The password manager giant LastPass faced a data breach in August 2022, when an unknown threat actor gained access to its third-party cloud-based storage service containing the backup of the production data.
The LastPass leadership came forward to admit the extent of this breach in December 2022 by confirming that the threat actors had access to both unencrypted data as well as fully-encrypted sensitive fields.
However, they warned that the threat actors might attempt to use brute force to guess the customers’ master password and decrypt the copies of the vault data they had stolen.
This breach is a classic example of how an increase in market size and diversification has led to the exposure of newer risks for organizations. Industries of all sizes and types now have to be on the lookout for vulnerabilities and monitor their cyber attack surface continuously to avoid losses.

Today’s world requires solid compliance functions to deal with the swift changes in the market. The authorities have also been introducing new regulations periodically, like the Personal Data Protection Law in Indonesia (PDPL) and Digital Personal Data Protection Bill in India. They are also introducing new revised versions of the old frameworks to widen the scope of protecting their citizens’ data privacy. For example, California Privacy Rights Act is an extension of the California Consumer Privacy Act.
However, it is imperative that organizations not just follow these regulations but be mindful of the best practices they implement in order to strengthen their organization’s information security. That’s where infosec compliance comes into play. Infosec compliance is a regulatory or voluntary framework that helps organizations maintain data privacy.
In this article, we will discuss the seven infosec compliance trends organizations should watch out for in 2023 and why!
Infosec compliance trends to watch out for in 2023s
The role of government or lawmakers in the infosec sector, entrusted with the responsibility of framing the laws, is to anticipate risks and build resilience to improve the citizens’ data security. The role of organizations, on the other hand, is to comply with the leading industry frameworks to secure customers’ data and protect themselves from financial and reputational damages.
Every organization is susceptible to complying with different compliance frameworks based on various factors, like business operations, location, customer location, and inventories. A compliance workflow is a predefined flow of activities centered around compliance policies and government regulations. It ensures uniformity in the activities, security of the data, and greater visibility of the process and makes compliance audits much simpler.
IBM found that the average cost of data breaches for organizations with high levels of compliance failure reached $5.57 million vis-à-vis the mean cost of $4.35 million.

1. Automation of compliance procedures

Automated compliance is used for performing and simplifying compliance procedures. The activities carried out manually by the employees can be carried out with technological advances, enabling organizations to automate compliance workflows.
Compliance software is a tool to monitor an organization’s internal systems and controls to ensure that it adheres to the standards and requirements it falls under.
Accenture also found that 90% of the compliance leaders believed that there would be a 30% rise in the cost of compliance in near future. However, 72% of them didn’t foresee any changes in their allotted budget in the next couple of years.

Increasing security risks plus the rising costs of a data breach mandates the IT managers to concentrate more on security procedures. The overall effect on the organization is stretched financial and human resources. Automation can carry out many administrative repetitive tasks leaving IT staff free for more human-oriented activities.
Because the benefits of automation frequently outweigh the costs, it is evident that the world will see a greater shift toward automation in the future.
2. Securing the supply chain
Deloitte reported that an average of 57% of the organizations had a cybersecurity risk program to monitor and track the security posture of their partners and suppliers.

Organizations today have taken their business to a global level, thereby increasing the facets of supply chain management. While this helps expand the organization’s operations, the attack surface also increases massively. As the organization grows, it must ascertain whether its suppliers and partners are following appropriate cybersecurity hygiene.
IBM’s Cost of Data Breach 2022 report also found that 19% of the breaches resulted from supply chain attacks. Moreover, A supply chain breach took, on average, 26 days longer to identify and contain than the global average. These astonishing figures imply the importance of security and compliance in supply chain management.
These statistics reinstate that when you design your security and compliance processes with a premise of a certain breach, your defenses become stronger.
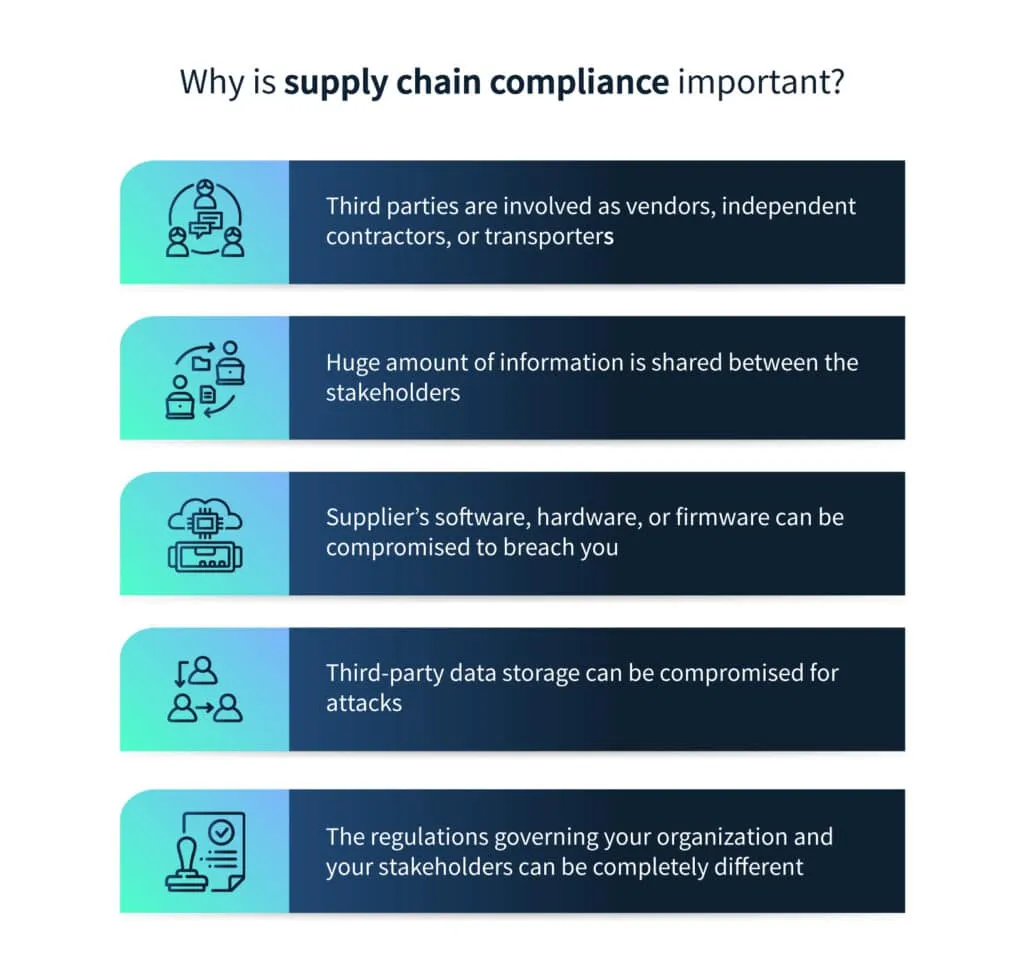
Assessing and controlling the risk on this scale becomes a complex task, particularly if your suppliers are not on the same page as you regarding the importance of security, including risk monitoring, control implementation, and cloud monitoring.
3. Tightening the regulatory requirements
In December 2022, US President Biden signed the National Defence Authorization Act (NDAA). The highlight of the Act is the Federal Risk and Authorization Management Program (FedRAMP) Authorization Act, which formalizes cybersecurity certification that cloud service providers (CSPs) are required to obtain prior to working with the United States government.
Additionally, the California Consumer Privacy Act (CCPA), which came into effect on January 1, 2020, is amended to become the California Privacy Rights Act (CPRA). Also called the CCPA 2.0, the CPRA is expected to become a potential model for other states, including Nevada and Maine.
Moreover, in addition to the US, other countries like India, New Zealand, Canada, Pakistan, and UAE have either updated or introduced new data protection laws.
As a business owner, you must be aware of the laws and regulations that affect you. You must be aware of the market you are working in and the location of your consumers. Awareness is the only way to remain relevant in the year to come.
4. The rising importance of risk management
Regulations and frameworks are regularly undergoing changes to keep the citizens’ data private despite increasing cyber threats and to stay relevant with the changing digital landscape.
The National Institute of Standards and Technology Cybersecurity Framework (NIST CSF) was first issued in 2014 and aimed at critical infrastructure providers. This was Version 1.0. However, in 2018, Version 1.1 was announced and made publicly available. The latest version included changes in
- guidance on how to perform self-assessments,
- additional detail on supply chain risk management,
- guidance on how to interact with supply chain stakeholders, and
- encourages a vulnerability disclosure process.
The American Institute of Certified Public Accountants (AICPA) first issued System and Organization Controls (SOC) 1, then issued SOC 2, and the latest one SOC 3. AICPA iterates on the importance of risk management in the compliance process of an organization. A typical audit today includes risk assessment, compliance management, and added verification at the discretion of the management.
5. Zero-trust business architecture

The principle of least privilege has been a building block for almost all infosec frameworks. But as we shift to more modern tech stack across the world, a zero-trust architecture helps you comply with this mandate more effectively.
Zero-trust business architecture is based on providing information only to the people or resources who need it to perform their duties. It ensures that all the data assets are discovered and recorded. As the data flow visibility increases, breaching it will become more complex.
In the unfortunate event of a breach, the organization can prove to its customers, regulators, auditors, and even courts that it has taken adequate steps to maintain data privacy. This model also enables organization to observe the movement of data and to identify and stop the breach sooner.
If you own a small or medium-sized business (SMB) and think that zero-trust architecture is not for you, think again. The following steps can simplify the zero-trust model for you:
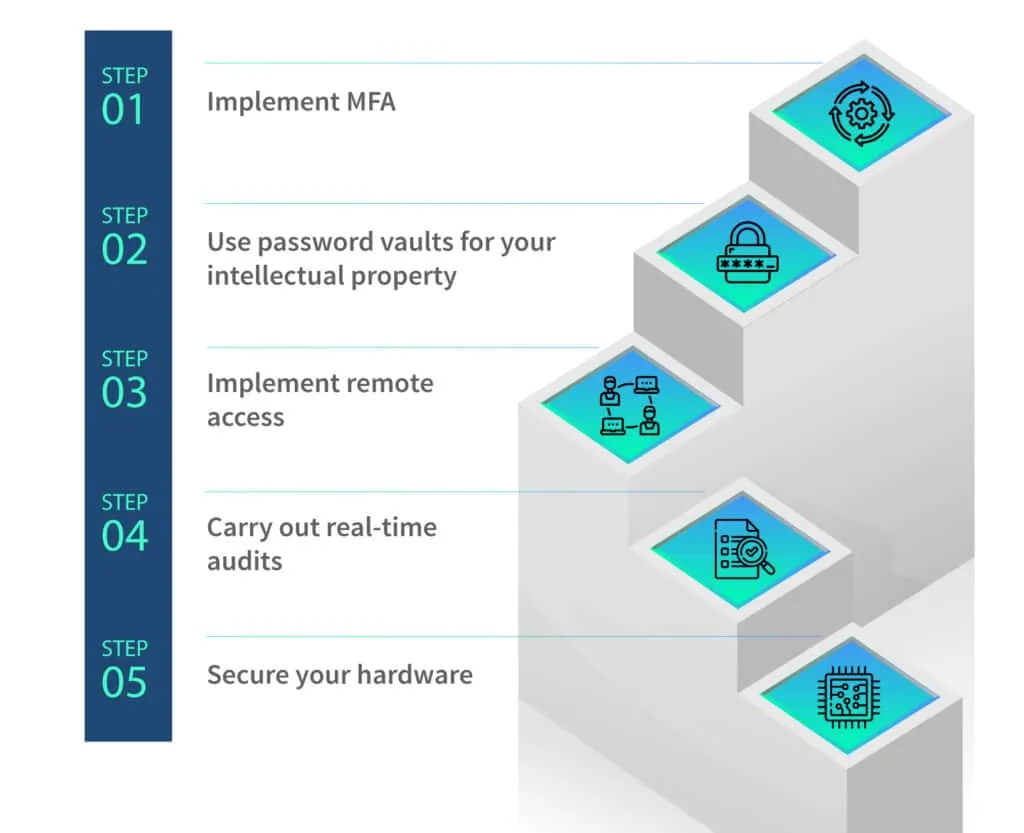
- Implement multi-factor authentication (MFA) in every account, whether it is an internal employee or an external contractor. MFA helps you reduce the chances of unauthorized data access.
- If you have highly sensitive data like patents, designs, or formulas to protect, you must use digital lockers, known as password vaults. These vaults can protect intellectual property (IP) by providing passwords to authorized people only after thorough identification.
- Implement secure remote access to ensure that no unauthorized person can access your systems. By segregating the data according to the level of security required, you can restrict its access to limited audiences.
- Real-time audits should be conducted to verify whether all relevant checks are in place. If you observe an employee accessing the data above their security clearance level, you must take concrete steps to resolve the issue.
- Hardware security is an integral part of the zero-trust architecture and must not be compromised. The stakeholders must be able to log in from their official devices only. The use of open networks must be strictly discouraged. Sharing passwords and data among employees might result in a serious cybersecurity flaw. Therefore, employees should be trained to follow the rules.
6. Compliance training programs
IBM identified that there are two most common reasons why organizations fall prey to data breaches, and these are technology failure and human error. IT failures like loss of data due to failure in an organization’s computer systems were responsible for 24% of the data breaches while 21% of the breaches were caused by a negligent employee or a contractor. Effective employee training can reduce the data breach cost by $247,758.
In order to reduce security risks, an organization must train and re-train its employees. You must remember how crucial it is to explain to your employees the cost of ignoring the compliance processes. As the organization grows, training tends to become less and less manageable. However, Scrut Automation can help you train your employees the way you want.
You can select a program of your choice and track your employees’ progress. Our employee training program helps organizations reduce manual effort by using pre-recorded training sessions, sending automated email reminders, and tracking the progress of your employees through a single-window platform.
7. Governance, Risk, and Compliance (GRC) partners
36% of the respondents in the Accenture survey claim that a lack of sufficient organizational stature in compliance structure poses a serious impediment to strengthening compliance.
New privacy laws are being introduced regularly to improve citizens’ data privacy making it difficult for organizations to keep up with the regulations while carrying on their operations.
The result – chaos in compliance.
An obvious answer to the problem would be hiring an outside agency to help you with governance, risk, and compliance processes. Organizations must secure their information systems and protect customers’ personally identifiable information (PII). A breach can result in penalties that might become too high for the organization to bear.
A reliable GRC provider can reduce your workload so that you can concentrate on activities that maximize profits without compromising on the quality of security processes you implement in your organization. A true balance is needed between achieving compliance certification with control monitoring and the growth of the business.
Conclusion
Compliance is no longer a distant reality in 2023, every organization with the right knowledge, tools, and time can achieve it. However, compliance in itself will not provide overall security, it is simply a by-product of security. There are several practices, including continuous cloud monitoring and risk management, that need to be followed for a protected infrastructure, and partnering with a compliance automation platform like Scrut might just be the right choice.
Conquering the compliance challenge can be simpler and faster with a partner like Srcrut. Book a demo with our experts to learn more about how Scrut can assist you in being compliant with different regulations in 2023.
The top three compliance challenges organizations face while pursuing compliance with industry frameworks are a lack of knowledge about compliance procedures, shortage of talent in the world, markets, and high compliance costs.
According to CrowdStrike, the three most critical areas for enterprise cybersecurity are: 1. Endpoints and cloud workloads – As per the IBM report, 17% of the breaches had cloud misconfiguration as an initial vector. 2. Identity – Initial vector for 19% of the breaches was compromised credentials. 3. Data – The average total cost of a data breach is $4.35 million.
Forbes predicted that phishing, malware, and supply chain or threat party threats would be the top cybersecurity threats to protect your organization from in 2023. With an expansive and attractive attack surface comes a high risk of data breaches, making continuous monitoring a necessity for organizations.





































