Choose risk-first compliance that’s always on, built for you.
Go back to blogs
ISO 27001 Compliance: Meaning, Controls, Cost, Audit, Policies
Last updated on
May 19, 2025
min. read
.png)
ISO 27001 is a well-known system for handling information security. Companies in different fields, such as IT, healthcare, finance, and manufacturing, use it around the world. This standard helps businesses build a strong Information Security Management System (ISMS). This system protects their intellectual property and customer data and ensures they follow relevant rules.
Organizations shell out between $10,000 and $90,000 to get certified, with the exact amount depending on how big and complex they are. This price tag covers things like audits, training, and advice they need as they go through the certification process. To get certified, they have to go through a two-part audit. First, the company’s policies are evaluated and then they carry out the assessment of ISMS. And it doesn’t stop there – to keep their certification, they need to have yearly check-ups called surveillance audits.
Essential policies, such as information security and incident management, help organizations manage security risks effectively. Originally published in 2005 and regularly updated, ISO 27001 enhances cybersecurity, builds customer trust, ensures legal compliance, and provides a competitive edge.
Hang on to read more about ISO 27001 and its requirements.
What is ISO 27001 Compliance?
ISO 27001 is an international standard for managing information security developed by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC). It offers a structure to set up, put into action, and enhance an ISMS. This makes it key for companies dealing with private information to show strong cybersecurity methods.
Getting certified means agreeing to regular checks—every three years—to ensure the ISMS meets standards. The benefits of certifying include better risk management, increased customer confidence, and adherence to legal requirements. Accredited certification bodies assist companies through the necessary documentation and compliance processes.
Part of the ISO 27000 family, the latest update to ISO 27001 in October 2022 introduced streamlined controls aimed at tackling modern cybersecurity challenges. Holding the ISO 27001 badge signals to customers and partners that your organization adheres to high standards of information security.
What are ISO 27001 Framework Controls?
Now, about the ISO 27001 controls—there are 93 security controls outlined in the most recent version (ISO/IEC 27001:2022), which replaces the previous ISO 27001:2013 standard. These controls address key aspects of information security such as data protection and privacy, enabling organizations to lower risks and safeguard sensitive information effectively.
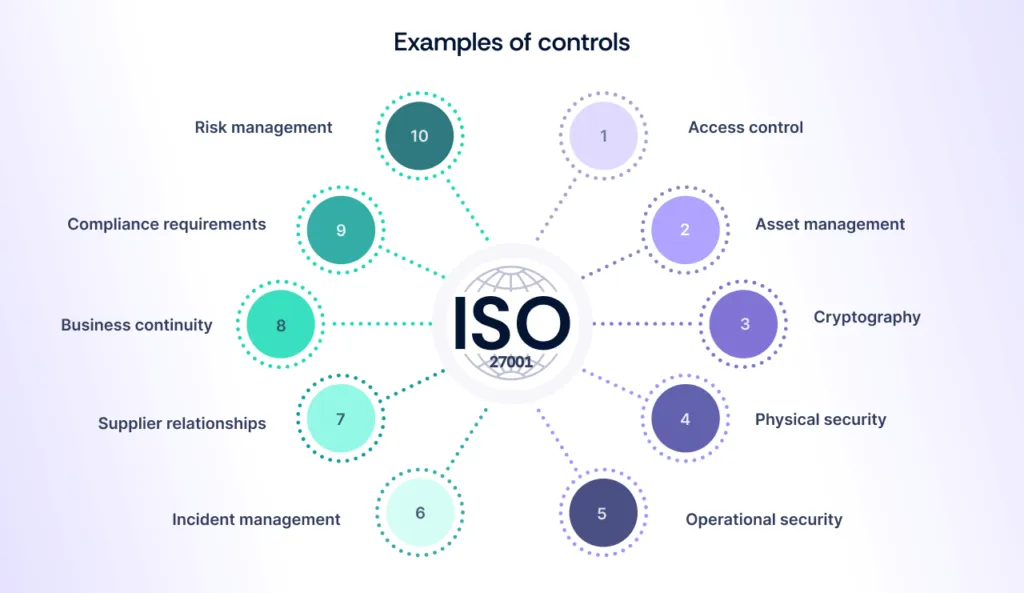
Do I need to follow the ISO 27001 controls list?
Yes, it’s essential to follow the ISO 27001 controls list if you seek certification or want to align with best practices. These controls are divided into key areas such as organizational measures, HR security, access control, and cryptography. Together, they play a crucial role in strengthening cybersecurity and effectively managing risks.
What are ISO 27001 requirements?
ISO 27001 requirements define the key elements for establishing an effective ISMS, including policies, risk assessments, and controls to manage risks and protect data. Checklists and templates simplify implementation and ensure compliance with international security standards.
ISO 27001 requirements
ISO 27001 is designed as a clear and comprehensive framework for managing information security. It includes sections like clauses and Annex A, helping organizations create a customized ISMS that aligns with their specific needs and risk profiles. This ensures sensitive information stays protected in today’s digital world.
ISO 27001 is structured into different sections, including clauses and Annex A, to provide a comprehensive framework for information security management. This structure allows organizations to build a robust and tailored information security management system that aligns with their specific needs and risk profile, ensuring the protection of sensitive information in today’s digital landscape. Here’s an overview of its structure:
Clauses 0–3: Setting the stage for ISMS
The initial clauses of ISO 27001 establish the groundwork for understanding and implementing an Information Security Management System (ISMS):
Clause 0: Introduction
Explains the purpose and benefits of an ISMS, setting the stage for how the standard can help organizations manage information security risks effectively.
Clause 1: Scope
Defines the boundaries of the ISMS, identifying which parts of the organization and information assets it covers.
Clause 2: Normative references
Lists related standards and documents that complement ISO 27001:2022.
Clause 3: Terms and definitions
Clarifies key terms used throughout the standard to ensure consistency and understanding.
Clauses 4–10: Implementing and maintaining ISMS
These clauses guide organizations on how to establish, operate, evaluate, and improve their ISMS:
Clause 4: Context of the organization
Focuses on understanding the organization’s internal and external issues relevant to information security.
Clause 5: Leadership
Highlights the role of leadership in driving the ISMS, including establishing a security policy and ensuring commitment at all levels.
Clause 6: Planning
Covers risk assessment, risk treatment, and setting clear objectives and plans for the ISMS.
Clause 7: Support
Emphasizes resource management, staff competence, awareness, and communication related to information security.
Clause 8: Operation
Details the practical implementation of ISMS processes, including operational control and risk treatment.
Clause 9: Performance evaluation
Discusses monitoring, measurement, and evaluation of the ISMS’s effectiveness.
Clause 10: Improvement
Encourages continuous improvement of the ISMS by addressing non-conformities and implementing corrective actions.
ISO 27001:2022 Controls: Annex A
Alongside its clauses, ISO 27001 includes Annex A, which provides detailed guidance on specific control objectives and information security controls. It contains a comprehensive set of 93 control objectives and controls that organizations can choose from to address their unique security needs.
The controls are grouped into 14 domains, including information security policies, asset management, access control, cryptography, and physical and environmental security. Organizations can select and adapt these controls based on their risk assessments and specific security needs, ensuring a tailored and effective ISMS.
What are ISO 27001 policies?
ISO 27001 policies are formal documents outlining rules, procedures, and responsibilities for maintaining an effective ISMS and ensuring compliance. The core information security policy sets the direction for protecting information assets.
The number of policies varies by organization size and needs, but key ones include access control, data protection, risk management, and incident response. These policies must be regularly reviewed, especially during audits or organizational changes, to ensure consistency and alignment with ISO 27001 requirements.
Should you do an ISO 27001 risk assessment?
Yes, conducting an ISO 27001 risk assessment is crucial for identifying, analyzing, and mitigating security threats to information assets. It helps prioritize resources and implement controls to address risks like unauthorized access, data breaches, physical vulnerabilities, third-party risks, and regulatory non-compliance. Regular assessments ensure proactive risk management and an effective ISMS.
Is it possible to do an ISO 27001 penetration test?
Yes, you can definitely conduct a penetration test as part of your ISO 27001 compliance efforts. While it’s not explicitly required by the standard, it’s highly recommended. Penetration testing helps identify vulnerabilities and evaluates how well your security controls are working.
Common vulnerabilities often include misconfigured systems, outdated software, weak access controls, unpatched security issues, and insecure APIs. Penetration testing helps uncover these weaknesses by simulating real-world attack scenarios, such as phishing attempts, SQL injections, or brute-force attacks.
This hands-on approach provides valuable insights into potential risks, complementing the ISO 27001 risk assessment process, and ensuring your ISMS is equipped to handle the ever-evolving landscape of cyber threats.
How to perform an ISO 27001 Compliance audit?
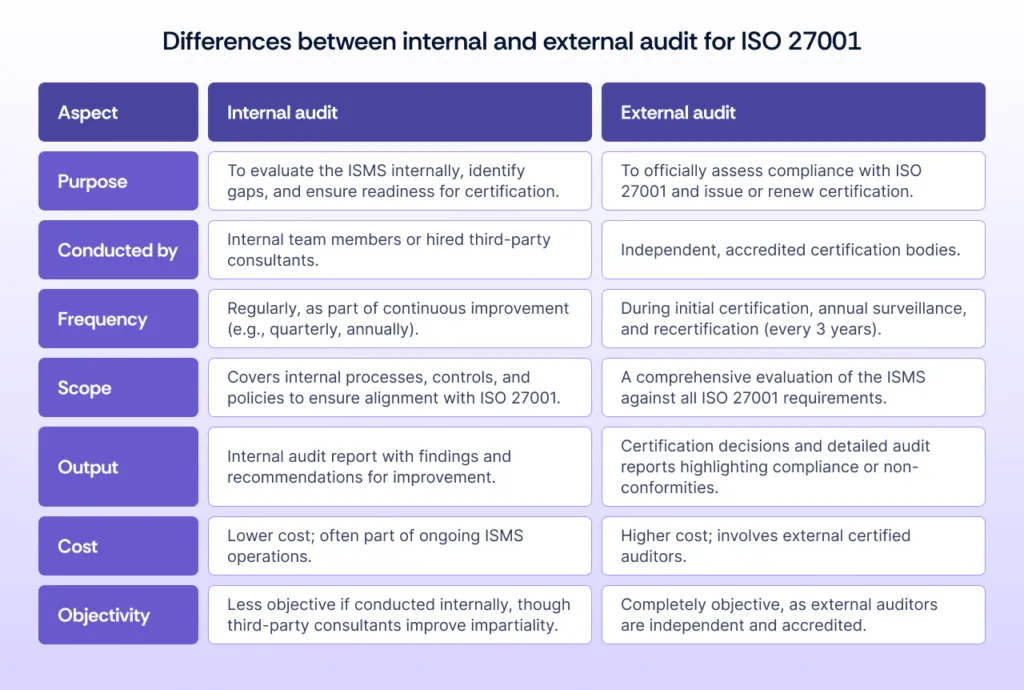
An ISO 27001 audit evaluates an organization’s compliance with the standard for an effective ISMS, ensuring key requirements like risk assessments, security controls, and documented policies are implemented. Audits can be internal (by trained professionals) and external (by certified auditors), with external audit costs ranging from $10,000 to $50,000, depending on size and complexity. More of both types of audits in the next section.
Audits occur during initial certification, annual surveillance, or when significant ISMS changes occur. Regular audits identify gaps, ensure compliance, and maintain certification, demonstrating a commitment to data protection and enhancing stakeholder trust.
What are the different types of ISO 27001 audits?
An ISO 27001 internal audit is an internal evaluation of an organization’s ISMS to ensure compliance with ISO 27001 requirements. Conducted by internal team members or third-party consultants, it identifies gaps, non-conformities, and areas for improvement. The internal audit is part of the ongoing ISMS maintenance process and helps organizations prepare for external certification audits.
On the other hand, an ISO 27001 external audit is an independent, formal assessment conducted by accredited certification bodies to verify an organization’s compliance with ISO 27001 standards. It is performed during the initial certification process, annual surveillance, and recertification audits. The external audit assesses whether the ISMS meets the standard’s requirements. If successful, it leads to ISO 27001 certification or its renewal.
The external audit consists of:
- Stage 1 audit (Documentation review): A preliminary check of ISMS policies and documentation.
- Stage 2 audit (Certification audit): A thorough evaluation of the ISMS’s implementation and effectiveness.
External auditors also carry out surveillance audits annually after certification to ensure continued compliance and improvement of the ISMS. These audits confirm the organization is maintaining ISO 27001 standards.
The key differences between ISO 27001 internal audit and external audit lie in their purpose, execution, and auditors involved:
How to complete the ISO 27001 certification process?
Successfully completing the certification process allows you to earn the ISO badge, showcasing your compliance with globally recognized security standards.
Steps to complete ISO 27001 certification
- Establish an ISMS: Develop and implement an ISMS aligned with ISO 27001 requirements.
- Perform a gap analysis: Identify areas of non-compliance and address them effectively.
- Conduct a risk assessment: Evaluate potential risks and apply appropriate controls.
- Document policies and procedures: Create required ISO 27001 documents and records.
- Internal audit: Perform an internal audit to ensure the ISMS is functioning effectively.
- External audit: Engage an accredited certification body for Stage 1 and Stage 2 audits.
- Obtain ISO badge: Once certified, display the ISO 27001 badge to showcase your compliance.
Completing these steps ensures your organization meets ISO standards and maintains a strong security posture.
To renew an ISO 27001 certificate, an organization must complete a recertification audit with an accredited certification body, demonstrating ongoing compliance with the standard; this renewal is required every three years to maintain certification.
Also Read: Achieving ISO 27001 certification: Tips and guidance
What is the ISO 27001 certification cost?
The cost of obtaining ISO 27001 certification varies based on factors such as organizational size, complexity, and existing security measures. According to Scrut Automation, the total cost typically ranges from $15,000 to $90,000.
The breakdown includes:
- Audit preparation costs: $3,000 to $40,000, covering gap analysis, penetration testing, and standard requirements.
- Implementation costs: Starting from $1,000 annually, encompassing security training, new tools, and managing productivity loss.
- Certification audit costs: $10,000 to $50,000, which includes internal audits, certification, and surveillance.
These figures are estimates, and actual costs can vary based on specific organizational needs and the chosen certification body. Investing in ISO 27001 certification enhances information security management and builds customer trust.
How can Scrut help with ISO 27001 Compliance certification?
Scrut Automation offers comprehensive tools and expertise to simplify and accelerate the ISO 27001 certification process. Here’s how Scrut can help:
1. Streamlined compliance management
Scrut offers a comprehensive platform that streamlines ISO 27001 compliance activities, such as managing policies, controls, and evidence collection. By automating repetitive tasks, it minimizes manual effort and ensures that no critical steps are missed.
2. Audit readiness
Scrut enables organizations to monitor their compliance progress in real time and stay audit-ready. The platform organizes and securely stores ISO 27001 documentation, simplifying the process of presenting evidence during audits. It also offers checklists to ensure all requirements, from defining the ISMS scope to conducting risk assessments, are covered.
3. Expert guidance
Scrut connects organizations with a network of ISO 27001 consultants and auditors who provide personalized guidance. These experts assist in designing and implementing an ISMS that aligns with ISO 27001 standards, helping to address any compliance gaps along the way.
4. Policy and control templates
Scrut offers pre-built templates for key ISO 27001 policies and controls, like the Information Security Policy and Access Control Policy. These templates save time, ensure compliance with standard requirements, and make implementation quicker and more precise.
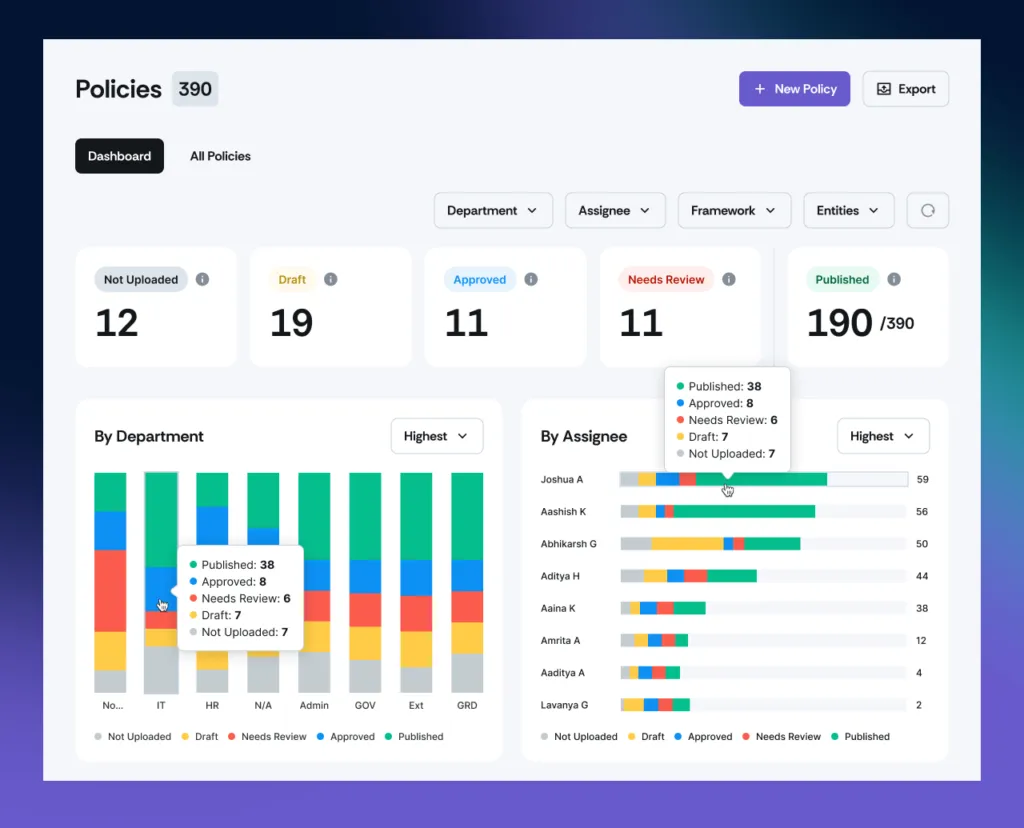
5. Continuous monitoring
The platform continuously monitors your ISMS to proactively identify and address risks. This helps ensure that your controls remain effective, minimizing the risk of non-compliance during annual surveillance audits or the three-year recertification process.
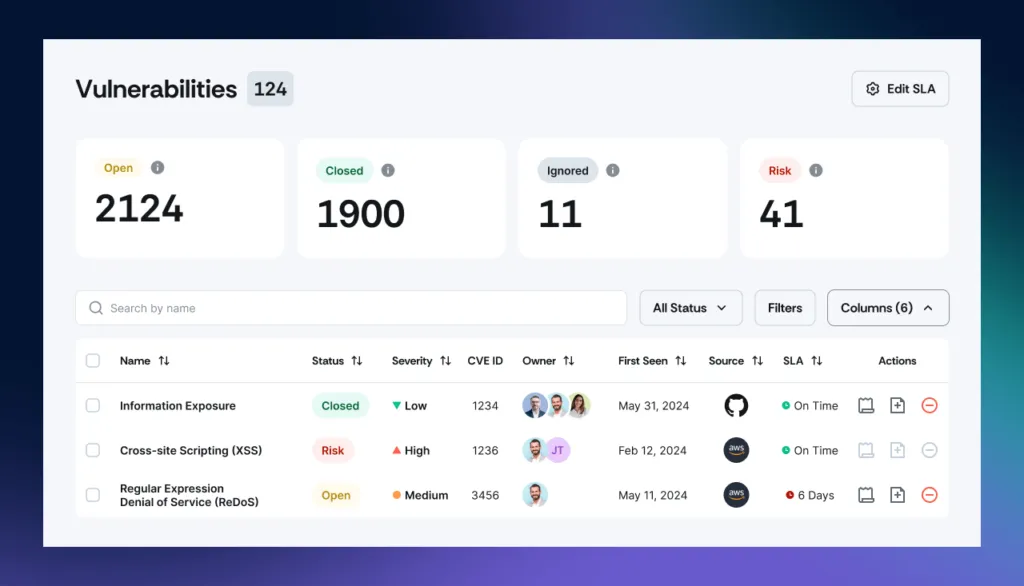
6. Integration with existing tools
Scrut integrates with your organization’s existing tools and systems, like cloud providers and ticketing platforms, enabling smooth evidence collection and control verification. This makes the certification process simpler and more efficient.
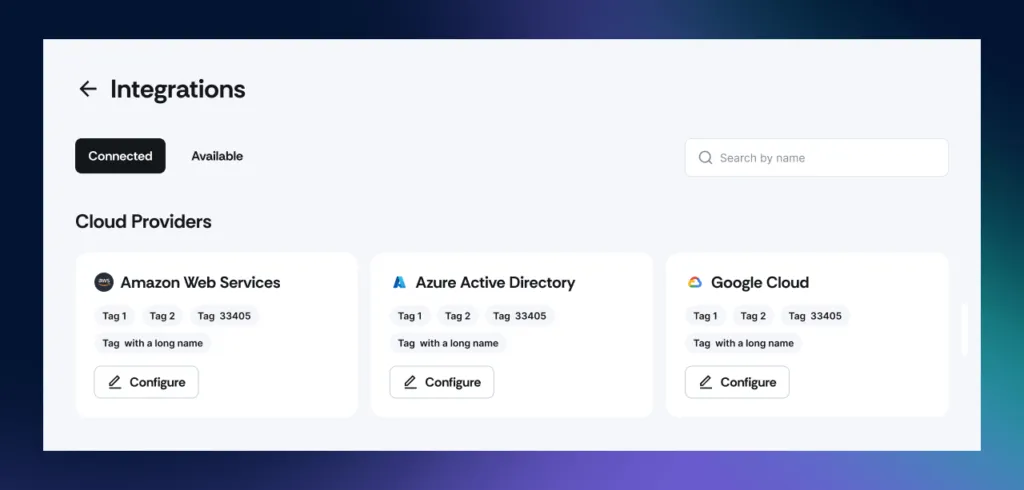
7. Cost efficiency
Scrut simplifies ISO 27001 certification by automating compliance activities and centralizing control over the entire process. This reduces the time and resources needed, making it a cost-effective solution—particularly for small and medium-sized enterprises pursuing certification.
8. Recertification support
Scrut goes beyond initial certification by helping organizations prepare for periodic audits and the recertification process, ensuring continuous compliance with ISO 27001 standards.
By combining automation, expert guidance, and real-time tracking, Scrut empowers organizations to achieve and maintain ISO 27001 certification efficiently, eliminating much of the complexity typically associated with compliance.

Ready to achieve ISO 27001 certification?
Streamline your ISO 27001 certification journey with Scrut. From compliance management to audit readiness, our platform and expert guidance make achieving and maintaining ISO 27001 effortless.
Get started today and ensure your organization meets the highest security standards.
FAQs
Is ISO 27001 the same as other ISOs
No, ISO 27001 is not the same as other ISO standards. While all ISO standards provide best practice frameworks, ISO 27001 specifically focuses on managing information security through an ISMS. In contrast, ISO 31000 addresses risk management, and ISO 42001 focuses on AI management systems. Each serves a unique purpose but can complement one another when implemented together.
Is ISO the same as IEC?
No, ISO and IEC are not the same but work closely together. ISO develops global standards across industries, while IEC focuses on electrical and electronic technologies. Joint standards like ISO/IEC 27001 combine their expertise for comprehensive global frameworks.
Who can be ISO 27001 certified?
Any organization, regardless of size, industry, or location, can achieve ISO 27001 certification by implementing and maintaining a compliant ISMS. This applies to businesses, non-profits, and government entities handling sensitive information. Certification is granted after a successful audit by an accredited body.
What are the benefits of being ISO 27001 certified
Achieving ISO 27001 certification offers organizations numerous advantages, strengthening their information security posture while boosting credibility and operational efficiency.
1. Enhanced information security: Protect sensitive data effectively.
2. Regulatory compliance: Meet legal and industry requirements.
3. Improved customer trust: Showcase commitment to security.
4. Competitive advantage: Stand out in the market.
5. Risk management: Identify and mitigate potential threats.
6. Operational efficiency: Streamline security processes.
7. Global recognition: Align with an internationally recognized standard.
8. Continuous improvement: Foster a culture of ongoing security enhancements.
Is there any particular training for ISO 27001?
Yes, specific ISO 27001 training programs help individuals and organizations understand and implement its requirements. These include ISMS implementation, internal auditing, and lead auditing courses offered by accredited providers, ensuring effective compliance management and certification maintenance.
Can I map ISO 27001 to other frameworks?
Yes, you can map ISO 27001 to other frameworks, as it shares common principles with many global standards. Common mapping frameworks include the NIST Cybersecurity Framework, ISO 31000 for risk management, SOC 2 for service organization controls, and GDPR for data protection compliance. This allows organizations to efficiently align their security practices across multiple regulatory and industry requirements.
Internal Linking: Link to the most popular ISO Mapping to another framework
How many updates have there been in the ISO 27001 standard?
The ISO 27001 standard has undergone two major updates since its initial release. It was first published in 2005, updated in 2013, and most recently revised in 2022. Updates are not frequent, typically occurring every 7–10 years, ensuring the standard remains relevant to evolving security challenges while maintaining stability for long-term implementation.
Table of contents


















