Choose risk-first compliance that’s always on, built for you.
Go back to blogs
Creating a Proactive Risk-Based Vulnerability Management Strategy
Last updated on
April 21, 2025
8
min. read

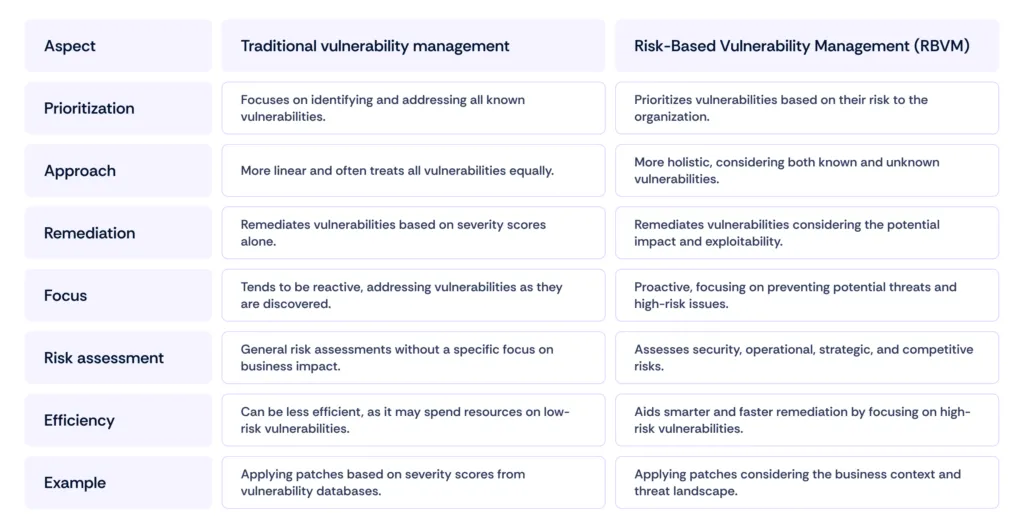
Traditional vulnerability management often treats all vulnerabilities equally, leading to inefficiencies and potential oversight of critical issues. Risk-based vulnerability management (RBVM) addresses several critical problems in cybersecurity by prioritizing vulnerabilities based on the actual risk they pose to an organization.
RBVM focuses on identifying, assessing, and mitigating vulnerabilities that are most likely to be exploited and cause significant damage. This approach helps organizations allocate their limited resources more effectively, reducing the overall risk exposure and enhancing the security posture.
By continuously monitoring and prioritizing vulnerabilities, RBVM ensures that the most pressing threats are addressed first, thereby preventing potential breaches and minimizing the impact of security incidents.
In this article, we will learn about how to create a proactive risk-based vulnerability management system.
Section 1: What is risk-based vulnerability management system?
To understand RBVM, the first question is, “What is a vulnerability management system?”
A VMS, vulnerability management system is a software application or platform designed to help organizations identify, assess, prioritize, and remediate security vulnerabilities in their networks, systems, and applications. This system involves continuous processes such as scanning for vulnerabilities, assessing their severity, prioritizing them based on the risk they pose, and applying appropriate remediation measures to mitigate or eliminate the risks.
By proactively managing vulnerabilities, organizations can reduce their exposure to cyberattacks and data breaches, ensuring better protection of their digital assets and maintaining compliance with security standards.
A risk-based vulnerability management (RBVM) system is a cybersecurity strategy that focuses on identifying, assessing, prioritizing, and remediating vulnerabilities based on the risk they pose to an organization. Unlike traditional vulnerability management approaches that treat all vulnerabilities equally, RBVM emphasizes the potential impact of vulnerabilities on the business.
This system continuously evaluates the organization’s IT environment to detect vulnerabilities and uses risk metrics to prioritize remediation efforts. By focusing on the most critical vulnerabilities that could be exploited and cause significant harm, RBVM helps organizations allocate their resources more effectively, reducing the overall risk and enhancing their security posture.
Why is a risk-based approach important in vulnerability management?
Seizing opportunities in risk-based vulnerability management ensures that the most critical vulnerabilities, which pose the highest risk to an organization, are prioritized and addressed first. This approach leverages machine learning and other advanced technologies to assess the potential impact of vulnerabilities by considering factors such as asset criticality, vulnerability severity, and threat actor activity.
By focusing on the vulnerabilities that are most likely to be exploited and could cause significant damage, organizations can allocate their resources more efficiently and effectively, thereby enhancing their overall security posture. This method not only helps in reducing the attack surface but also ensures continuous monitoring and proactive remediation of threats, ultimately minimizing the risk of cyberattacks and data breaches.
Difference between traditional and risk-based approaches
Key components of a risk-based vulnerability management system
A risk-based vulnerability management (RBVM) system incorporates several key components to effectively identify, assess, and mitigate vulnerabilities based on risk. Here are the primary components:
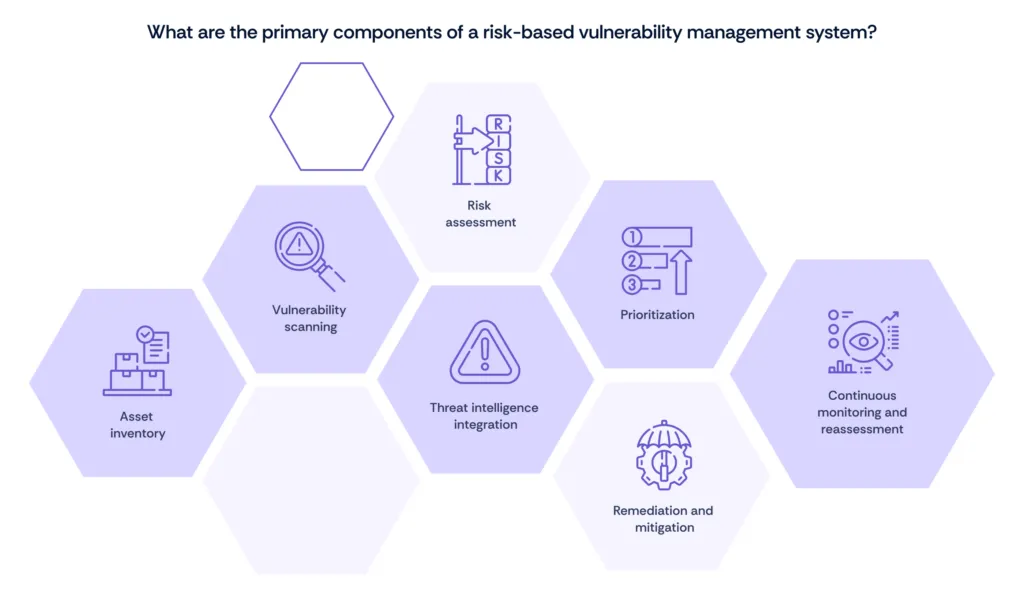
- Asset inventory: Comprehensive listing of all assets within the organization to understand their criticality and the impact of potential vulnerabilities.
- Vulnerability scanning: Regular scanning of systems and applications to identify known vulnerabilities.
- Risk assessment: Evaluating the potential impact of vulnerabilities by considering factors such as asset criticality, vulnerability severity, and threat actor activity.
- Threat intelligence integration: Incorporating threat intelligence to understand the motives, targets, and behaviors of potential attackers.
- Prioritization: Prioritizing vulnerabilities based on their risk level rather than just their severity. This ensures that the most critical vulnerabilities are addressed first.
- Remediation and mitigation: Implementing measures to fix or mitigate identified vulnerabilities, focusing on those that pose the highest risk to the organization.
- Continuous monitoring and reassessment: Ongoing monitoring of the risk environment and reassessment of vulnerabilities as new threats emerge and the organization’s IT environment evolves.
Section 2: Steps to conduct a risk-based vulnerability management system
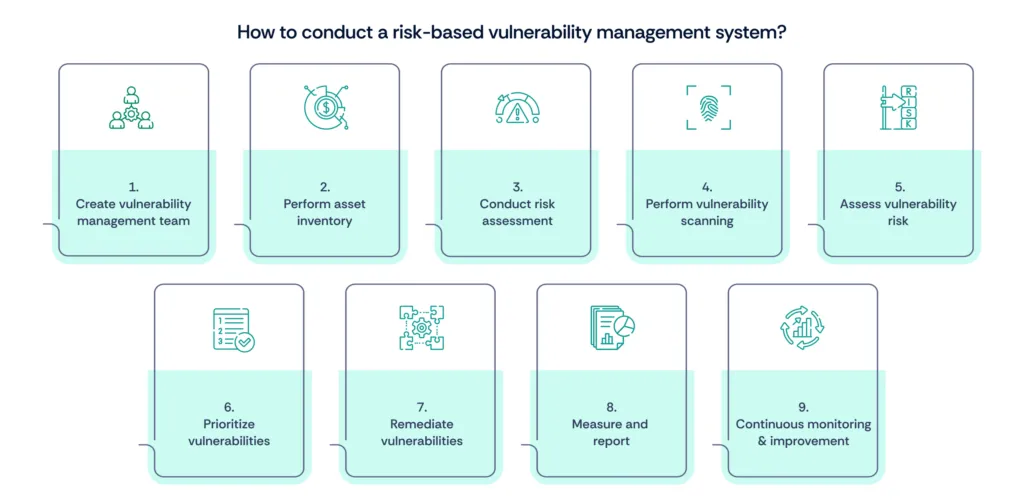
Step 1: Create a vulnerability management team
Assemble a dedicated team to oversee the vulnerability management process. This team should include IT security professionals, network administrators, system administrators, and relevant stakeholders from various departments. The team will be responsible for the entire vulnerability management lifecycle, ensuring that vulnerabilities are identified, assessed, prioritized, and remediated effectively.
Step 2: Perform asset inventory
Conduct a comprehensive inventory of all assets, including hardware, software, and cloud resources. This inventory should detail each asset’s type, location, and configuration. Accurate asset inventory is crucial for understanding the environment and ensuring that all potential vulnerabilities are identified.
Step 3: Conduct risk assessment
Evaluate the potential risks associated with each asset. This involves assessing the asset’s value, exposure, and the potential impact of vulnerabilities. Risk assessment helps in understanding which assets are most critical and what security measures are necessary to protect them.
Step 4: Perform vulnerability scanning
Use automated tools to scan assets for known vulnerabilities. These tools should be configured to scan the network, systems, and applications regularly. The scans will identify potential security weaknesses that need to be addressed.
Step 5: Assess vulnerability risk
Analyze the detected vulnerabilities to understand their potential impact and likelihood of exploitation. This assessment should consider the severity of the vulnerability, the ease of exploitation, and the potential damage if the vulnerability is exploited. This step helps in making informed decisions about which vulnerabilities to address first.
Step 6: Prioritize vulnerabilities
Rank vulnerabilities based on their assessed risk, focusing on those that pose the greatest threat to critical assets. Prioritization ensures that the most dangerous vulnerabilities are remediated first, reducing the risk of significant security breaches.
Step 7: Remediate vulnerabilities
Develop and implement plans to mitigate or remediate the highest-priority vulnerabilities. This may involve applying patches, changing configurations, or implementing additional security controls. The remediation efforts should be tracked and documented to ensure that vulnerabilities are effectively addressed.
Step 8: Measure and report
Continuously measure the effectiveness of remediation efforts and report on the status of vulnerabilities to stakeholders. Regular reporting helps in keeping all relevant parties informed about the security posture and the progress of vulnerability management activities.
Step 9: Continuous monitoring and improvement
Regularly update vulnerability scans, reassess risks, and refine the management process to address new threats and improve overall security posture. Continuous monitoring and improvement are essential to maintaining an effective vulnerability management program in the face of evolving threats.
Section 3: Benefits of risk-based vulnerability management system
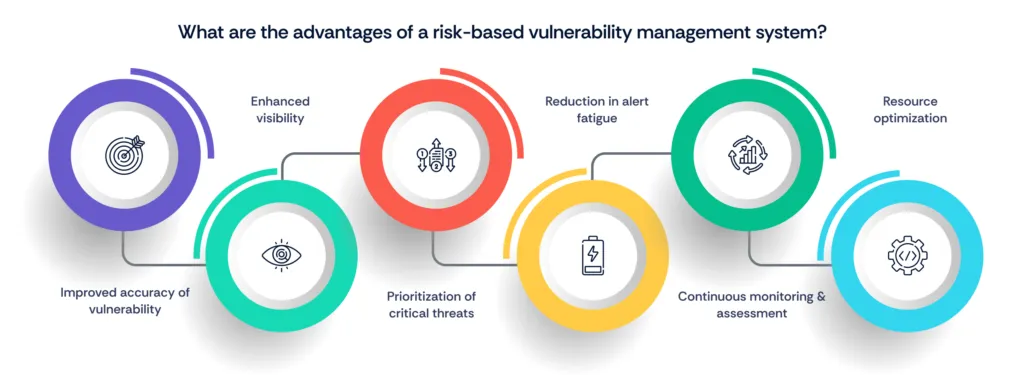
1. Improved accuracy
Risk-based vulnerability management (RBVM) leverages threat intelligence and threat-hunting capabilities to enhance the accuracy of vulnerability assessments. This ensures that the most critical threats are identified and addressed first.
2. Enhanced visibility
RBVM provides comprehensive visibility across all systems and infrastructure. This increased visibility helps organizations maintain a better understanding of their security posture and manage vulnerabilities more effectively.
3. Prioritization of critical threats
By correlating asset criticality, vulnerability severity, and threat actor activity, RBVM enables organizations to prioritize remediation efforts on the most significant threats, ensuring that resources are allocated efficiently.
4. Reduction in alert fatigue
A risk-based approach helps reduce alert fatigue by focusing on the vulnerabilities that pose the highest risk, thus minimizing the number of alerts and enabling security teams to concentrate on the most pressing issues.
5. Continuous monitoring and assessment
RBVM systems often incorporate automated and continuous monitoring of the attack surface, providing ongoing identification of security weaknesses and helping maintain an up-to-date understanding of the threat landscape.
6. Resource optimization
The ability to prioritize vulnerabilities based on risk allows for more efficient use of security resources, focusing efforts on the most critical vulnerabilities and ensuring that minor issues do not divert attention from significant threats.
Section 4: Challenges and solutions in implementing a risk-based vulnerability management system
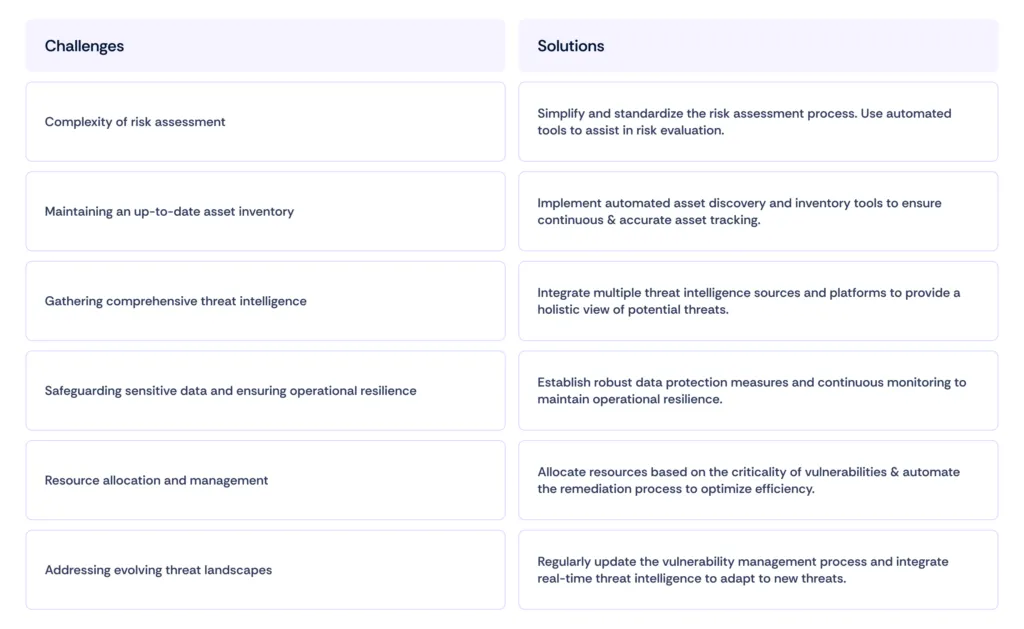
Winding up
In conclusion, adopting a risk-based vulnerability management (RBVM) approach revolutionizes how organizations handle cybersecurity threats. By prioritizing vulnerabilities based on actual risk, RBVM allows for more efficient resource allocation and enhances overall security. This strategy ensures that critical vulnerabilities are addressed first, minimizing the potential for significant breaches.
Implementing RBVM involves continuous monitoring, regular reassessment, and integrating threat intelligence, creating a more resilient IT environment. As cyber threats evolve, embracing RBVM is essential for safeguarding digital assets and maintaining operational resilience.
Enhance your organization’s security posture with Scrut’s comprehensive Risk Management solutions. Don’t wait for a breach to take action—start proactively managing your risks today. Request a Demo to experience Scrut’s advanced risk management platform.
FAQs
1. What is a Risk-Based Vulnerability Management (RBVM) system?
An RBVM system is a cybersecurity strategy that focuses on identifying, assessing, prioritizing, and remediating vulnerabilities based on the risk they pose to an organization. It emphasizes addressing the most critical vulnerabilities that could significantly impact the business.
2. How does RBVM differ from traditional vulnerability management?
Traditional vulnerability management treats all vulnerabilities equally and often focuses on severity scores alone. In contrast, RBVM prioritizes vulnerabilities based on their risk to the organization, considering factors like asset criticality, exploitability, and potential impact, leading to more efficient resource allocation and enhanced security posture.
3. Why is a risk-based approach important in vulnerability management?
A risk-based approach ensures that the most critical vulnerabilities are prioritized and addressed first, reducing the overall risk exposure. By focusing on vulnerabilities that are most likely to be exploited and cause significant damage, organizations can better allocate their resources and improve their security posture.
Table of contents


















