CMMC 2.0 compliance timelines: Crucial deadlines to avoid contract ineligibility

The long period of anticipation is officially over. The Cybersecurity Maturity Model Certification (CMMC) 2.0 has moved decisively from rulemaking to reality, marking the beginning of a new, mandatory era for the entire Defense Industrial Base (DIB). The Department of Defense (DoD) published the final Defense Federal Acquisition Regulation Supplement (DFARS) Acquisition Rule (48 CFR) in the Federal Register on September 10, 2025, laying the legal groundwork for enforcement.
This means every organization handling Federal Contract Information (FCI) or Controlled Unclassified Information (CUI) must now face the most urgent date on the calendar: November 10, 2025. This is the effective date when CMMC compliance requirements will officially begin appearing in new DoD solicitations and contracts. This transition transforms cybersecurity from a "check-the-box" self-attestation exercise into a validated condition of contract eligibility.
The sheer scale of this mandate is monumental: the DoD estimates that approximately 8,350 medium and large entities will be required to meet the CMMC Level 2 third-party assessment (C3PAO) requirements as a condition of contract award. This official figure underscores the massive logistical and security commitment now required across the DIB.
This guide serves as your essential map for this compliance expedition. We will precisely chart the multi-year phased rollout of CMMC 2.0 and outline the immediate, proactive preparation steps required to ensure your organization not only meets this regulatory threshold but gains a competitive edge through demonstrable, continuous compliance.
The mandatory CMMC timeline: Key dates
The most pressing question for the DIB is not if CMMC will be required, but when. The final DFARS Acquisition Rule formalizes a rigorous, four-phase rollout schedule beginning in November 2025 and culminating in full implementation by late 2028. This phased introduction is the explicit window of opportunity for organizations to align their security posture without jeopardizing contract eligibility.
November 10, 2025: The launch date (Phase 1 begins)
This is the critical effective date for the DFARS rule (48 CFR), formally enabling Contracting Officers to include CMMC requirements in all new solicitations and applicable contracts.
- Requirement focus: CMMC Level 1 (Self-Assessment) and Level 2 (Self-Assessment) requirements become conditions of contract award.
- DoD discretion: The DoD may, at its discretion, immediately require the more stringent CMMC Level 2 (C3PAO Certification) for certain prioritized contracts.
- The implication: Given that achieving L2 compliance typically requires 6 to 12 months of dedicated work, any company wishing to bid on CUI-handling contracts starting late 2025 or early 2026 must have its gap analysis completed and its remediation roadmap actively underway today.
November 10, 2026: Third-party validation escalates (Phase 2 begins)
Beginning one calendar year after the effective date, the compliance expectations are significantly heightened across the DIB.
- Requirement focus: The requirement for CMMC Level 2 (C3PAO certification) becomes mandatory for a wider range of applicable contracts as a condition of award.
- DoD discretion: The DoD may also introduce Level 3 (DIBCAC) assessment requirements for select high-priority programs.
- The implication: For organizations handling CUI, the shift from possible self-assessment to mandatory third-party assessment is the inflection point. Certification requires a C3PAO assessment every three years, and the limited availability of C3PAOs demands early scheduling.
November 10, 2027: L2 certification becomes universal (Phase 3 begins)
This phase closes the door on earlier assessment flexibility, ensuring broad compliance across the supply chain.
- Requirement focus: CMMC Level 2 (C3PAO certification) is required not only for new contract awards but also as a condition for exercising option periods on contracts awarded after the initial effective date (Nov 10, 2025).
- Level 3: Mandatory Level 3 (DIBCAC) assessment requirements are included in all applicable solicitations as a condition of award, though the DoD retains the discretion to delay this to an option period.
- The implication: Even existing contracts become subject to the certification requirement, validating that compliance is continuous.
November 10, 2028: Full implementation (Phase 4 begins)
This date marks the successful culmination of the three-year phase-in period.
- Requirement focus: Full implementation of all CMMC Program requirements is mandated for all applicable DoD solicitations and contracts, including option periods.
- The implication: By this point, CMMC compliance will be a standardized, baseline cost of doing business within the DIB. The failure to maintain a current CMMC status in SPRS will result in ineligibility to compete for or continue work on virtually all CUI and FCI contracts.
The clarity of this timeline is an undeniable call to action. Given the 6 to 12 months needed for Level 2 readiness, the time to begin your preparation is not next year, but today.
CMMC readiness: The 6-step timeline, time estimates, and key roles for certification
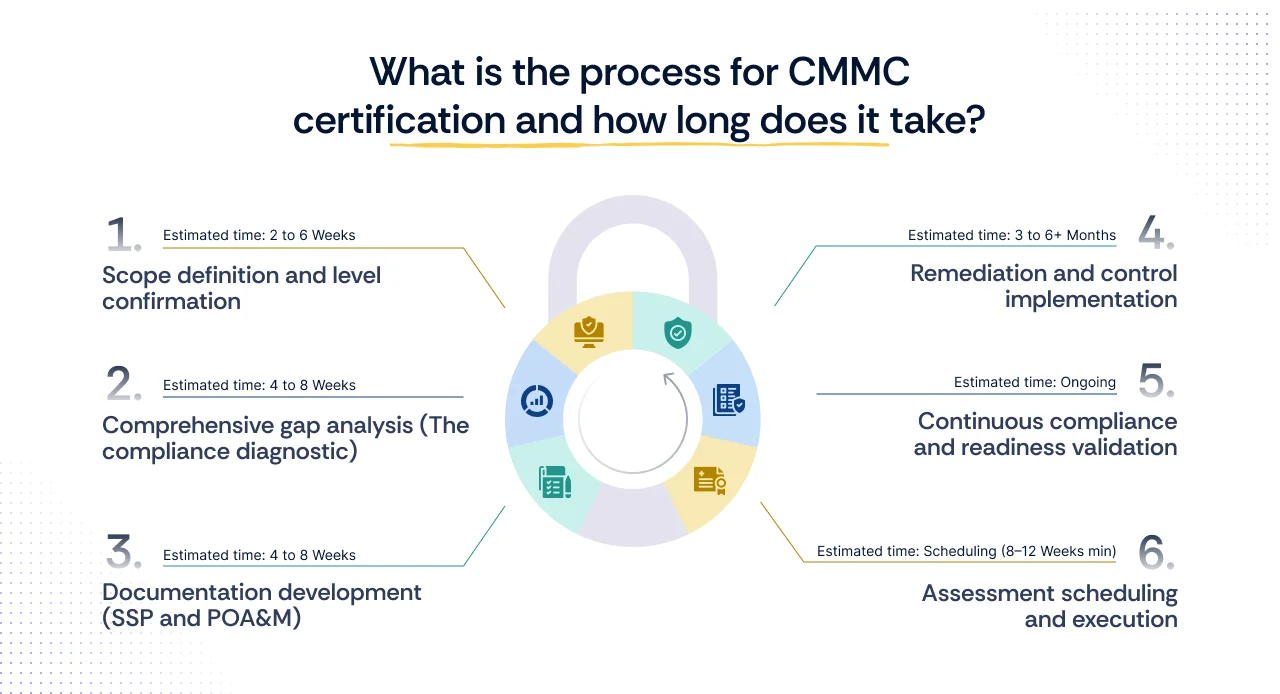
The most frequent question asked by DIB contractors is precisely how much time to allocate to the readiness journey. While the overall timeline varies (30-90 days for Level 1, 6-12 months for Level 2), strategic preparation requires breaking this down into concrete, time-bound steps with clear ownership.
Step 1: Scope definition and level confirmation
This foundational step sets the boundaries for all subsequent work, preventing unnecessary time and resource expenditure on out-of-scope assets.
- Responsible roles: Senior Leadership (Affirming Official), Compliance Officer, IT Leadership.
- Estimated time: 2 to 6 Weeks (for CMMC Level 2 scoping in a small-to-midsize DIB company).
- Required action: Identify and map every system, user, process, and external service provider (ESP) that processes, stores, or transmits FCI or CUI. The core goal is to define the "CMMC Assessment Scope" (CAS) and determine if network segmentation (enclave strategy) can significantly reduce the complexity and cost of the audit.
Step 2: Comprehensive gap analysis (The compliance diagnostic)
The gap analysis serves as the detailed blueprint for your remediation efforts, comparing your current cybersecurity posture against the full set of CMMC requirements.
- Responsible roles: Compliance Officer, IT Security Team, and often an External Registered provider organization (RPO) or an automated GRC Platform.
- Estimated time: 4 to 8 Weeks. This period involves rigorous evidence collection, control mapping (against NIST SP 800-171's 110 controls), and detailed reporting of deficiencies.
- Required action: Perform a control-by-control assessment to identify non-compliant items. This phase directly informs the Plan of Action and Milestones (POA&M), transforming abstract requirements into concrete tasks. Leveraging a GRC platform dramatically accelerates evidence collection and eliminates manual spreadsheet tracking.
Step 3: Documentation development (SSP and POA&M)
Before any audit can commence, the organization must articulate how it meets the CMMC requirements in the mandatory System Security Plan (SSP) and what remains to be done in the POA&M.
- Responsible roles: Compliance Officer, Technical Writers, Affirming Official (for final approval).
- Estimated time: 4 to 8 Weeks. Writing the SSP and POA&M is a highly detailed effort; auditors demand implementation narratives, not just policy statements.
- Required action: The SSP must describe the system boundary, its environment, and how every control objective is met. The POA&M must list remaining gaps (if Level 2/3), assign ownership, specify resources, and include a firm completion deadline within the strict 180-day limit.
Step 4: Remediation and control implementation
This is the most variable and time-consuming phase, demanding significant investment in technology and organizational change.
- Responsible roles: IT Engineering, Security Operations, HR (for training), and Budget/Finance.
- Estimated time: 3 to 6+ months. The timeline is dictated by the severity of the gaps: implementing MFA (basic fix) takes weeks; deploying a Security Information and Event Management (SIEM) system (complex fix) and securing operational technology (OT) takes months.
- Required action: Close all gaps identified in the POA&M. Critical requirements (those disallowed on a POA&M) must be prioritized and implemented immediately, while non-critical controls must be closed within the 180-day window to achieve final certification.
Step 5: Continuous compliance and readiness validation
CMMC is a three-year certification, but compliance is continuous. This phase ensures the implemented controls are operating effectively and generating verifiable, auditable evidence.
- Responsible roles: Security Operations Team, Compliance Team, and continuous monitoring of GRC Technology.
- Estimated time: Ongoing. A minimum of 1 to 2 months of control operation is often needed to generate sufficient evidence (logs, audit trails) prior to a formal assessment.
- Required action: Implement automated monitoring for key controls. Organizations must file an annual affirmation with the DoD certifying ongoing compliance. This continuous validation is where automation tools prove indispensable for maintaining audit readiness 365 days a year.
Step 6: Assessment scheduling and execution
The final step is the formal audit by the appropriate body, the C3PAO or DIBCAC.
- Responsible roles: C3PAO Lead Assessor, Client-side Affirming Official, and internal Subject Matter Experts (SMEs).
- Estimated time: Scheduling (8–12 Weeks minimum); Assessment (1–2 Weeks).
- Required action: Due to the limited pool of C3PAOs, organizations should begin engagement well in advance. The assessment itself involves documentation review, personnel interviews, and technical verification, culminating in the issuance of a conditional or final CMMC Status in SPRS.
Do all CMMC levels take different timelines to complete?
Yes, the time required to achieve CMMC compliance differs significantly across the three maturity levels, as the complexity and number of security controls escalate with each tier. The timeline is primarily influenced by your current security posture (the "gap") and the required assessment type.
Here is a breakdown of the typical time required for each CMMC level, drawing on industry standard estimates and the specific requirements mandated by the DoD's final rules:
CMMC Level 1: Foundational cybersecurity
- Why the short timeline? Level 1 requires implementing only 17 basic cyber hygiene practices based on 15 controls. For many organizations already maintaining a baseline security posture (unique user accounts, anti-virus software), the effort focuses mainly on formalizing existing practices and compiling the required documentation (SSP, policies) to support the annual self-assessment.
- Time focus: The 30 to 90 days are mostly spent on scoping, validating that the 15 controls are fully implemented (since POA&Ms are not permitted), and ensuring the correct senior leader performs the affirmation in SPRS.
CMMC Level 2: Advanced cybersecurity
- Why the long timeline? Level 2 demands adherence to all 110 controls of NIST SP 800-171, which govern comprehensive technical and procedural aspects of cybersecurity (e.g., Multi-Factor Authentication, continuous monitoring, robust incident response). The sheer volume and technical complexity of these controls require substantial work.
- Time focus: The estimated 6 to 12 months typically encompasses:
- Gap analysis and documentation: 2 to 8 weeks.
- Remediation and implementation (The longest phase): 3 to 6 months or more, depending on the need for new technology acquisition (like SIEM systems) or significant network restructuring.
- Readiness and assessment: 1 to 3 months, including scheduling the triennial assessment (which can take several weeks due to limited C3PAO availability) and undergoing the audit itself.
CMMC Level 3: Expert cybersecurity
- Why the extended timeline? Level 3 is the most rigorous, building on the 110 NIST SP 800-171 controls with an additional 24 enhanced controls from NIST SP 800-172. These controls focus on proactive defense against Advanced Persistent Threats (APTs) and require advanced capabilities like continuous threat hunting.
- Time focus: The 18+ month timeline reflects the need for advanced technical capabilities, achieving the mandatory Final CMMC Level 2 (C3PAO) status as a prerequisite, and preparing for the government-led DIBCAC assessment. The implementation and institutionalization of these controls demand deep architectural and operational maturity.
What are the timeline expectations for different organization sizes
CMMC compliance timelines absolutely differ across levels and, crucially, by the size and complexity of the organization. The compliance challenge is fundamentally a measure of the gap between your current security posture and the required CMMC controls.
Based on industry estimates and preparation phases, here is a breakdown of the typical timeline expectations by organizational size:
Small businesses (e.g., < 50 employees, Level 1 or basic Level 2 scope)
Small businesses often benefit from smaller, simpler IT environments, allowing for faster policy changes and remediation implementation.
- Total estimated CMMC timeline: 8 to 18 months for Level 2 Certification Readiness. (Level 1 readiness is much quicker, potentially 30-90 days).
- Preparation and remediation focus: If starting with low security maturity, expect 6-12 months to understand requirements, perform gap analysis, implement the 110 NIST SP 800-171 controls, and develop the required documentation (SSP).
- Assessment and certification: Level 2 C3PAO assessment scheduling and execution usually takes 1-3 months, plus the crucial window of up to 180 days for POA&M closure, if needed.
Medium businesses (e.g., 50–500 employees, standard Level 2 scope)
Medium-sized organizations face a significant jump in complexity due to more users, diverse systems, and potential cross-departmental data flows, requiring robust policy implementation.
- Total estimated CMMC timeline: 12 to 24 months for Level 2 Certification.
- Preparation and remediation focus: A timeline of 9-18 months is common. This involves a more complex gap analysis, likely significant technical control implementations or upgrades (like enterprise-wide MFA or SIEM), and extensive policy development and evidence gathering across more systems and users.
- Assessment and certification: The C3PAO assessment process (scheduling, assessment, reporting, and POA&M closure) typically requires 3–5 months.
Large businesses (e.g., 500+ employees, complex Level 2 or Level 3 scope)
Large enterprises, especially those with multiple locations, global operations, and legacy systems, face the longest and most resource-intensive compliance journeys.
- Total Estimated CMMC timeline: 18 to 36+ months.
- Preparation and remediation focus: Expect preparation and remediation to take 12-24+ months. This is due to complex environments, coordinating remediation across large, siloed teams, managing legacy infrastructure, and the extensive time required for comprehensive documentation. If pursuing Level 3, the implementation of the additional 24 NIST SP 800-172 controls will extend this timeline further.
- Assessment and certification: The Level 2 C3PAO or Level 3 DIBCAC assessment processes can take 4–6+ months, factoring in the inherent complexity of the environment and any potential remediation required under a POA&M.
In every scenario, early scoping, aggressive remediation, and leveraging technology for continuous compliance are the only ways to compress these timelines and stay ahead of the phased rollout deadlines.
Accelerate your CMMC readiness with Scrut
The rigid phase-in deadlines, starting in November 2025, transform CMMC compliance into an urgent, continuous operational requirement, not a one-time audit. Organizations that embrace this shift gain a decisive advantage.
By leveraging Scrut’s continuous compliance automation, DIB contractors can drastically compress the 6-12 month readiness timeline. Scrut streamlines scoping, automates evidence collection, and maintains a real-time audit trail, ensuring your System Security Plan (SSP) and POA&M are perpetually audit-ready. Don't risk disqualification from crucial DoD contracts by manually tracking compliance.

Frequently Asked Questions (FAQ)
What are the 4 official phases of CMMC rollout?
The rollout begins November 10, 2025, and progresses annually:
- Phase 1 (Nov 2025): L1/L2 Self-Assessments appear in contracts.
- Phase 2 (Nov 2026): Mandatory L2 (C3PAO Certification) for applicable new contracts.
- Phase 3 (Nov 2027): L2 (C3PAO) required for contract option exercises; mandatory L3 (DIBCAC) requirements introduced.
- Phase 4 (Nov 2028): Full CMMC implementation across all applicable contracts.
How do POA&M deadlines affect CMMC certification?
POA&Ms are not allowed for Level 1. For Levels 2 and 3, they are strictly limited to non-critical controls and must be closed out via a closeout assessment within 180 days of receiving a Conditional CMMC Status. Failure to close them out results in automatic termination of the status and contract ineligibility.
How to schedule assessments amid limited C3PAO capacity?
Start early. Given the small number of C3PAOs relative to demand (estimated 8,350 entities requiring assessment), organizations should achieve audit-readiness (Steps 1-5) and book a C3PAO engagement 8–12 weeks in advance of their deadline to avoid significant delays.
What timeline challenges do small businesses/nonprofits face?
Small businesses primarily struggle with resource limitations (budget and personnel bandwidth), which stretch the typical 6-12 month readiness timeline. They also face early compliance pressure, as prime contractors often enforce the L2 C3PAO requirement on subcontractors ahead of the official DoD phases.
Will there be a grace period or extensions for small businesses?
No. There is no official grace period. The DoD mitigated the small business burden through the multi-year phased rollout and the allowance for self-assessment on certain contracts. If a contract requires a CMMC status on award, a lack of compliance means immediate ineligibility.
Which step in the CMMC process tends to take the longest?
Step 4: Remediation and Control Implementation (Estimated 3 to 6+ Months). This phase requires implementing new security technology, overhauling policies, and ensuring continuous evidence generation, which takes the most time and dedicated budget.
Are there different deadlines for prime contractors and subcontractors?
The official phase-in dates (Nov 2025–2028) apply to both. However, subcontractors face the fastest practical deadlines because prime contractors must verify a sub's CMMC status (flow-down requirement) before awarding a subcontract. This means the sub's deadline is often set by the prime, not the DoD's phase schedule.
If you increase the CMMC budget, will it speed up the process?
Yes, strategically. Increased budget, specifically allocated to expert RPO consulting and compliance automation tools like Scrut, can accelerate the Gap Analysis (Step 2), Documentation (Step 3), and Continuous Monitoring (Step 5), effectively compressing the overall 6-12 month timeline.