CMMC training guide for continuous compliance

The journey into the Cybersecurity Maturity Model Certification (CMMC 2.0) framework assumes new urgency following the effective date of the CMMC Final Rule in November 2025. This regulatory shift mandates stricter requirements for Department of Defense (DoD) contractors to secure national assets.
As we navigate the terrain of compliance, we find the vulnerability often lies not in complex systems, but at the endpoint: the individual. The scale of the threat underscores this urgency; the FBI's 2024 Internet Crime Report documented victim losses exceeding $16.6 billion in a single year (a 33% increase from the previous year), highlighting the absolute necessity of robust Controlled Unclassified Information (CUI) protection.
Compliance cannot be achieved through a one-time effort; it is a continuous imperative. Therefore, effective CMMC training becomes the linchpin of a perpetual compliance posture. Organizations must implement ongoing, role-based training that is automatically updated to reflect the latest CMMC requirements, ensuring personnel are audit ready every single day.
What is CMMC training?
CMMC training is a systematic education program designed to align personnel behavior with the cybersecurity requirements mandated by the DoD. More than just a simple annual refresher, effective CMMC training serves to institutionalize a "security first" culture across the organization. The framework itself organizes security controls across three CMMC levels: Foundational (Level 1), Advanced (Level 2), and Expert (Level 3).
The corresponding training is layered, addressing the differing needs at each tier. For Level 1, the focus is often on basic cybersecurity awareness and hygiene for protecting Federal Contract Information (FCI). However, as organizations progress to Levels 2 and 3, training evolves to become role-based, detailing specific procedures to safeguard CUI and managing complex threat scenarios. This targeted approach ensures that every employee understands their specific contribution to continuous compliance and overall organizational readiness for CMMC assessments.
Why is CMMC training required under CMMC 2.0
The mandate for continuous employee training is a non-negotiable CMMC requirement, rooted firmly in key governmental standards that underpin the CMMC 2.0 program. For CMMC Level 1, the requirement to implement basic safeguards for Federal Contract Information is driven by FAR 52.204-21. These requirements focus on fundamental cyber hygiene practices such as access control, system configuration, and physical protection. However, FAR 52.204-21 does not explicitly mandate security awareness training or user education — those expectations appear in higher maturity levels aligned to NIST SP 800-171.
At the Advanced Level, CMMC 2.0 aligns fully with NIST SP 800-171, which includes a dedicated control family for Awareness and Training. These explicit training requirements compel organizations to implement security awareness training, including crucial incident reporting awareness, on an annual basis, to drastically reduce the costly risk of human error.
Furthermore, training compliance directly impacts the organization’s ability to remain eligible for contracts after the CMMC Final Rule takes effect. An incomplete or ineffective training program represents unmet controls, resulting in lost points from the maximum possible score of +110 recorded in the Supplier Performance Risk System (SPRS). These gaps necessitate a Plan of Action & Milestones (POA&M) and signal a deficient cybersecurity posture during the assessment cycle.
Types of training required for CMMC 2.0
The tiered structure of CMMC 2.0 guides our exploration into the necessary training protocols, ensuring that the level of personnel proficiency is commensurate with the sensitivity of the information handled. The required training is broken down into two compliance levels and a specialized component, ensuring organizational resilience is built from the ground up.
Level 1 training requirements
For organizations handling FCI at CMMC Level 1, training typically focuses on basic security awareness and cyber hygiene. However, it is essential to note that FAR 52.204-21’s 17 basic safeguarding requirements do not explicitly mandate security awareness training. Instead, these practices are adopted voluntarily to support Level 1’s intent and reduce avoidable human-error risks. This foundational education must equip every user to serve as a capable digital safeguard.
Core topics include recognizing and avoiding common deceptive tactics, such as phishing, understanding the proper handling of FCI within defined information systems, and cultivating vigilance against risky behaviors, including unauthorized software installation. Crucially, this training must instill a sense of accountability by emphasizing proactive incident reporting of suspicious activity, transforming every employee into an active participant in organizational defense.
Level 2 training requirements
Organizations progressing to CMMC Level 2 must protect CUI and, therefore, must implement the 110 practices of NIST SP 800-171. This necessitates a substantial elevation of the CMMC training curriculum. The expanded requirements ensure personnel are versed in explicit CUI handling procedures, including marking, transmission, and storage protocols.
Furthermore, a dedicated component on insider threat awareness is required, training personnel to recognize and report indicators of potential malicious or negligent insider activity. This level also incorporates secure configuration habits and specific rules derived from the NIST 800-171 framework, covering areas like media protection and secure system development.
Level 3 training requirements
Achieving CMMC Level 3, the Expert designation, involves implementing controls based on NIST SP 800-172. This requires training to evolve from defensive compliance to proactive threat mitigation. The curriculum for CMMC Level 3 is fundamentally an extension of the role-based training from Level 2, focusing on the highly specialized technical skills needed to execute and maintain the advanced controls.
This training is targeted at expert personnel in security and IT operations, covering sophisticated procedures like advanced continuous monitoring, enhanced logging analysis, forensic readiness, and robust configuration control. The objective is to ensure that the personnel responsible for the most sensitive environments possess the deep technical competence required for effective, proactive CUI protection against advanced persistent threats.
Role-based training
Beyond the mandatory general awareness, the NIST SP 800-171 requirements demand specific role-based training. This recognizes that an administrator’s responsibilities differ vastly from those of an executive. System administrators and security teams, for instance, require deep training on audit logging, incident response framework execution, and continuous monitoring procedures.
Developers must be trained in secure coding practices and configuration management rules tied to development and testing environments. Similarly, executives require tailored training on risk management, supply chain security, and the governance processes necessary to sustain continuous compliance and maintain a perpetual audit readiness state. This strategic, differentiated approach ensures technical competence aligns precisely with functional duty.
This revision uses short, descriptive headings for each component, making the structural requirements of a strong CMMC training program clear at a glance.
What a strong CMMC training program should include
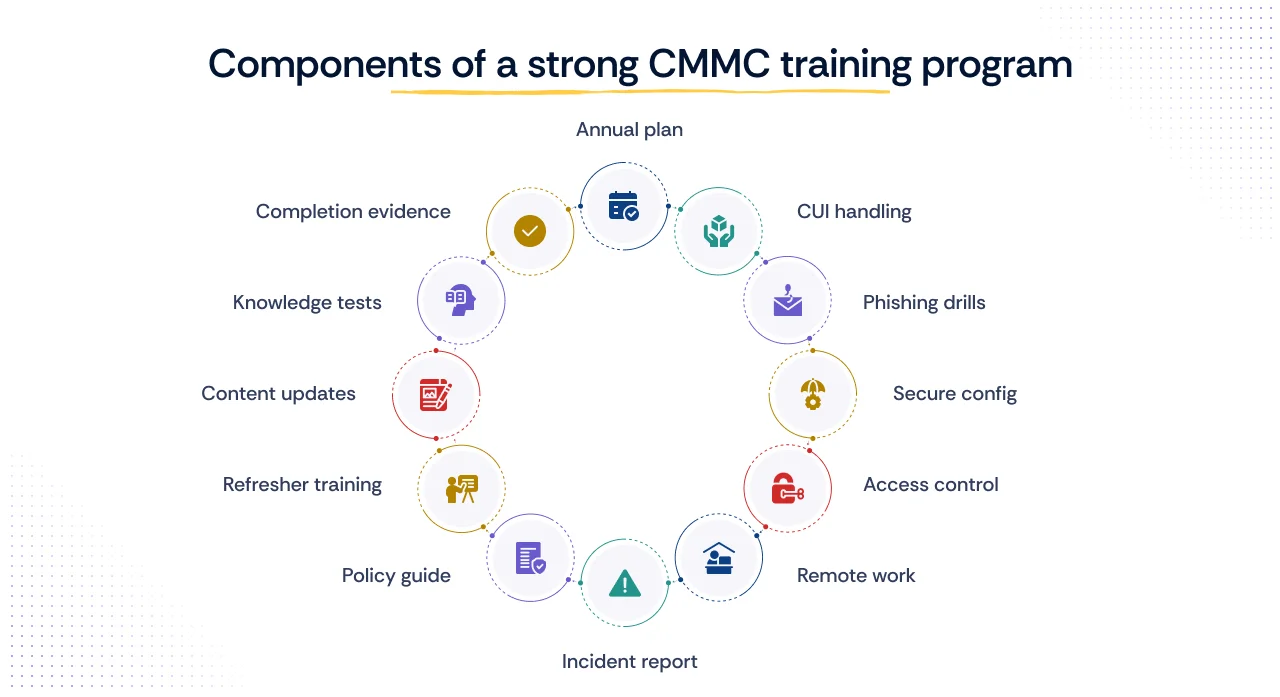
As we delve into the structure of an effective CMMC training program, it becomes clear that compliance requires more than mere annual participation; it demands a measurable, sustained culture of secure behavior.
For organizations pursuing continuous compliance under CMMC 2.0, the training architecture must be designed to mitigate human error and provide irrefutable evidence of proficiency. A high-performing program integrates the following critical elements:
- Annual plan: The program must be founded upon a structured annual training plan that defines the scope of required proficiency for all personnel throughout the fiscal year.
- CUI handling: Mandatory CUI handling modules must be included to educate employees on the proper procedures for marking, storing, and transmitting CUI.
- Phishing drills: The curriculum should integrate continuous security exercises, such as phishing simulations, to test and sharpen personnel vigilance against common social engineering tactics.
- Secure config: Training must address secure configuration basics, ensuring personnel understand the system boundaries and the rules governing equipment and software setup.
- Access control: Comprehensive instruction on access control awareness must detail least privilege principles and the security protocols for granting and managing permissions to sensitive information systems.
- Remote work: Dedicated modules on secure remote work practices are essential to address the expanded attack surface introduced by geographically dispersed teams.
- Incident report: Personnel must be thoroughly trained in detailed incident reporting steps, guaranteeing rapid and consistent reaction to all suspected security events.
- Policy guide: The training must encompass specific policy training, ensuring employees understand how organizational security governance connects directly to their daily operational tasks.
- Refresher training: NIST SP 800-171 requires security awareness training at least once per year. Organizations may choose to conduct additional refresher sessions throughout the year to reinforce key concepts, but increased frequency, such as quarterly updates, is an internal policy decision rather than a CMMC requirement.
- Content updates: The program requires agile mechanisms for content updates based on threats, allowing the curriculum to immediately reflect new intelligence or changes to the CMMC framework.
- Knowledge tests: Formal tests and assessments to prove understanding must be employed to verify knowledge transfer and generate objective metrics of employee competence for auditors.
- Completion evidence: Crucially, the system must generate auditable evidence of completion for every training instance and assessment, seamlessly integrating results with the organization's compliance platform.
By implementing these structural requirements, an organization transforms its workforce from a potential liability into its most formidable defensive asset, ensuring that the human element is always ready for CMMC assessment.
How to build a CMMC training plan for all levels

The creation of a robust CMMC training plan is a structured expedition, transforming compliance requirements into actionable steps for personnel at CMMC Level 1, CMMC Level 2, and CMMC Level 3. Our exploration outlines a seven-step roadmap designed for continuous compliance and audit readiness:
1. Map training to controls
The foundational step is to meticulously link every security requirement, from basic cyber hygiene (CMMC Level 1) to the CUI-handling controls of NIST SP 800-171 (CMMC Level 2), to specific training modules. This establishes a clear compliance checklist for the program.
2. Identify roles and responsibilities
Security training must be tailored. This step involves identifying all system user roles, from general users to administrators and developers, and assigning an appropriate, role-based curriculum based on their access and duties.
3. Build an annual and quarterly cadence
Establish the training frequency. While general awareness requires an annual training requirement, a more frequent quarterly cadence is necessary for high-risk roles or when preparing for a specific assessment.
4. Add simulations and practical tests
Move beyond passive learning by integrating practical elements like phishing simulations and knowledge assessments. This validates that employees possess the required secure behavior rather than just reviewing content.
5. Track evidence in one place
For audit readiness, a centralized system is essential. Training completion records, assessment scores, and attendance logs must be automatically collected, correlated, and tracked in a single compliance platform to generate auditable evidence of completion.
6. Review and update content
Compliance is not static. The plan must include a defined process to review and update content regularly based on changes in the CMMC Final Rule, evolving threat intelligence, or post-incident analysis.
7. Conduct leadership briefings
Security culture starts at the top. Regular leadership briefings must be held to report on training progress, compliance gaps, and the overall state of the human risk posture, ensuring executive accountability for the training initiative.
Implementing these steps ensures that the CMMC training plan is proactive, measurable, and perpetually ready for the assessment cycle.
Common mistakes that break CMMC training compliance and how to avoid them
In the pursuit of achieving CMMC certification, organizations often overlook critical operational details regarding the human element, leading to common CMMC compliance failures and exposing vulnerabilities during assessments. This exploration outlines typical CMMC audit mistakes related to training and offers actionable strategies to sustain an audit ready posture.
To navigate the intricacies of CMMC effectively, organizations must transform training from a static event into a managed, continuous system. Leveraging automation ensures that the evidence of human competence is as reliable as the security technology protecting CUI.
How CMMC training helps you stay audit ready
The core discovery from our exploration is that effective training is the fuel for maintaining a state of being audit ready, moving the organization beyond periodic preparation to continuous compliance. Comprehensive training achieves this readiness through several crucial pathways:
- Reduces POA&M findings: By transforming personnel into active security participants, comprehensive training directly reduces findings related to human error, which are frequent sources of POA&M requirements.
- Improves SPRS score: Meeting the Awareness and Training controls of NIST SP 800-171 immediately contributes valuable points to your organization’s SPRS score, bolstering your objective cybersecurity posture recorded by the DoD.
- Supports annual affirmations: Verifiable training records provide crucial evidence to support the mandatory annual affirmations required under CMMC 2.0.
- Strengthens day-to-day defense: On a day-to-day basis, this educated vigilance strengthens defenses by reducing incidents and improving incident reporting, creating a proactive shield for sensitive data.
- Ensures documented compliance: Ultimately, by automating the delivery and evidence collection of the training program, organizations ensure that the human element is always current, documented, and fully compliant for auditors.
How Scrut supports CMMC training
The administrative burden of maintaining CMMC training compliance is significantly eased through CMMC automation platforms like Scrut. Scrut delivers effective CMMC training management by centralizing the entire process, ensuring every step is auditable.
The platform provides pre-built security and privacy courses, allowing you to tailor training based on specific employee roles and criticality to your security measures. Scrut facilitates seamless evidence collection by automatically logging training completion and assessment results. This capability links the human-centric controls, such as security awareness and device monitoring (e.g., hard drive encryption), directly to the CMMC framework.
By automating the tracking, reminders, and evidence collection for training and device compliance, Scrut drastically reduces the manual labor involved in audit preparation, ensuring your organization maintains continuous compliance effortlessly and remains perpetually audit ready.
Ready to transform your security awareness program into an automated defense asset? Explore how Scrut’s compliance platform can simplify your CMMC training and make audit readiness your everyday reality.

FAQs
1. Does CMMC training apply to all CMMC levels?
Yes. CMMC training is mandatory across all CMMC levels. Level 1 requires basic security awareness for FCI, while Levels 2 and 3 require advanced, role-based training aligned with NIST standards to protect CUI.
2. What is the core difference between Level 1 and Level 2 training content?
CMMC Level 1 training focuses on basic cyber hygiene and FCI protection. CMMC Level 2 training expands to cover detailed CUI protection protocols, secure configurations, and mandatory insider threat awareness as required by NIST SP 800-171.
3. Why is training documentation essential for the SPRS score?
Training records are crucial evidence for the Awareness and Training controls. Lack of verifiable documentation leads to lost points, resulting in a lower SPRS score and potential POA&M requirements, which impacts your eligibility.
4. Is annual training sufficient to maintain CMMC compliance?
No. Compliance necessitates a state of continuous compliance. While annual training covers the base requirement, a strong program includes mandatory quarterly refresher training and practical simulations to stay audit-ready against evolving threats.
5. How does CMMC training reduce the risk of audit failure?
Effective, measurable training directly reduces human error, a frequent cause of CMMC audit mistakes. It minimizes control deficiencies, helps clear POA&M findings, and provides the documentation needed to verify personnel competence during the assessment cycle.


















