As businesses grow and scale, cloud data management, and storage solutions become more appealing. The challenge, of course, is ensuring the safety and security of your data, and that’s where cloud security monitoring comes in.
Cloud security monitoring tools continuously assess and analyze data and infrastructures for threats and vulnerabilities on both virtual and physical servers.
The overall goal of cloud security monitoring solutions is to ensure that organizations store and retrieve data securely when using cloud services.
To do this, they scan your cloud infrastructure and identify misconfigurations in your public cloud environment.
Next, these cloud security tools help you act on security issues in your cloud before they are exploited by hackers.
Cloud security monitoring solutions include the following capabilities:
- Most cloud security software apps integrate with popular cloud service providers such as AWS, GCP, and Azure to provide visibility into your cloud environment.
- A cloud monitoring solution monitors all activities happening in your cloud infrastructure. It continuously looks for risky activities and helps mitigate the threat in real time.
- A cloud monitoring platform provides a unified view of your organization’s users, files, and applications.
A cloud monitoring tool helps you stay compliant with the different privacy and security frameworks.

This article will present some of the top 12 cloud security monitoring tools available in the market many organisations turn to google cloud consulting services to design secure architectures.
List of 12 Cloud Security Monitoring Tools
1. Scrut Automation
Scrut Cloud Security continuously scans and monitors misconfigurations in your public cloud accounts against Center for Internet Security (CIS) benchmarks.
Scrut tests your cloud configurations against 200+ cloud controls across CIS benchmarks to maintain a strong InfoSec posture.
Furthermore, Scrut Cloud Security enables you to fix cloud misconfigurations preemptively. The platform ensures that your public cloud accounts are always compliant and secure.
Scrut gives you alerts with actionable recommendations for remediation as misconfigurations occur.

You can assign tasks to team members for misconfiguration fixes.
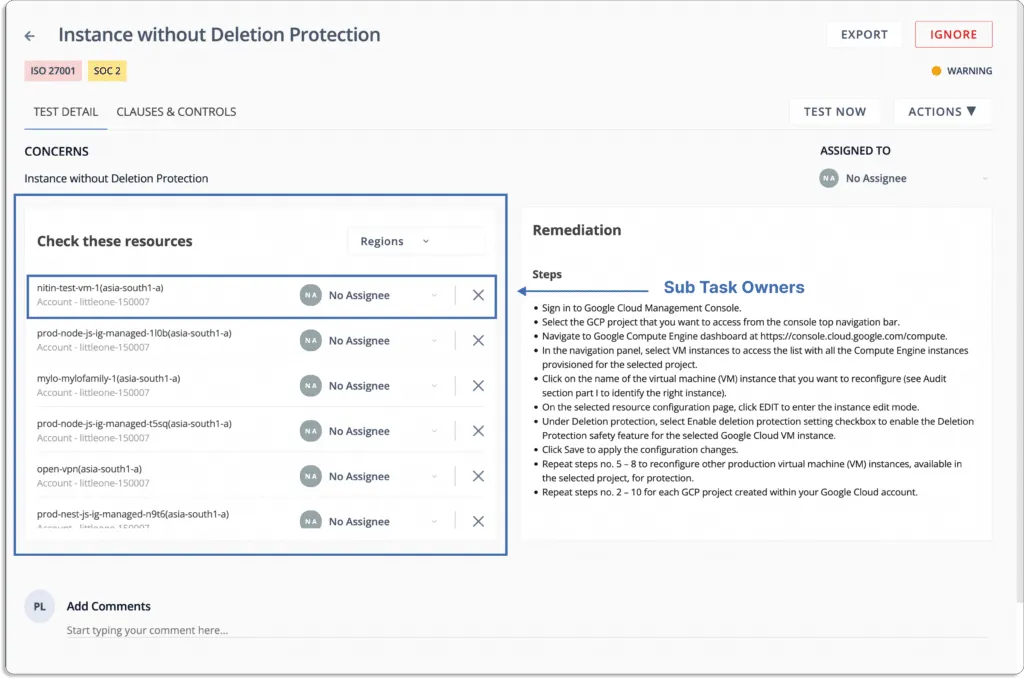
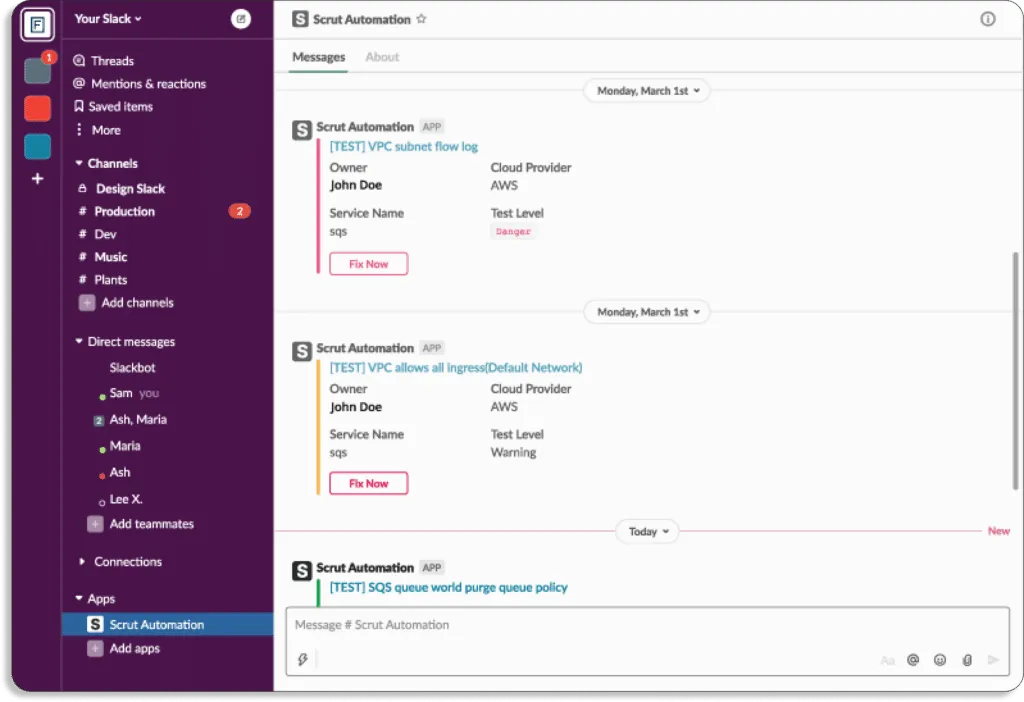
You don’t need to check the platform periodically for new alerts; you get the notifications directly on your existing tools, like Slack.
When issues are diagnosed you can create Jira tickets directly from the platform.

Scrut provides you with a single pane of glass for all the risks. These risks come with a status that helps you prioritize what to work on first.

Status
- Danger – Most critical issues. Work on these first.
- Warning – After working on the issues marked as danger, next, you can work on these.
- Low – These risks should be worked on last.
- Compliant – Everything is fine. Don’t need to do anything.
In short, Scrut Cloud Security strengthens your cloud-native security. It establishes complete security for all your cloud-native deployments across containers, serverless, and virtual machines (VMs).
Scrut enables you to implement security best practices consistently across your hybrid and multi-cloud infrastructure.

Now, let’s see how Typesense improved their cloud security posture with Scrut Cloud Security.
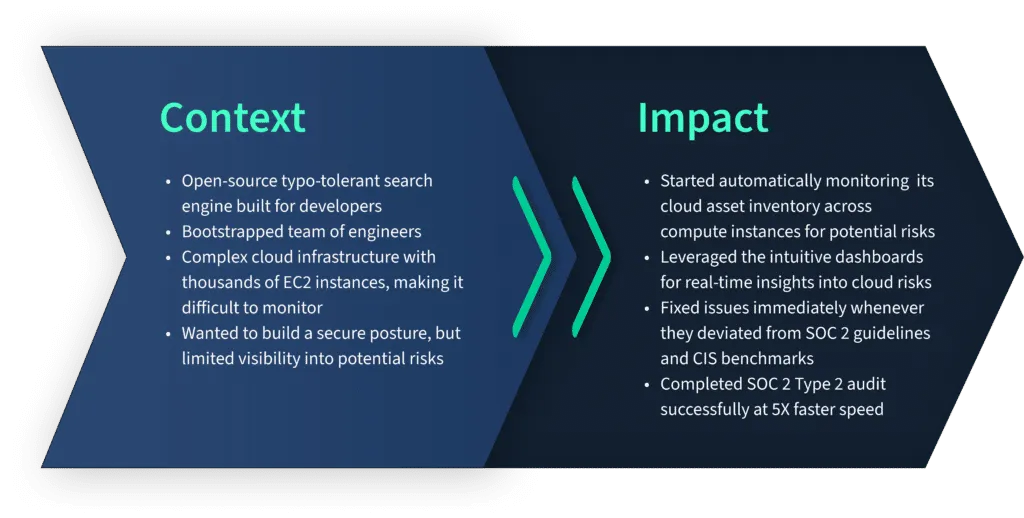
Typesense (now our customer) reached out to us with the goal of getting SOC 2 Type 2 compliant. Before going for the audit, they required a secure cloud posture but needed more visibility into their cloud risks.
Due to thousands of EC2 instances, they found it difficult to monitor their AWS infrastructure. With an agentless deployment, Scrut Cloud Security relieved them of the headache of monitoring their cloud environment.
As a result, they successfully completed their SOC 2 audit at 5x speed.
Here is what Jason Bosco, founder, and CEO of Typesense, has to say about Scrut.

Getting started with Scrut is easy and quick.
It is a 2 step process.

First, you need to connect your cloud infrastructure with the Scrut platform. This takes a few minutes only.
Just go to Integrations under the Settings tab.
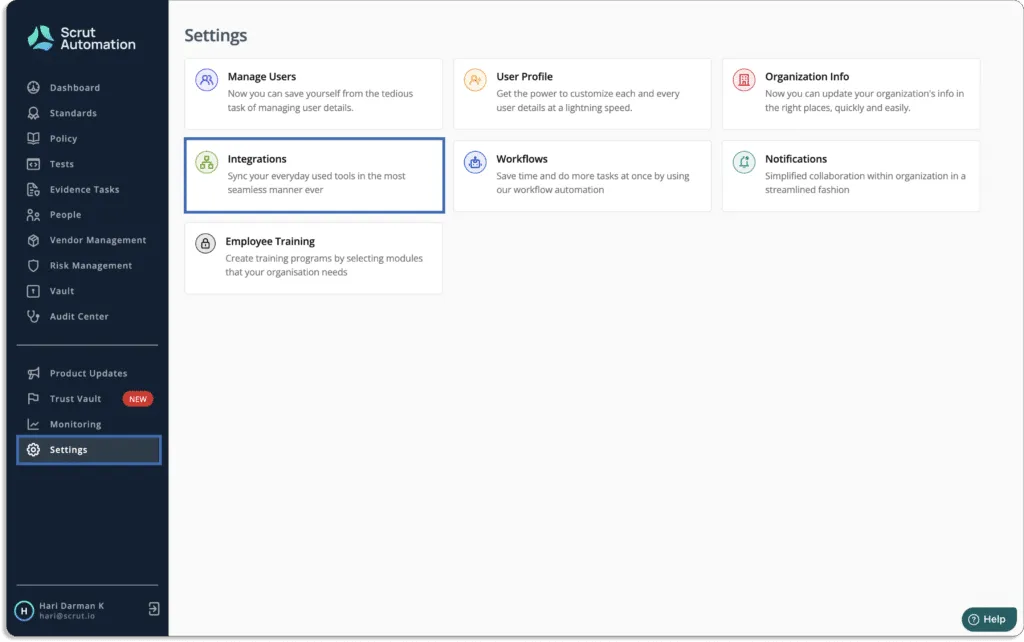
You will land on this page. Choose your cloud service providers.
Note that Scrut supports multi-cloud service providers.
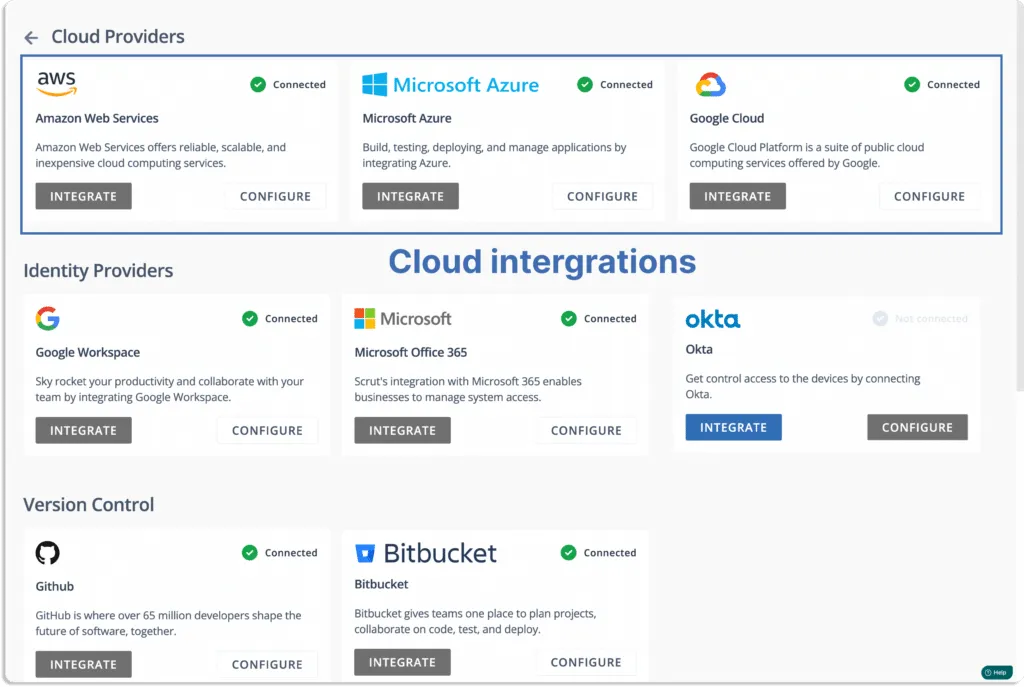
Next, click on configure for all your cloud service providers.
For AWS, you integrate either via role-based login or via access key. Scrut allows you to connect multiple AWS accounts, unlike some other CSPM tools.
Once connected, you can see the data appearing in the tests tab.

Check our customer’s reviews of G2 below:
Customer Rating
- G2- 5/5

2. DisruptOps
DisruptOps is a cloud security operations platform that monitors, alerts, and responds to security risks in your public cloud infrastructure in real-time. It delivers critical issues directly to the right responders within the tools you already use, such as Slack, Teams, and Jira. The platform claims to bring down barriers between development, security, and operations teams, allowing anyone to be an active defender.
Pros
- Quick to set up and simple to use.
- Enables security and development teams to fix cloud security issues faster by directly taking actions on the Slack, Jira, and Teams platforms.
Cons
- Primarily built for AWS cloud; if you are using Azure, GCP, or any other cloud service providers, many cloud monitoring features are missing.
Customer Rating
- Capterra- 5/5
3. JupiterOne
JupiterOne makes identifying, mapping, analyzing, and securing your cyber assets and attack surface simple. Users can gain complete visibility into complex cloud environments to detect threats, close compliance gaps, and prioritize risk.
The platform unifies and standardizes asset data across complex multi-cloud environments. Users can use a single query to search for information from multiple cloud providers, applications, and services.
Pros
- Fully automated infrastructure auditing.
- Provides continuous instrumentation and monitoring of cloud environments and controls.
Cons
- Due to the steep learning curve, some may find it a little confusing at first.
- Relationship mapping between different assets can give inaccurate results.
Customer Rating
- G2- 5/5
4. Wiz
Wiz platform provides complete visibility and context for your cloud in minutes, allowing your teams to proactively identify, prioritize, remediate, and prevent risks to your business. Wiz scans every layer of your cloud environment without agents to provide complete visibility into every technology running in your cloud with no blind spots.
Pros
- Setup takes just a few minutes since it works on 100% API-based integrations.
- The platform gives the security team the context to prioritize suitable risks and reduce false positives.
Cons
- Reports are not customizable; thus, you cannot exclude any particular data from the default report. This can be a problem when you want the top executives to focus on serious issues.
- License calculation is complex. It covers various clouds and object types.
Customer Rating
- G2- 4.9/5
5. Threat Stack
Threat Stack security platform protects your application infrastructure across all layers of the infrastructure stack and provides the observability required for proactive and targeted remediation action. The platform offers built-in configurable security, compliance risk detection, and alerting rules.
Pros
- Best fit for small-size companies who are serious about cloud security.
- Collects all events and color codes them according to the severity level. This makes it easy to understand for most teams.
Cons
- The tool doesn’t allow you to trigger a scan on demand. Thus, you must wait for the next day to check the status for confirmation after fixing any vulnerability.
- There is no option in the tool to store all events for one year for compliance purposes.
Customer Rating
- G2- 4.4/5
6. Lacework
Lacework reduces the complexity of cloud security posture and compliance. It continuously tracks your cloud environment and provides comprehensive visibility to reduce risks and compliance requirements in your organization.
It is a unified platform that provides comprehensive visibility and control over your multi-cloud environment, removing silos and blind spots.
Pros
- Delivers alerts directly to Slack or PagerDuty, so you don’t need to check periodically on the platform.
- One-stop for many security needs, such as container image scanning, cloud trail, compliance reports, etc.
Cons
- Creating custom alerts can be tricky as it is not a graphical user interface based.
- Setting up branch protection rules for a GitHub repository may be challenging.
Customer Rating
- G2- 4.5/5
7. Fugue
The Fugue platform provides security teams with the tools to build, deploy, and maintain cloud security throughout the development lifecycle. It is one platform to meet all of your cloud infrastructure security requirements.
Fugue gives cloud engineering and security teams the ability to demonstrate continuous compliance, incorporate security into cloud development, and eliminate cloud misconfiguration.
Pros
- Provides regulatory health checks in the AWS platform, assessing cloud compliance and matching it to customer standards and organizational policies.
- Fugue allows users to see all their cloud resources and compliance issues.
Cons
- It may be a little confusing at first.
- When using Fugue CLI, it is not possible to use SAML-based authentication.
Customer Rating
- G2- 4.8/5
8. Aquasec
The Aqua Platform is a cloud-native application protection platform (CNAPP). It provides prevention, detection, and response automation across the entire application lifecycle to secure the supply chain, cloud infrastructure, and running workloads wherever deployed.
The platform safeguards applications from development to production on VMs, containers, and serverless workloads up and down the stack.
Pros
- Monitors and remediates vulnerabilities in docker images.
- The Aqua platform provides real-time visibility and event trail audit logs, which protect data in a containerized environment.
Cons
- The platform lacks a few prominent alert notification channels, such as Datadog and Webhooks.
Customer Rating
- G2- 4.5/5
9. Axonius
Axonius cloud asset compliance connects to your cloud platforms to map the state of your cloud instances against industry standards and benchmarks.
Users can strengthen their cloud security posture with Axonius. It leverages data from connected cloud IaaS provider accounts. The tool automatically identifies misconfigurations and policy lapses that pose a risk.
Pros
- The software allows users to aggregate CSV reports and make API calls to various data sources.
- Data can be aggregated for endpoints, servers, and people. You could combine data from Active Directory, Vulnerability Scanner, and Antivirus into a single report.
Cons
- Lack of if – else – then query capabilities.
- There is currently no way to organize the metric cards by another sorting option (the default sorting is based on the creation date.)
Customer Rating
- Capterra – 5/5
10. CloudGuard
Check Point CloudGuard provides unified cloud-native security across your applications, workloads, and network, allowing you to automate security, prevent threats, and manage posture at cloud scale and speed.
The platform provides advanced security intelligence, which includes cloud intrusion detection, network traffic visualization, and cloud security monitoring and analytics.
Pros
- Easy to deploy and scale as per requirements to secure your cloud environments.
- The platform works well in local branches and integrates well with the cloud. It is adaptable enough to deploy everything from large centralized data centers to IoT/OT devices to local branches.
Cons
- It is one of the most expensive solutions available in the market.
- CloudGuard console is hard to monitor traffic and threats.
Customer Rating
- G2 – 4.4/5
11. Blumira
Blumira Cloud Security protects your cloud environments, including AWS and Azure, by quickly detecting and responding to cloud security threats.
The platform uses threat intelligence and behavioral analytics to detect attacker attempts to log in to your systems, such as geo-impossible logins and fraudulent login attempts that may indicate username and password theft.
Pros
- Easy setup with super simple administer.
- Simple to deploy with a high detection rate and easy to integrate with various platforms.
- The platform can be configured to send alerts to phones directly when abnormal activities are detected.
Cons
- It can give the same false-positive alert multiple times.
- As an MSP, users cannot add new clients through the portal; instead, they must fill out a form.
Customer Rating
- G2- 4.8/5
12. Sumo Logic
Sumo Logic Cloud Security Platform offers cloud-native data monitoring and analysis, resulting in actionable security awareness for your cloud and on-premise environments. The platform simplifies prioritizing and investigating security insights within your infrastructure.
With the Sumo Logic cloud security solution, users can stay ahead of changing attack surfaces by generating deep security insights through use-case-driven queries, dashboards, and alerts.
Pros
- Provides real time security insights into the server.
- Data sharing can be private or public, allowing developers to create searches and share them with support staff.
Cons
- Reports cannot be downloaded for sharing in Sumo Logic cloud SIEM enterprise.
- Searching through logs is a little slow.
Customer Rating
- G2- 4.3/5





































