of security solutions?
By thoroughly assessing your organization's risk profile, compliance requirements, and budget constraints, you'll be better prepared to make informed decisions when selecting cloud security prooviders that align with your specific needs and priorities.
What are the key considerations for evaluating cloud security vendors?
When selecting a cloud security vendor to protect your organization's valuable assets in the digital realm, it's essential to embark on this decision-making journey with a clear understanding of the critical factors to consider.
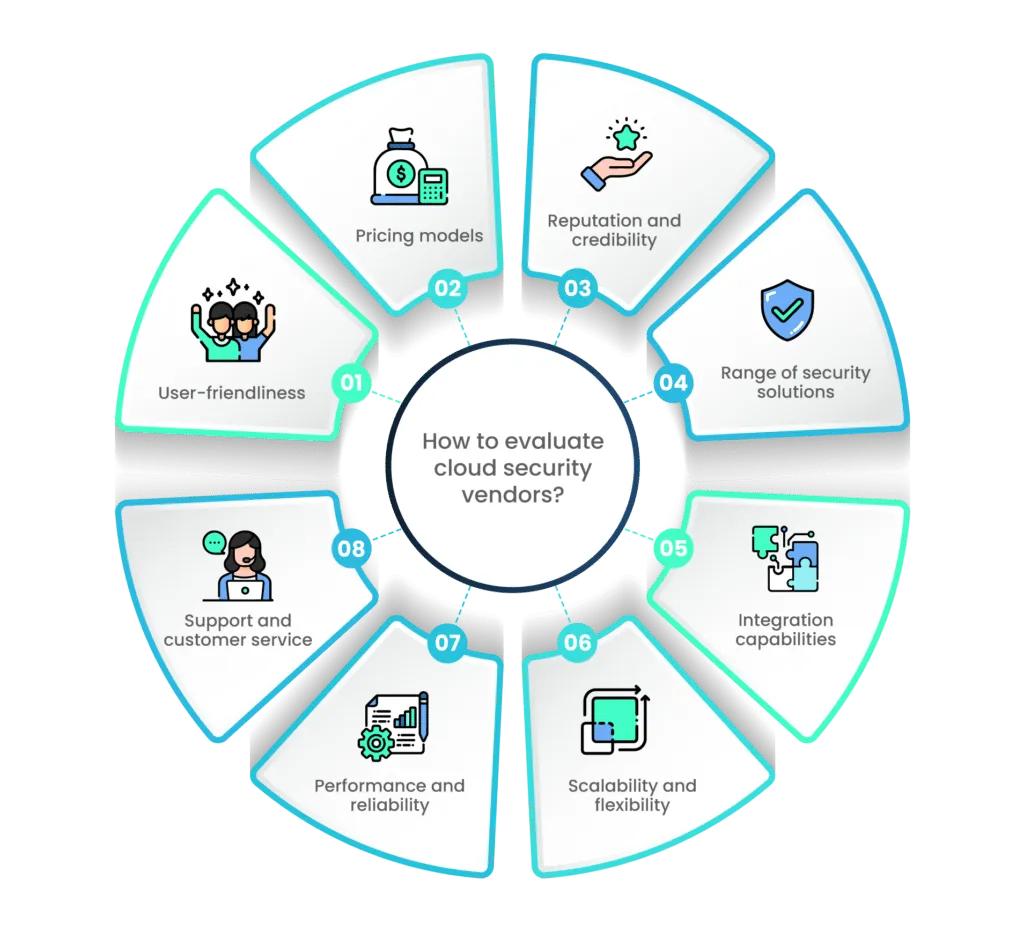
Below, we outline key considerations that will guide you toward making an informed choice for your cloud security needs.
1. Reputation and credibility
- Research and reviews: Investigate the vendor's reputation by reading customer reviews, industry reports, and case studies. A vendor with a strong track record and positive customer feedback is more likely to deliver reliable security solutions.
- Certifications and compliance: Check if the vendor holds industry certifications and compliance with relevant standards. Certifications like ISO 27001 and SOC 2 demonstrate a commitment to security.
2. Range of security solutions
- Comprehensive offerings: Assess whether the vendor offers a wide range of security solutions to cover different aspects of cloud security, including identity and access management, data encryption, threat detection, and more.
- Scalability: Ensure the vendor's solutions can scale with your organization's growth and evolving security needs.
3. Integration capabilities
- Compatibility: Determine if the vendor's solutions integrate seamlessly with your existing cloud infrastructure, applications, and third-party tools.
- APIs and documentation: Check if the vendor provides robust APIs and comprehensive documentation for easy integration.
- Scalability and flexibility
- Scalability: Ensure that the vendor's solutions can adapt to your organization's changing needs, allowing you to add or adjust security measures as required.
- Customization: Evaluate the flexibility to customize security policies and settings to align with your specific requirements.
4. Performance and reliability
- Uptime and availability: Investigate the vendor's historical uptime and availability records. Downtime can be detrimental to your security posture.
- Performance benchmarks: Assess the impact of security solutions on the performance of your cloud services. Minimal performance degradation is crucial.
5. Support and customer service
- Support channels: Evaluate the availability of customer support channels, such as email, phone, chat, and a knowledge base.
- Response times: Inquire about response times for support requests, especially in the event of security incidents.
6. User-friendliness
- Ease of use: Consider the user-friendliness of the vendor's security solutions. Complex and unintuitive interfaces can lead to operational challenges.
- Training and documentation: Check if the vendor provides training materials and documentation to help your team effectively use their solutions.
7. Pricing models
- Cost transparency: Understand the vendor's pricing structure and ensure it aligns with your budget. Be aware of any hidden costs.
- Scalability costs: Analyze how pricing scales as your organization grows or requires additional security features.
What are the different types of cloud security providers?
As you explore the realm of cloud security vendors, it's important to be aware of the various categories and tools available to protect your cloud-based assets.
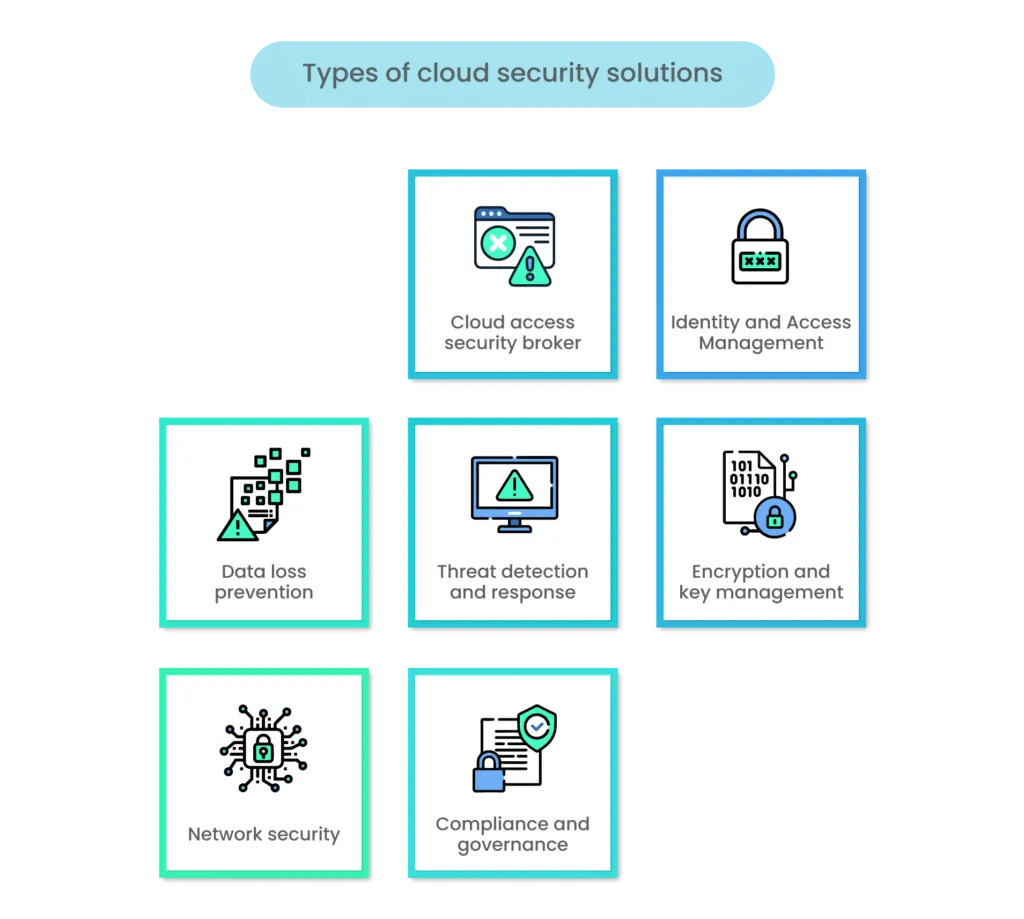
Here are some key types of cloud security providers:
1. Cloud access security broker (CASB)
- CASB solutions act as intermediaries between users and cloud service providers, ensuring that cloud activities align with security policies.
- They provide visibility into cloud usage, enforce access controls, and offer threat detection capabilities.
2. Identity and Access Management (IAM)
- IAM solutions manage user identities, roles, and permissions for cloud resources.
- They play a crucial role in ensuring that only authorized individuals can access sensitive data and applications in the cloud.
3. Data loss prevention (DLP)
- DLP solutions monitor and prevent the unauthorized sharing or leakage of sensitive data in the cloud.
- They use policies to detect and block actions that could lead to data exposure.
4. Threat detection and response
- These solutions use advanced algorithms and threat intelligence to identify and respond to security threats in real time.
- They are vital for detecting and mitigating attacks, such as malware, phishing, and insider threats.
5. Encryption and key management
- Encryption solutions protect data by converting it into unreadable ciphertext, ensuring that even if data is compromised, it remains secure.
- Key management solutions manage encryption keys, a critical component of data protection.
6. Network security
- Network security solutions safeguard cloud infrastructure and data by controlling traffic, detecting and preventing intrusions, and mitigating DDoS attacks.
- They help create secure network architectures in the cloud.
7. Compliance and governance
- Compliance and governance solutions assist organizations in meeting regulatory requirements and industry standards in the cloud.
- They provide tools for auditing, reporting, and ensuring adherence to security policies.
These types of cloud security vendors are designed to address specific aspects of cloud security, and organizations often use a combination of them to create a robust security posture tailored to their needs and risk profile. Understanding these categories will help you make informed choices when selecting the right security tools for your cloud environment.
What is the procurement process for cloud security solution?
When you've identified your cloud security needs and potential vendors, it's time to navigate the procurement process.

Here are the key steps involved in procuring cloud security providers:
1. Request for proposal (RFP)
- Start by creating a detailed RFP that outlines your organization's security requirements, expectations, and evaluation criteria.
- Distribute the RFP to potential vendors, inviting them to submit proposals that address your specific needs.
2. Vendor demos and trials
- Once you receive proposals, request vendor demos and trials. This allows you to get hands-on experience with the security solutions.
- During demos and trials, assess how well each vendor's offerings align with your requirements and how user-friendly they are.
3. Evaluating proposals
- Evaluate vendor proposals based on predefined criteria, such as features, scalability, performance, support, and cost.
- Consider factors like reputation, compliance, and the vendor's ability to address your organization's unique challenges.
4. Negotiating contracts
- Initiate contract negotiations with the selected vendor(s). This phase involves discussing terms, pricing, service-level agreements (SLAs), and any customization needs.
- Ensure that all aspects of the contract are clearly defined, including licensing, maintenance, and support.
5. Implementation planning
- Collaborate with the chosen vendor to develop a comprehensive implementation plan. This plan should include timelines, responsibilities, and milestones.
- Consider any necessary training for your team and ensure a smooth transition to the new cloud security solutions.
What are the security best practices for cloud adoption?
As organizations increasingly embrace cloud computing, it's imperative to establish robust security practices to safeguard data and operations.

Here are some essential security best practices for successful cloud adoption:
1. Security awareness training
- Provide ongoing security awareness training to your employees to educate them about the risks and best practices associated with cloud usage.
- Ensure that employees understand how to recognize phishing attempts and other security threats specific to the cloud environment.
2. Regular auditing and monitoring
- Implement continuous monitoring of your cloud infrastructure and applications to detect and respond to security incidents promptly.
- Utilize cloud-specific monitoring tools to track access, configurations, and user activities in real time.
3. Incident response planning
- Develop a comprehensive incident response plan tailored to cloud-specific threats and vulnerabilities.
- Conduct regular tabletop exercises to ensure your team is prepared to respond effectively to security incidents in the cloud.
4. Cloud security policies and governance
- Establish clear cloud security policies and governance frameworks that align with your organization's overall security strategy.
- Define roles and responsibilities for cloud security, including who is responsible for managing configurations, access control, and compliance.
5. Compliance and regulations
- Stay informed about relevant compliance standards and regulations applicable to your industry and geographic location.
- Ensure that your cloud security practices align with these standards and that you maintain compliance in the cloud.
6. Data encryption
- Encrypt sensitive data both in transit and at rest within the cloud environment.
- Implement strong encryption mechanisms and key management practices to protect data from unauthorized access.
7. Access control and identity management
- Implement robust identity and access management (IAM) policies to control who has access to cloud resources and data.
- Utilize multi-factor authentication (MFA) and least privilege access principles to enhance security.
8. Regular security assessments
- Conduct regular security assessments, vulnerability scans, and penetration testing on your cloud infrastructure and applications.
- Address identified vulnerabilities promptly to mitigate potential risks.
9. Backup and disaster recovery
- Establish automated backup processes for critical data and applications in the cloud.
- Develop a comprehensive disaster recovery plan to ensure business continuity in case of data loss or service disruption.
10. Third-party risk management
- Evaluate and monitor the security practices of third-party vendors and cloud service providers.
- Ensure that they meet your organization's security and compliance requirements.
By incorporating these security best practices into your cloud adoption strategy, you can create a secure and resilient cloud environment that protects your data, meets regulatory requirements, and effectively mitigates security risks.
What are the future trends in cloud security?
As cloud technology continues to evolve, so do the security challenges and solutions associated with it.

Here are some emerging trends in cloud security that are expected to shape the future:
1. Zero trust security model
- The zero-trust security model is gaining prominence as organizations shift away from the traditional perimeter-based approach.
- Zero trust assumes that threats may exist within the network and requires continuous verification of users, devices, and applications before granting access.
- Implementing zero-trust principles in cloud environments enhances security by minimizing the attack surface and reducing the risk of lateral movement by attackers.
2. AI and machine learning in threat detection
- Artificial intelligence (AI) and machine learning (ML) are being increasingly used to bolster threat detection and response capabilities.
- AI and ML algorithms can analyze vast amounts of data to identify patterns and anomalies that might indicate security threats.
- These technologies enhance the ability to detect and mitigate advanced and evolving cyber threats in real time.
3. Container security
- Containers have become a fundamental component of cloud-native applications, but they also introduce security challenges.
- Container security solutions are emerging to protect containerized applications and ensure the security of container orchestration platforms like Kubernetes.
- These solutions focus on vulnerability scanning, runtime protection, and access control for containers.
4. Serverless security
- Serverless computing, where code execution is event-driven without managing servers, is on the rise.
- Security in serverless environments requires a new approach, addressing issues like function isolation, access control, and event source validation.
- Serverless security solutions are emerging to protect against serverless-specific threats and vulnerabilities.
5. Cloud-native security tools
- Cloud-native security tools are designed to seamlessly integrate with cloud platforms and DevOps workflows.
- These tools provide automated security checks during the development and deployment phases, enhancing the security posture of cloud-native applications.
6. Quantum-safe encryption
- With the advent of quantum computing, traditional encryption methods are at risk of being compromised.
- Quantum-safe encryption algorithms are being developed and tested to secure data in a post-quantum computing world.
7. Enhanced cloud compliance solutions
- As regulations evolve, cloud compliance solutions are becoming more sophisticated, offering automated compliance monitoring, reporting, and remediation.
- These tools help organizations maintain compliance while operating in complex cloud environments.
Keeping abreast of these future trends in cloud security is crucial for organizations seeking to stay ahead of emerging threats and ensure the continued protection of their cloud-based assets and data. Integrating these trends into your cloud security strategy will be essential for maintaining a robust security posture in the evolving digital landscape.
Top cloud security companies
There are many cloud security providers in the market at this time. Let’s look at some of the leaders that rule the market today:
1. Proofpoint
- Overview: Proofpoint is a cybersecurity company that specializes in email security, phishing protection, and advanced threat intelligence. They provide solutions to protect organizations from email and cloud-based threats.
- Key offerings: Proofpoint offers products for email security, email archiving, data loss prevention (DLP), and threat intelligence. Their solutions help organizations safeguard against phishing attacks, malware, and data breaches.
- Notable features: Proofpoint's threat intelligence platform provides real-time threat analysis and comprehensive threat visibility, helping organizations stay ahead of evolving cyber threats.
2. Check Point Software
- Overview: Check Point Software is a multinational provider of software and hardware products for IT security, including network security, cloud security, and mobile security.
- Key offerings: Check Point offers a wide range of security solutions, including firewalls, intrusion prevention systems (IPS), threat prevention, and cloud security. Their solutions are designed to protect networks, cloud environments, and endpoints from cyber threats.
- Notable features: Check Point's SandBlast technology provides advanced threat prevention capabilities, including protection against zero-day threats and malware.
3. CrowdStrike
- Overview: CrowdStrike is a cybersecurity company known for its cloud-native endpoint protection platform. They focus on endpoint security, threat intelligence, and incident response.
- Key offerings: CrowdStrike Falcon is their flagship product, offering endpoint protection, threat hunting, and security incident response. It uses AI and machine learning to detect and prevent threats.
- Notable features: CrowdStrike's threat graph provides real-time visibility and threat intelligence across endpoints, enabling organizations to respond to threats rapidly.
4. Palo Alto Networks
- Overview: Palo Alto Networks is a cybersecurity company that specializes in firewall and cloud security solutions. They offer a wide range of products to protect organizations from cyber threats.
- Key offerings: Palo Alto Networks provides next-generation firewalls, cloud security, and threat intelligence solutions. Their security platform is designed to secure networks, cloud environments, and endpoints.
- Notable features: The Palo Alto Networks Security Operating Platform offers centralized management and automation to improve security posture and reduce manual tasks.
5. VMWare
- Overview: VMware is a global leader in virtualization and cloud infrastructure solutions. While not exclusively a cybersecurity company, they offer security solutions for virtualized and cloud environments.
- Key offerings: VMware offers products like NSX, which provides network security for virtualized environments, and Carbon Black, which focuses on endpoint security. These solutions help organizations secure their virtualized and cloud infrastructure.
- Notable features: NSX enables micro-segmentation, allowing organizations to create granular security policies for each application, enhancing network security in virtualized environments.
These companies play significant roles in the cybersecurity landscape, offering a range of solutions to protect organizations from the evolving and complex cyber threats they face.
In Conclusion
In conclusion, cloud storage has evolved into an essential for individuals and businesses, accompanied by intricate security challenges. To navigate this landscape, organizations must continually assess security needs and compliance requirements, define a clear budget, carefully select cloud security vendors based on key criteria, understand various solutions, follow a systematic procurement process, implement crucial security practices, and stay updated on emerging trends in cloud security. By adhering to these principles, organizations can safeguard their cloud assets effectively in the dynamic digital landscape.
Ready to fortify your cloud security? Start your journey today by assessing your needs and exploring trusted vendors. Get Scrut's cloud security solution to help you through your journey.
FAQs
1. What is cloud storage, and why is it essential for businesses and individuals?
Cloud storage is a service that allows individuals and businesses to store their data and files on remote servers accessible via the Internet. It's essential because it provides flexibility, scalability, and cost-efficiency for managing and accessing data.
2. What factors should organizations consider when selecting a cloud security vendor?
Organizations should evaluate vendors based on reputation, the range of security solutions offered, integration capabilities, scalability, performance, support, user-friendliness, and pricing models.
3. What steps should organizations follow in the procurement process for cloud security solutions?
The procurement process includes creating a detailed Request for Proposal (RFP), vendor demos and trials, evaluating proposals, contract negotiations, and comprehensive implementation planning.
Table of contents


















