Secure DoD contracts: How to master CMMC controls and achieve audit readiness

The Defense Industrial Base (DIB) operates on a contested digital frontier, backed by immense fiscal responsibility. In Fiscal Year 2024 alone, the Department of Defense (DoD) awarded $402.66 billion in contracts, representing over half of all federal contracts, underscoring the vital importance of this sector. For organizations securing this massive national investment, compliance is not merely a preference; it is an imperative flow-down requirement.
As we explore this critical mandate, we confront the urgency of the Cybersecurity Maturity Model Certification (CMMC) 2.0 program against the backdrop of escalating global cyber threats. Sophisticated adversaries increasingly target the DIB's weakest links as a gateway to Controlled Unclassified Information (CUI). This vulnerability is compounded by documented readiness gaps: a recent analysis found that 62% of defense contractors lack the comprehensive governance controls necessary for certification success.
CMMC 2.0 is the DoD’s structural response, transforming security from a technical issue into a core Governance, Risk, and Compliance (GRC) strategy. To secure contract eligibility and protect CUI, DIB entities must now fully implement the framework's bedrock: the 110 security controls aligned with NIST SP 800-171. And that’s exactly what we will talk about in this blog – the CMMC controls.
What are CMMC controls?
CMMC controls are specific cybersecurity practices defined by the Department of Defense (DoD) to safeguard sensitive unclassified defense information across the supply chain. Essentially, they form the technical and procedural requirements necessary for a defense contractor to achieve certification and maintain eligibility for DoD contracts. These controls are not proprietary; rather, they draw their authority and substance from established federal security standards.
The CMMC 2.0 framework primarily leverages the NIST Special Publication (SP) 800-171, Revision 2 standard, which outlines 110 controls required to protect the confidentiality of Controlled Unclassified Information (CUI) in non-federal systems. These controls are grouped into 14 distinct security domains (control families), including Access Control, Configuration Management, and Identification and Authentication, ensuring a comprehensive and systematic approach to risk mitigation. These requirements are mandatory for DoD contractors and their suppliers (subcontractors) who handle CUI or, at the foundational level, Federal Contract Information (FCI). This application ensures that security requirements flow down through all tiers of the DIB.
What are the 14 CMMC Control Domains (Control Families)?
The 110 security controls that form the foundation of CMMC 2.0 Level 2 are strategically organized into 14 distinct control domains, or families. These domains, which align perfectly with the structure of NIST SP 800-171, ensure a holistic approach to securing CUI.
Each domain has group-related security requirements to address specific areas of risk, moving from foundational access rules to comprehensive incident response capabilities. This systematic grouping facilitates efficient implementation, auditing, and continuous monitoring of an organization's security posture across the entire scope of its operations.
The 14 Control Domains of CMMC 2.0 (NIST SP 800-171)
CMMC 2.0 Level 1: Foundational safeguarding
The CMMC 2.0 Level 1 represents the foundational level of cybersecurity maturity and applies to DIB organizations that only handle FCI. FCI is defined as information provided by or generated for the Government under a contract, not intended for public release. This level ensures basic cyber hygiene and requires the implementation of a specific set of security practices.
Key details for Level 1
- Scope: Applies to DIB companies that process, store, or transmit FCI but do not handle CUI.
- Controls: Requires the implementation of 1715 security controls (practices) drawn from Federal Acquisition Regulation (FAR) clause 52.204-21. The FAR is the primary regulation for all federal executive agency acquisitions. These controls are a subset of the full NIST SP 800-171 list.
- Assessment type: Annual Self-Assessment performed by the company's senior official. This self-assessment must be submitted annually to the DoD's Supplier Performance Risk System (SPRS). SPRS is the official system used by the DoD to monitor contractor performance and risk.
- Certification validity: The self-assessment attestation certification is valid for one year.
Foundational CMMC Level 1 controls (The 15 practices)
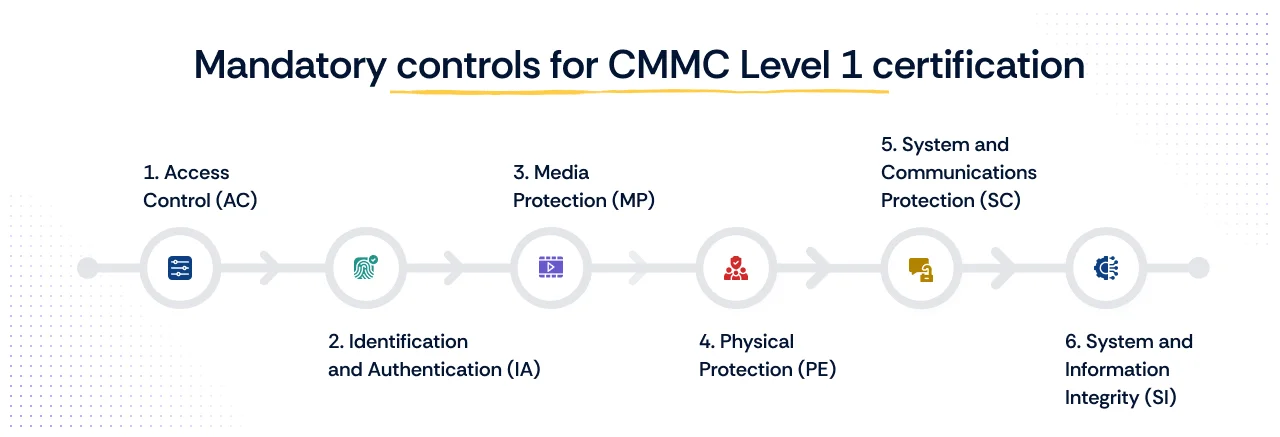
These controls are directly sourced from FAR 52.204-21.
1. Access Control (AC)
- Practice AC.L1-3.1.1: Limit information system access to authorized users, processes acting on behalf of authorized users, and devices (including other information systems).
- Practice AC.L1-3.1.2: Limit information system access to the types of transactions and functions that authorized users are permitted to execute.
2. Identification and Authentication (IA)
- Practice IA.L1-3.5.1: Identify information system users, processes acting on behalf of users, and devices.
- Practice IA.L1-3.5.2: Authenticate (e.g., verify the identity of) users, processes, or devices before allowing access to the information system.
3. Media Protection (MP)
- Practice MP.L1-3.8.3: Sanitize or destroy information system media containing FCI before disposal or release for reuse.
4. Physical Protection (PE)
- Practice PE.L1-3.10.1: Limit physical access to organizational information systems, equipment, and the respective operating environments to authorized individuals.
- Practice PE.L1-3.10.2: Protect and monitor the physical perimeter of organizational information systems.
- Practice PE.L1-3.10.3: Control and manage physical access devices (e.g., keys, smart cards, badges).
5. System and Communications Protection (SC)
- Practice SC.L1-3.13.1: Monitor, control, and protect organizational communications (i.e., information transmitted or received by organizational information systems) at the external boundaries and key internal boundaries of the information systems.
- Practice SC.L1-3.13.5: Implement sublicense restrictions to achieve the security objectives of the contract or order.
6. System and Information Integrity (SI)
- Practice SI.L1-3.14.1: Identify, report, and correct information flaws in a timely manner.
- Practice SI.L1-3.14.2: Provide protection from malicious code at appropriate locations within organizational information systems.
- Practice SI.L1-3.14.3: Update malicious code protection mechanisms when new releases are available and check the configurations of the mechanisms.
- Practice SI.L1-3.14.4: Perform periodic scans of the information system and real-time scans of files from external sources as files are downloaded, opened, or executed.
- Practice SI.L1-3.14.5: Monitor system security alerts and advisories and promptly take appropriate action in response.
CMMC 2.0 Level 2: Protecting Controlled Unclassified Information (CUI)
CMMC 2.0 Level 2 is the most critical and widely applicable maturity level, mandated for DIB organizations that handle CUI. This level transitions a company from basic cyber hygiene to a robust and institutionalized security program designed to effectively safeguard sensitive defense information.
Key details for Level 2
- Scope: Applies to DIB companies that process, store, or transmit CUI. This includes almost all DoD contractors and subcontractors involved in major acquisition programs.
- Controls: Requires the full implementation of the 110 security controls specified in NIST SP 800-171.
- Assessment type: The assessment type is split based on the criticality of the CUI being handled:
- Prioritized acquisitions: These contracts require a Triennial (every three years) CMMC Third-Party Assessment Organization (C3PAO) Assessment. The results are posted to SPRS.
- Non-prioritized acquisitions: These contracts allow for an Annual Self-Assessment by the company's senior official, which is submitted to SPRS.
- Certification validity:
- C3PAO Assessments are valid for three years.
- Self-assessments are valid for one year.
- POA&M usage: For CMMC Level 2, the use of Plans of Action and Milestones (POA&Ms) is permitted for a limited number of non-high-value controls, provided the remaining controls are met at the time of assessment. The DoD will specify the maximum allowable number of outstanding controls.
CMMC Level 2 controls: The 110 practices of NIST SP 800-171
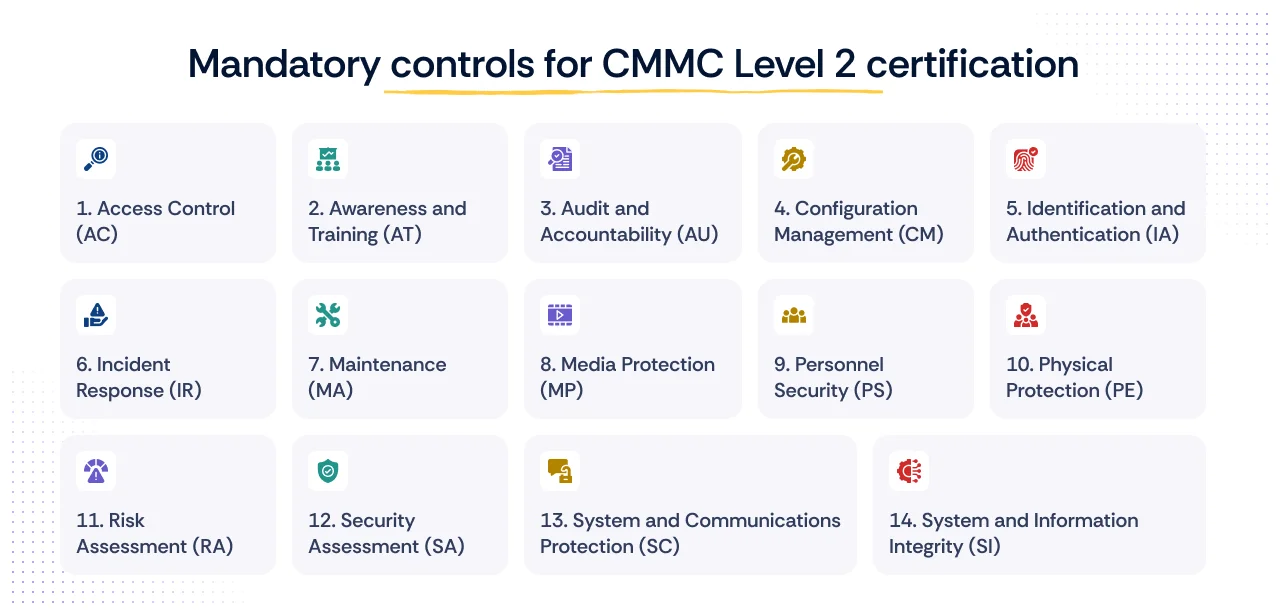
Level 2 requires the implementation of all 110 controls across the 14 control domains (families) previously discussed. Listing all 110 individually is impractical for a blog format, as the full list spans over 100 pages in the NIST publication.
Instead, the roadmap should focus on the strategic difference between Level 1 and Level 2, illustrating this through examples of the more rigorous, CUI-specific practices introduced in Level 2 within each domain.
1. Access Control (AC)
- Practice AC.L2-3.1.3: Control access to information systems by enforcing least privilege, separating duties, and restricting access to CUI based on the official duties of the individuals. (This moves beyond simply limiting access to requiring granular, role-based control).
- Practice AC.L2-3.1.7: Enforce approved authorizations for controlling the flow of CUI as specified by the authorizing official.
2. Awareness and Training (AT)
- Practice AT.L2-3.2.2: Provide security awareness training on potential personal risks associated with the transfer of CUI via social media and unauthorized communication methods. (Focuses training specifically on protecting CUI).
3. Audit and Accountability (AU)
- Practice AU.L2-3.3.4: Provide audit reduction and report generation capabilities to support on-demand analysis and reporting. (Requires robust, analytical logging far beyond the basic logging required in Level 1).
4. Configuration Management (CM)
- Practice CM.L2-3.4.5: Implement the principle of least functionality by configuring information systems to provide only essential capabilities. (Requires hardening systems by disabling unnecessary ports, protocols, and services).
5. Identification and Authentication (IA)
- Practice IA.L2-3.5.3: Use multi-factor authentication (MFA) for local and network access to privileged accounts and for network access to non-privileged accounts (This is a mandatory, core CUI protection requirement).
6. Incident Response (IR)
- Practice IR.L2-3.6.1: Establish an operational incident-handling capability for organizational information systems that includes adequate preparation, detection, analysis, containment, recovery, and user response activities. (Requires a formal, documented Incident Response plan).
7. Maintenance (MA)
- Practice MA.L2-3.7.2: Ensure that CUI is not exposed to unauthorized individuals during system maintenance. (Specific focus on CUI protection during physical or remote maintenance).
8. Media Protection (MP)
- Practice MP.L2-3.8.7: Control access to media containing CUI and periodically limit the use of portable storage media (e.g., USB drives) on organizational systems. (Requires strict policy control over how CUI can be stored and moved).
9. Personnel Security (PS)
- Practice PS.L2-3.9.1: Screen individuals prior to authorizing access to organizational information systems containing CUI. (Requires formal background checks or other screening measures for personnel).
10. Physical Protection (PE)
- Practice PE.L2-3.10.4: Monitor visitors and escort them in areas where CUI is handled or systems containing CUI are located. (Requires control over access within the facility, not just at the perimeter).
11. Risk Assessment (RA)
- Practice RA.L2-3.11.2: Scan for vulnerabilities in the information system and applications periodically and when new vulnerabilities are identified. (Mandates proactive vulnerability scanning).
12. Security Assessment (SA)
- Practice SA.L2-3.12.3: Develop a Plan of Action and Milestones (POA&M) for the information system to document the organization’s planned corrective actions for deficiencies identified during the security assessment. (Requires formal documentation of deficiencies and remediation plans).
13. System and Communications Protection (SC)
- Practice SC.L2-3.13.11: Implement cryptographic mechanisms to protect the confidentiality of CUI during transmission outside the organizational system boundary. (Mandates encryption for CUI data-in-transit).
14. System and Information Integrity (SI)
- Practice SI.L2-3.14.7: Implement security alerts and response actions to address unauthorized changes to organizational software, firmware, and hardware. (Requires real-time monitoring for integrity violations).
CMMC 2.0 Level 3: Expert protection against Advanced Persistent Threats (APTs)
CMMC 2.0 Level 3, the "Expert" level, represents the pinnacle of cybersecurity maturity within the framework. It is reserved for the small subset of DIB organizations that handle CUI associated with the DoD’s most critical, high-priority programs and technologies, which are the primary targets of sophisticated adversaries, often referred to as Advanced Persistent Threats (APTs).
Key details for Level 3
- Scope: Applies to DIB companies that handle highly sensitive CUI on critical programs, requiring enhanced protection against APTs.
- Controls: Requires the implementation of 134 security controls in total. This includes:
- The 110 controls from NIST SP 800-171.
- An additional 24 enhanced controls derived from NIST SP 800-172, "Enhanced Security Requirements for Protecting Controlled Unclassified Information."
- Assessment type: Government-led Triennial Assessment conducted by the Defense Industrial Base Cybersecurity Assessment Center (DIBCAC). This is a crucial distinction, as organizations cannot use a C3PAO for Level 3 certification.
- Prerequisite: An organization must first achieve a Final Level 2 (C3PAO) status for the same scope.
- Certification validity: The DIBCAC assessment certification is valid for three years.
- Annual affirmation: Organizations must also submit annual compliance affirmations to SPRS for both Level 2 and Level 3 requirements.
- POA&M usage: The DoD has indicated that POA&Ms will be permitted for a limited number of non-high-value Level 3 requirements, provided they are closed out within a specified time frame (expected to be 180 days).
Enhanced CMMC Level 3 controls (The 24 NIST SP 800-172 practices)

The additional 24 practices focus on building penetration-resistant architectures, enabling damage-limiting operations, and designing for cyber resiliency. These controls build on the NIST SP 800-171 baseline by adding requirements for automation, advanced monitoring, and zero-trust concepts.
1. Access Control (AC)
- Practice AC.L3-3.1.2e: Restrict access to systems and system components to only those information resources that are owned, provisioned, or issued by the organization. (Eliminating the use of unauthorized or personal devices).
- Practice AC.L3-3.1.3e: Employ organization-defined secure information transfer solutions to control information flows between security domains on connected systems. (Focuses on secure data enclaves and controlled flow).
2. Awareness and Training (AT)
- Practice AT.L3-3.2.1e: Provide awareness training, including practical exercises, focused on recognizing and responding to threats from APT actors, social engineering, breaches, and suspicious behaviors. (Moves training from conceptual to practical exercise-based).
3. Configuration Management (CM)
- Practice CM.L3-3.4.1e: Establish an authoritative source and repository for approved system components and configurations. (Ensuring control over all trusted software/hardware baselines).
- Practice CM.L3-3.4.2e: Employ automated mechanisms to detect and handle unauthorized or misconfigured components; after detection, remove or quarantine them.
4. Identification and Authentication (IA)
- Practice IA.L3-3.5.1e: Authenticate systems and components using cryptographic, replay-resistant methods (e.g., strong mutual authentication).
- Practice IA.L3-3.5.2e: Employ automated mechanisms for password generation, rotation, and management.
5. Incident Response (IR)
- Practice IR.L3-3.6.1e: Establish and maintain a Security Operations Center (SOC) capability that operates 24/7, with allowance for remote/on-call staff. (Mandating continuous, high-level monitoring).
- Practice IR.L3-3.6.2e: Establish and maintain a cyber-incident response team that can be deployed by the organization within 24 hours.
6. Risk Assessment (RA)
- Practice RA.L3-3.11.1e: Conduct a threat-informed risk assessment at least annually to identify, analyze, and document potential risks and vulnerabilities. (The assessment must be informed by actual threat intelligence)
- Practice RA.L3-3.11.2e: Perform threat hunting activities to proactively search for malicious actors in the network that evade common detection methods.
7. Security Assessment (SA)
- Practice SA.L3-3.12.1e: Conduct penetration testing at least annually or when significant security changes are made to the system, leveraging automated scanning tools and ad hoc tests using subject matter experts. (Mandating offensive testing to find hidden vulnerabilities).
8. System and Information Integrity (SI)
- Practice SI.L3-3.14.1e: Verify the integrity of security-critical or essential software using cryptographic signatures or hardware/software roots of trust. (Ensuring foundational system components have not been tampered with).
- Practice SI.L3-3.14.2e: Use threat indicator information and effective mitigations obtained from, at a minimum, open or commercial sources and any DoD-provided sources, to guide and inform intrusion detection and threat hunting. (Mandates use of government-vetted threat intelligence).
What other framework controls overlap with CMMC controls?
1. NIST SP 800-171 (The Foundation)
This is not just an overlap; NIST SP 800-171 is the core technical basis of CMMC Level 2.
- Overlap: CMMC 2.0 Level 2 is a direct adoption of the 110 security controls specified in NIST SP 800-171 Rev. 2. The 14 control domains in CMMC Level 2 are identical to the 14 families in NIST SP 800-171.
- Relationship: NIST SP 800-171 provides the "what" (the requirements for protecting CUI), and CMMC provides the "how" (the verification and certification process via C3PAO audits or self-assessments).
- CMMC Level 3: This level builds on the Level 2 baseline by adding 24 enhanced controls from NIST SP 800-172.
2. NIST SP 800-53 (The Source)
NIST SP 800-53 is the comprehensive catalog of security controls for all U.S. Federal Information Systems (the highest standard). CMMC controls are essentially a refined subset of this extensive list.
- Overlap: NIST SP 800-171 (and thus CMMC Level 2) is a tailored set of controls derived directly from the larger catalog in NIST SP 800-53. These are the controls that were deemed necessary to protect CUI in non-federal (contractor) systems.
- Scope: An organization compliant with a high-level assurance of NIST SP 800-53 (like a Federal agency) has implemented a vast majority of the CMMC Level 2 and Level 3 controls, as the latter are lower-impact versions of the former.
3. FedRAMP (The Cloud Standard)
The Federal Risk and Authorization Management Program (FedRAMP) is the standardized security assessment and authorization process for cloud services used by federal agencies.
- Overlap: FedRAMP requires cloud service providers (CSPs) to meet security control baselines that are directly sourced from NIST SP 800-53. A FedRAMP Moderate authorization, for example, requires the implementation of 325 controls from NIST SP 800-53.
- Benefit: Since CMMC Level 2 uses only 110 controls derived from the same source (800-53), any FedRAMP-authorized cloud service or environment is generally considered to be highly compliant with the technical control requirements for CMMC Level 2.
4. ISO/IEC 27001 (International Standard)
ISO/IEC 27001 is a globally recognized standard for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS).
- Overlap: While ISO 27001 is risk-based (allowing an organization to choose controls based on risk), and CMMC is prescriptive (mandating specific controls), there is significant overlap in the control practices:
- Controls related to Access Control, Risk Assessment, Incident Response, and Configuration Management are common to both frameworks.
- Organizations with an existing ISO 27001 ISMS already have the foundational documentation, governance, and management structures required to implement and maintain CMMC compliance.
5. CIS Critical Security Controls (CIS Controls)
The Center for Internet Security (CIS) Controls are a prioritized, smaller set of best practices designed to protect organizations from the most pervasive and dangerous cyber-attacks.
- Overlap: Many foundational CMMC Level 1 and Level 2 practices map directly to the CIS Controls, especially Implementation Group 1 (IG1), which focuses on essential cyber hygiene. Examples include:
- Inventory of Assets (CM)
- Secure Configuration (CM)
- Access Control (AC)
- Vulnerability Management (RA/SI)
- Benefit: Implementing the CIS Controls provides a practical, high-value on-ramp to CMMC compliance, addressing critical gaps before tackling the full 110 NIST SP 800-171 controls.
Moving from checklist to certification: The Scrut advantage
You’ve successfully navigated the complex control environments of CMMC Levels 1, 2, and 3, and you understand the monumental challenge: CMMC is not a checklist; it's a GRC mandate requiring continuous security evidence. The stark reality is that the gap between technical implementation and audit-ready documentation is what costs DIB contractors billions in lost opportunities.
This is where Scrut transforms your compliance roadmap from a manual, months-long headache into an automated, continuous process. Scrut is purpose-built to eliminate the paperwork and audit uncertainty, ensuring you are always assessment ready.
1. Eliminate documentation pain points
The number one bottleneck for CMMC Level 2 is the documentation i.e., the SSP and all associated policies.
- SSP and POA&M automation: Scrut provides pre-built, auditor-vetted templates for your System Security Plan and all required security policies (e.g., Access Control, Incident Response). You start up to 70% job done, simply customizing the templates rather than writing hundreds of pages from scratch. Scrut then automatically tracks remediation progress, creating an audit-ready POA&M with required deadlines.
- Centralized evidence collection: Stop chasing screenshots and log files. Scrut integrates deeply with your existing tech stack, cloud providers (AWS, Azure), identity services (Okta), and code repositories, to auto-collect evidence 24/7. This proof is automatically mapped and time-stamped to the exact NIST SP 800-171 control, saving hundreds of hours of manual effort.
2. Master control overlap and scope
As you saw, CMMC heavily overlaps with other standards like ISO 27001 and NIST SP 800-53. Scrut leverages this overlap for efficiency.
- Unified control mapping: Scrut provides a unified control framework, allowing you to implement a single control (e.g., MFA) and have that implementation automatically satisfy the requirements across CMMC, ISO 27001, and other frameworks simultaneously.
- Clarify CUI scope: Our compliance experts help map your FCI and CUI data flows, ensuring you accurately define the Assessment Scope (enclave). This prevents over-scoping that drives up costs and under-scoping that leads to audit failure.
3. Achieve continuous compliance and assessment readiness
CMMC requires year-round vigilance, not just a one-time snapshot.
- Continuous Monitoring: Scrut continuously monitors all CMMC controls, providing real-time alerts when controls drift, evidence expires, or systems become misconfigured. You fix gaps immediately, minimizing compliance debt.
- Streamlined Audit Collaboration: When it’s time for your C3PAO or DIBCAC assessment, you grant the assessor secure portal access. They review a single source of truth for all required evidence, documentation, and compliance status, eliminating the tedious back-and-forth and accelerating the final certification.
Ready to Win Your Next DoD Contract?
Don't let compliance be the barrier to securing defense contracts. By automating your NIST SP 800-171 implementation and audit preparation, Scrut gives you the verified security posture the DoD demands.

FAQs
What is the goal of CMMC controls?
The goal is to protect Controlled Unclassified Information (CUI) and Federal Contract Information (FCI) across the Defense Industrial Base (DIB) supply chain from theft by sophisticated adversaries, ensuring national security.
Do all organizations need Level 2 controls?
No. Only DIB organizations that process, store, or transmit CUI must achieve Level 2. Organizations handling only FCI require the lower-tier Level 1 controls.
Can I use automated tools for CMMC compliance?
Yes. Automated tools are highly encouraged. They are essential for continuous monitoring, evidence collection, and demonstrating the institutionalization of controls required for the Level 2 assessment, significantly reducing manual effort and audit preparation time.
How does CMMC compare to NIST SP 800-171?
The main difference in the debate of CMMC vs. NIST SP 800-171 is verification.
NIST SP 800-171 defines the 110 security controls ("the what") required to protect CUI. CMMC is the certification program ("the how") that assesses and verifies the actual implementation and maturity of those 110 controls, making it a mandatory contract requirement.
Is CMMC required for subcontractors?
Yes. CMMC requirements flow down from the prime contractor to all subcontractors in the supply chain who handle the relevant information (CUI or FCI) for the contract. A subcontractor's required CMMC level is determined by the type of information they handle.
How long does CMMC certification take?
Preparation time varies widely based on the current security posture. For Level 2, preparation typically takes 6 to 18 months, followed by the actual C3PAO assessment, which can take several weeks to a few months to complete, depending on the complexity of the scope and the assessor's schedule.
Who can conduct a CMMC 2.0 Level 2 assessment?
The assessment can be conducted in two ways:
- CMMC Third-Party Assessment Organization (C3PAO) assessment: Required for prioritized, critical acquisitions.
- Annual self-assessment: Permitted for non-prioritized acquisitions.
What is the role of C3PAOs in the CMMC process?
C3PAOs are independent, DoD-authorized organizations accredited to conduct formal CMMC Level 2 assessments. Their role is to objectively verify that a contractor has fully implemented the NIST SP 800-171 controls before recommending them for certification.
What are NFO controls as they relate to CMMC?
NFO stands for Non-Federal Organization. NFO controls are practices within NIST SP 800-171 that are related to security but are considered outside the scope of the CMMC assessment (e.g., specific facility safety protocols). The DoD has clarified which controls are Assessed and which are NFO.
How do DFARS and CMMC Level 2 overlap?
DFARS (Defense Federal Acquisition Regulation Supplement) clause 252.204-7012 is the underlying contract clause that mandated the protection of CUI via NIST SP 800-171 controls and required self-attestation. CMMC Level 2 is the new, mandatory verification mechanism that validates compliance with the security requirements already specified in DFARS clauses.
What are the CMMC requirements?
The requirements are defined by the level: