CMMC audit demystified: Breaking down levels, costs, and requirements

The clock is ticking. For any defense contractor in the Defense Industrial Base (DIB), the Cybersecurity Maturity Model Certification (CMMC) 2.0 has moved beyond a theoretical future requirement; it is the new, non-negotiable gatekeeper for Department of Defense (DoD) contracts. With the Final Rule now published (on Sep 10, 2025 and takes effect on Nov 10,2025), the DoD is making good on its promise to unify and standardize cybersecurity practices across its entire supply chain to protect sensitive Federal Contract Information (FCI) and Controlled Unclassified Information (CUI). If your organization stores, processes, or transmits this data, achieving CMMC compliance is no longer optional; it is essential to maintain eligibility for lucrative government work.
This comprehensive guide is designed to cut through the complexity of the CMMC 2.0 program and its associated audit. We'll clarify exactly what a CMMC audit means in the context of the streamlined three-level model, walk you step-by-step through the entire certification process, break down the substantial costs involved, and, most importantly, show you the top reasons companies fail their assessment and how to avoid those critical pitfalls. Your journey to audit readiness starts here.
CMMC meaning: What exactly is the CMMC audit?
If the CMMC is the "what," the CMMC audit is the "how": the formal verification that your company has actually implemented the required cybersecurity controls. To understand the audit, we must first confirm the framework it assesses.
A. Core definition: The Unified Standard
The Cybersecurity Maturity Model Certification (CMMC) is a unified standard developed by the DoD to measure and ensure the cybersecurity posture of the entire DIB. It mandates that contractors implement specific sets of security practices and processes to protect sensitive DoD information. The audit is the mechanism, either a self-assessment or a third-party review (as per the rules), used to verify this implementation.
B. CMMC 2.0 refresher: Streamlining to three levels
CMMC 2.0 represents a significant update from its predecessor, simplifying a complex five-level structure into a streamlined, three-level model. This change was implemented to reduce costs for smaller businesses and increase alignment with established security standards.
The key features of CMMC 2.0 are:
- Tiered model: Compliance requirements are tailored to the sensitivity of information handled.
- Assessment types: Specifies whether compliance is verified via an annual self-assessment or a triennial third-party audit.
- NIST alignment: The requirements for the most critical levels are now directly mapped to the globally recognized NIST SP 800-171 standard, removing CMMC-specific practices and minimizing redundancy.
C. The data that drives compliance (FCI vs. CUI)
The type of government data your organization handles is the single most important factor determining which CMMC Level you must achieve.
- Federal Contract Information (FCI): This is non-public information provided by or generated for the Government under a contract (e.g., standard internal reports, project schedules, and general contract correspondence). It is essential data, but it is considered less sensitive. Handling only FCI drives the CMMC Level 1 requirement.
- Controlled Unclassified Information (CUI): This is highly sensitive information that requires specific safeguarding controls according to federal law, regulation, or government-wide policy. Examples include technical specifications, blueprints, legal data, or detailed financial records. CUI is significantly more sensitive than FCI and drives the rigorous requirements of CMMC Level 2 and Level 3.
Understanding this distinction is crucial because if you handle any CUI, you must comply with the much stricter requirements of Level 2, regardless of how much FCI you also possess.
The three CMMC levels explained
The required CMMC level is not a choice; it is dictated by the specific requirements and data sensitivity defined in the DoD contract you are pursuing.
A. Level 1: Foundational (Self-assessment)
- Focus: Protecting FCI.
- Practices: Requires 17 basic cybersecurity practices, which are directly aligned with FAR 52.204-21.
- Assessment: Compliance is verified via an annual self-assessment. The results must be formally documented and submitted to the DoD's Supplier Performance Risk System (SPRS).
B. Level 2: Advanced (The most common requirement)
- Focus: Protecting CUI. This applies to any organization handling sensitive technical, financial, or program data.
- Practices: Requires the implementation of 110 security practices, which are a direct and complete mapping to the controls defined in NIST SP 800-171.
- Assessment: Under the Final CMMC Rule, most Level 2 contractors handling CUI must undergo a triennial third-party assessment conducted by an accredited C3PAO. Only a limited subset of Level 2 contracts that involve less sensitive CUI may qualify for an annual self-assessment, as specified by the Department of Defense in each solicitation. Regardless of the assessment type, all Level 2 organizations must submit an annual affirmation of continued compliance to the SPRS.
C. Level 3: Expert (Highest risk)
- Focus: Protecting CUI from Advanced Persistent Threats (APTs). This level is reserved for providers supporting the DoD's most critical and high-priority programs.
- Practices: Requires all 110 NIST SP 800-171 controls plus a subset of advanced, enhanced controls drawn from NIST SP 800-172.
- Assessment: Level 3 assessments are performed by the Defense Contract Management Agency’s Defense Industrial Base Cybersecurity Assessment Center (DCMA DIBCAC). Organizations must first achieve a final Level 2 certification for the same scoped systems before requesting a Level 3 assessment. The DIBCAC evaluation is conducted every three years and focuses on a subset of enhanced controls drawn from NIST SP 800-172, verifying protection against advanced persistent threats.
The CMMC audit and certification process (step-by-step)
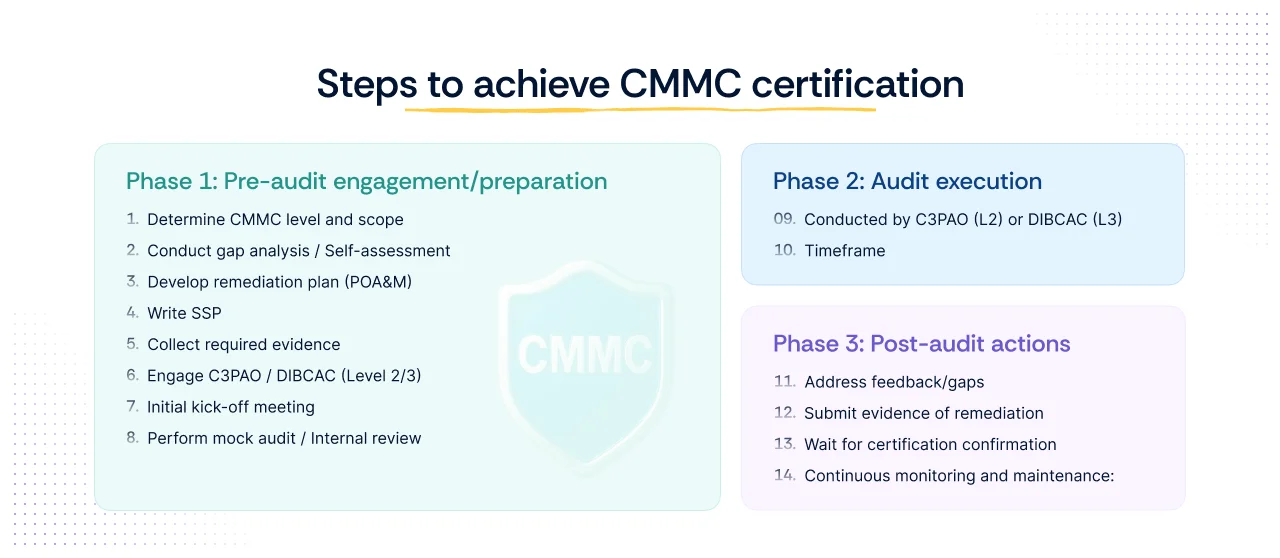
The CMMC audit is a rigorous, multi-phase program that demands preparation, execution, and sustained post-audit maintenance. Successfully navigating certification means understanding the distinct requirements of the three primary phases: Pre-audit engagement, audit execution, and post-audit actions.
Phase 1: Pre-audit engagement/preparation
Success hinges entirely on the quality of your preparation in this phase. The more thorough your initial work, the smoother and faster the official assessment will be.
- Determine CMMC level and scope: The first critical step is to identify your required CMMC Level (typically Level 2 for contractors handling CUI) and precisely define the scope of your CUI environment. This scope, often called the enclave, must isolate CUI to the smallest possible boundary.
- Conduct gap analysis / Self-assessment: You must internally assess your current security posture against the 110 practices of NIST SP 800-171 to identify any missing controls (gaps).
- Develop remediation plan (POA&M): For every gap identified, create a POA&M detailing how and when you will fix it. Crucially, high-priority and core controls (like strong MFA and logging) must be fixed pre-audit.
- Write SSP: This is the single most important document. The SSP formally describes your security environment and details how each CMMC control is implemented within your CUI enclave.
- Collect required evidence: Gather and organize all documentation necessary to prove compliance to the auditor, including policy documents, configuration screenshots, and system logs.
- Engage C3PAO / DIBCAC (Level 2/3): Select a C3PAO for Level 2 or engage the DoD's DIBCAC for Level 3 certification.
- Initial kick-off meeting: Hold a formal meeting with the auditor to align expectations, confirm the scope, and agree upon a timeline.
- Perform mock audit / Internal review: Conduct a final internal check to simulate the C3PAO review, ensuring all controls and documentation are perfect before the official assessment.
Phase 2: Audit execution
The official audit is conducted by the chosen assessor, who acts as the independent verification body.
- Conducted by C3PAO (L2) or DIBCAC (L3): The formal audit begins. The assessor reviews your SSP, conducts staff interviews, observes your system operations, and formally tests controls against the evidence you submitted.
- Timeframe: The duration of a CMMC assessment depends entirely on your organization’s readiness, the size and complexity of your CUI environment, and the assessor’s scheduling. In general, contractors should plan for a multi-month process from preparation to certification rather than relying on fixed timelines.
Phase 3: Post-audit actions
Certification requires both remediation and formal confirmation.
- Address feedback/gaps: If the assessor finds deficient controls that are remediable, you must address them promptly. Final POA&M items are submitted for review.
- Submit evidence of remediation: Provide the C3PAO with documented evidence proving that any post-audit gaps have been corrected.
- Wait for certification confirmation: C3PAO performs the assessment and status is posted into DoD systems (eMASS/SPRS). The Cyber AB (Cybersecurity Maturity Model Certification Accreditation Body) oversees the accreditation ecosystem and receives certificate copies from C3PAOs. Upon successful review and approval, your certification is confirmed and formally recorded.
- Continuous monitoring and maintenance: Certification is valid for three years (except for Level 1, which requires annual self assessment and affirmation), but compliance is not passive. You must implement continuous monitoring to maintain the security baseline and submit annual affirmations to the DoD.
CMMC cost reality: Why compliance costs far outweigh the audit fee
Many companies make the critical error of budgeting for CMMC by focusing only on the C3PAO audit fee. The reality is that the true financial burden of CMMC Level 2 is not the Auditing, it is the Compliance.
The cost of technical remediation, new security tools, policy documentation, and continuous monitoring will often be 5 to 10 times higher than the price tag for the formal assessment itself. This disparity is because the audit is a single event, while compliance is an ongoing, three-year operational investment. However, the total cost of audit and compliance will depend the size, maturity, and the complexity of the CUI enclave (scope).
Successful budgeting requires recognizing this difference and allocating funds across the four major phases of expenditure outlined below.
The successful CMMC budget treats compliance as a mandatory operational overhead, akin to insurance or rent, ensuring funding is secured for both the initial lift and the long-term sustainment.
Top reasons companies fail a CMMC audit (And how to avoid them)
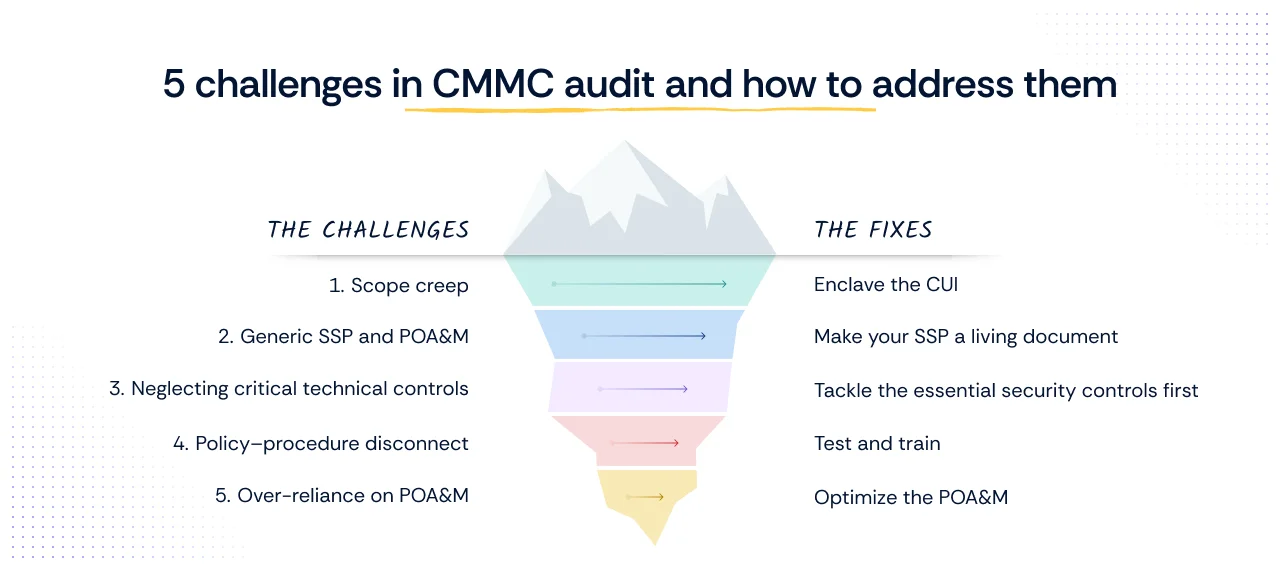
A CMMC Level 2 audit is an intensive review of 110 practices across 14 capability domains, directly aligned with NIST SP 800-171. Auditors (C3PAOs) look not only for implemented security controls but also for operational maturity, proof that your security processes are repeatable, documented, and consistently followed.
Failure is almost always tied to common, preventable mistakes in the preparation phase.
Challenge 1: Failure to define and restrict CUI scope (Scope creep)
This is arguably the number one reason companies fail. Organizations attempt to certify their entire corporate network, leading to hundreds of complex controls that must be audited. This is called "Scope Creep." If CUI touches every desktop, server, and SaaS application, the whole IT environment is in scope.
The fix: Enclave the CUI
Dedicate a small, isolated environment, a CUI enclave, to manage and store CUI. This might involve setting up a separate, compliant cloud service (like Microsoft 365 GCC High) that only a small, necessary subset of employees can access. By isolating CUI, you drastically reduce the number of systems and users that the C3PAO must assess, minimizing complexity and cost.
Challenge 2: Inadequate or generic documentation (SSP/POA&M)
The SSP is the auditor’s roadmap; it must accurately describe how you implement each of the 110 controls within your specific environment. Many companies use generic templates that fail to reflect their actual systems, hardware, and processes. A poorly written SSP is an immediate red flag and can halt the audit.
The fix: Make your SSP a living document.
Ensure the SSP is tailored to your unique CUI boundary and operational procedures. It should name the tools, staff, and locations involved for every single control. If your policy says "all mobile devices use approved encryption," your SSP must name the encryption standard, the devices, and the responsible department.
Challenge 3: Misunderstanding the severity of basic controls
Auditors will often fail a company immediately for non-compliance with fundamental technical controls, especially those related to identity and encryption. Common critical failures include:
- Missing or weak MFA: Failing to implement FIPS 140-2 validated MFA for all privileged access and remote access to the CUI environment.
- Non-compliant encryption: Using encryption methods that do not meet the FIPS 140-2 standard required for protecting CUI at rest and in transit.
- Lack of audit logging: Not having a functioning, centralized system (SIEM) that collects, reviews, and protects logs related to security events.
The fix: Tackle the essential security controls first.
Allocate budget and time immediately to deploy robust, compliant solutions for MFA, encryption, and centralized logging. These controls are foundational, and without them, the rest of your compliance efforts are moot.
Challenge 4: Policies exist, but procedures don't
An organization can have a perfect stack of written policies, but if the staff or technology isn't actually executing those policies, it's a failure of maturity. For example, the Incident Response Plan might look great on paper, but if staff aren't trained on it or can't locate the contact list, the control fails.
The fix: Test and train.
Conduct regular table-top exercises for key policies like incident response and media protection. Prove through internal audits, training records, and evidence (screenshots, logs) that your team knows how to implement the procedures described in your documentation. Security awareness training is an ongoing requirement, not a one-time class.
Challenge 5: Over-reliance on POA&M
The POA&M (Plan of Action and Milestones) is a structured remediation plan for controls that are not yet implemented but are required for certification. Under CMMC, conditional CMMC status with a POA&M is permitted for Level 2 and Level 3 for up to 180 days after the assessment. Many organizations treat it as a long-term deferral mechanism, failing the audit because they have too many or too complex controls listed in their plan.
The fix: Optimize the POA&M.
Treat the POA&M as an absolute last resort for minor, low-complexity controls. All high-severity controls (especially the core MFA/logging/encryption requirements) must be fully implemented before the C3PAO assessment begins. If you cannot prove compliance for a core control, you will not receive certification.
Essential tools and technologies for CMMC compliance

Achieving CMMC Level 2 is not just about documenting what you do; it's about proving how your technology enforces the required security controls. While the CMMC model is vendor-agnostic, certain categories of tools and specific environments are essential for efficiently managing the 110 NIST 800-171 practices.
Here are the non-negotiable technology categories your CUI enclave must utilize:
1. The CUI enclave platform
The most efficient way to achieve compliance is to consolidate CUI into a dedicated, pre-qualified cloud environment. This immediately tackles the scoping challenge (Step 1 of the roadmap).
- Actionable tip: Choose the Right Cloud. For most organizations using Microsoft products, many choose Microsoft 365 Government Community Cloud High (GCC High) because it simplifies meeting DFARS and FedRAMP Moderate requirements, but it is not the only compliant path. Any cloud environment that meets FedRAMP Moderate (or equivalent) standards, including approved AWS, Google Cloud, or ‘Moderate-Equivalent’ configurations, can host CUI securely
- Why it matters: These high-security clouds offer features that help meet stringent requirements, such as FIPS 140-2 validated encryption and data sovereignty controls, where commercial cloud tiers often fall short. Migrating CUI into a dedicated, segregated environment dramatically reduces the compliance burden on your non-essential corporate systems.
2. Identity and Access Management (IAM)
Access Control (AC) is a major domain in CMMC. You must know who has access to CUI and prove that their access is secure.
- FIPS 140-2 validated cryptographic standards: This is a non-negotiable requirement for all privileged access and remote access to the CUI environment. Look for IAM solutions (like Azure AD/Entra ID) that can enforce this specific, high-level encryption standard for multifactor authentication.
- Principle of least privilege: Your IAM solution must be configured to grant users only the minimum access necessary for their job roles. This means using Role-Based Access Control (RBAC) to manage permissions instead of granting blanket access.
3. Centralized logging and monitoring (SIEM)
CMMC requires you to collect, analyze, and protect audit logs across all in-scope systems. This is impossible without a centralized solution.
- Security Information and Event Management (SIEM): A SIEM solution (e.g., Microsoft Sentinel, Splunk, Graylog) is critical for controls related to Audit and Accountability (AU).
- Core function: The SIEM must aggregate logs from endpoints, servers, firewalls, and applications within the CUI enclave. It should be configured to automatically alert security personnel to suspicious activity and to store logs securely for a defined retention period, demonstrating compliance with forensic requirements.
4. Configuration and patch management
You must maintain strict control over system settings and ensure all software is up-to-date to protect against known vulnerabilities.
- Endpoint management tools: Tools like Microsoft Intune, SCCM, or other mobile device management (MDM) solutions are necessary to enforce Configuration Baselines (SC.L2-3.13.1) and manage system configurations across the enclave.
- Patching: Automated patch management is required. You must document and prove that patches are applied in a timely and consistent manner to all operating systems, firmware, and applications that touch CUI.
By investing in and properly configuring these four categories of technology, you create the bedrock necessary to generate the evidence and documentation (the SSP) that a C3PAO will require during the formal audit.
How Scrut simplifies CMMC compliance
Scrut transforms the overwhelming complexity of CMMC Level 2 into a manageable, continuous process. It directly addresses the cost and sustainment challenges by:
- Continuous monitoring: Automatically maps your existing security data to all 110 NIST SP 800-171 controls, providing real-time compliance scores and reducing manual effort.
- Documentation automation: Generates your SSP and required policies based on your environment, eliminating the need for expensive RPO consulting hours.
- Evidence collection: Streamlines the audit process by organizing and automatically collecting evidence for the C3PAO, accelerating your assessment and reducing auditor time.
- Gap remediation: Provides clear, prioritized tasks to close compliance gaps, ensuring you invest wisely in remediation rather than overspending.

FAQs
What are the levels of CMMC Audit?
The Cybersecurity Maturity Model Certification (CMMC) framework uses a tiered system with three defined levels, representing increasing cybersecurity maturity and control complexity:
- Level 1 (Foundational): Requires 17 practices focused on basic cyber hygiene. This level is for organizations that only handle Federal Contract Information (FCI).
- Level 2 (Advanced): Requires 110 practices, aligning with NIST SP 800-171. This is the primary level for contractors handling Controlled Unclassified Information (CUI).
- Level 3 (Expert): Requires a subset of practices from NIST SP 800-172, focused on protecting CUI from advanced persistent threats (APTs).
Do all CMMC maturity levels need separate audits?
Yes, they require separate assessment types.
- Level 1 requires an annual self-assessment, which the company performs internally and attests to the Department of Defense (DoD) via the Supplier Performance Risk System (SPRS).
- Level 2 (prioritized) requires an audit conducted by a Certified Third-Party Assessment Organization (C3PAO) for any contracts involving CUI, with the certification valid for three years.
While Level 2 (non-prioritized) can perform annual self-assessments instead.
- Level 3 will require a formal audit conducted directly by the DoD's DIBCAC.
Is CMMC Level 2 audit required for all suppliers?
No, CMMC Level 2 is only required for suppliers who will be processing, storing, or transmitting Controlled Unclassified Information (CUI) as part of their defense contract. Suppliers who only handle Federal Contract Information (FCI) are required to achieve CMMC Level 1 through self-assessment.
How does CMMC overlap with NIST 800-171 or DFARS?
CMMC is the DoD’s verification framework for existing requirements. CMMC Level 2 is built directly upon the foundation of NIST SP 800-171, requiring all 110 of those security practices. Similarly, CMMC formalizes the enforcement mechanism for the DFARS (Defense Federal Acquisition Regulation Supplement) clause 252.204-7012, which previously mandated self-attestation of NIST 800-171 compliance. Under CMMC, a third-party audit replaces the self-attestation for CUI-handling contracts.