Understanding CMMC: Levels, requirements, and certification process

The Cybersecurity Maturity Model Certification (CMMC) is the U.S. Department of Defense’s unified strategy to strengthen the cybersecurity of the defense supply chain. As threats continue to evolve, CMMC establishes a verified framework for protecting sensitive government information, including Federal Contract Information (FCI) and Controlled Unclassified Information (CUI).
For contractors and subcontractors handling these types of data, CMMC certification will become a mandatory requirement for many DoD contracts. The model builds directly on established cybersecurity standards like NIST SP 800-171, organizing them into a tiered system to help organizations demonstrate their cybersecurity maturity.
Whether you are a small subcontractor or a prime contractor, understanding CMMC is essential. In this blog, we will explain what CMMC is, who needs it, its levels, the compliance process, costs, benefits, and how it compares to other standards like FedRAMP.
What is the Cybersecurity Maturity Model Certification (CMMC)?
The Cybersecurity Maturity Model Certification (CMMC) is a Department of Defense (DoD) program that makes sure defense contractors and subcontractors are following the right cybersecurity practices to protect government information. It is specifically designed to safeguard Federal Contract Information (FCI) and Controlled Unclassified Information (CUI).
CMMC provides a clear framework with defined levels, helping organizations demonstrate that they can handle sensitive data responsibly and meet DoD requirements.
Who must comply with CMMC?

If your organization wants to bid on or hold DoD contracts, you will likely need to check whether you need a CMMC certification. The required level is specified in each contract, so meeting that level is essential to be eligible for the award. This applies to contractors of all sizes across the Defense Industrial Base.
(Note: CMMC is being rolled out in phases. While the CMMC 2.0 rule was finalized, it is being incorporated into contracts throughout 2025 and 2026. In the interim, many DoD contracts will continue to rely on self-attestation to NIST SP 800-171 via the SPRS system rather than a formal CMMC certification. However, preparing for mandatory certification now is essential for future contract eligibility.)
Industry examples include:
- Defense manufacturers: Companies producing weapons, aircraft, or other defense systems must comply to protect CUI such as design specifications and production processes.
- IT service providers: Firms offering IT support, cloud services, or software development for DoD agencies need to meet CMMC standards to safeguard FCI and CUI in their systems.
- Consultants and engineering firms: Organizations providing consulting or engineering services on DoD projects must implement CMMC practices to protect sensitive project data and communications.
For a detailed breakdown of which organizations must comply, check out our guide on who must comply with CMMC.
What are the CMMC levels?
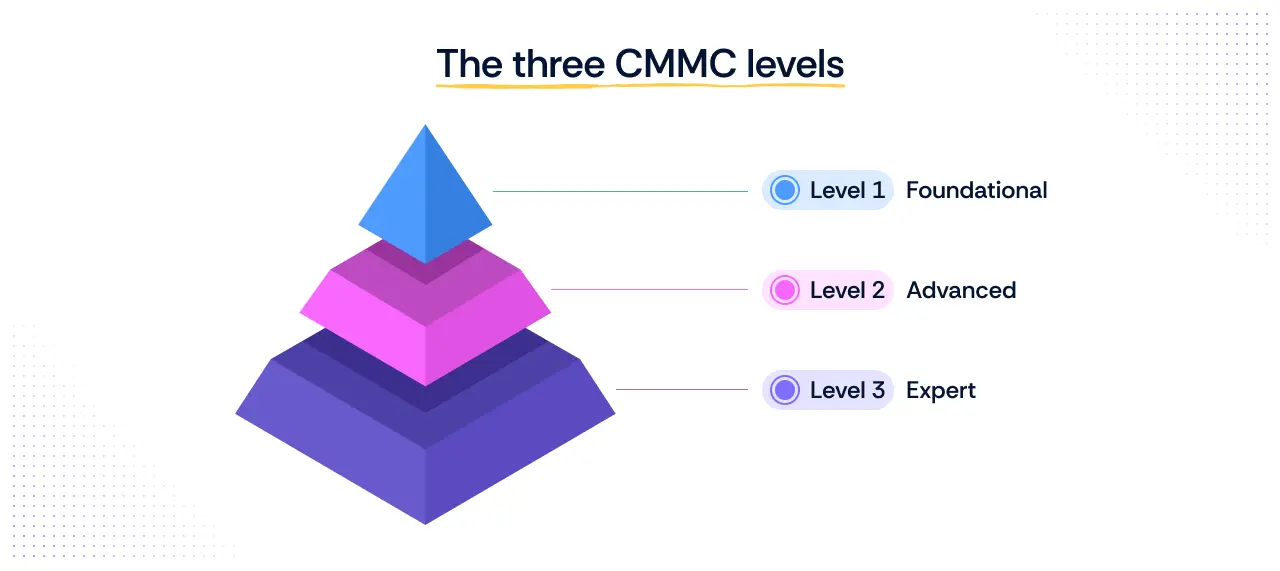
CMMC is structured as a tiered framework, with three main levels that reflect increasing cybersecurity requirements. Each level builds on the previous one, helping organizations gradually strengthen their practices while protecting sensitive DoD information. The level your organization needs depends on the type of information you handle and the contracts you pursue.
Level 1 – Foundational
This level focuses on protecting Federal Contract Information (FCI). It requires 17 basic cybersecurity practices derived from the FAR 52.204-21 standard. Assessment at this level is typically a self-assessment, making it suitable for organizations that handle less sensitive information.
Level 2 – Advanced
Level 2 is designed to safeguard Controlled Unclassified Information (CUI). Organizations must implement all 110 practices from NIST SP 800-171. Depending on the sensitivity of the contract, assessment can be either self-assessment or performed by a third-party assessor. This level serves as a bridge for organizations moving from foundational protections toward more robust cybersecurity controls.
Level 3 – Expert
The highest tier, Level 3, adds around 24 enhanced practices from NIST SP 800-172 on top of the 110 NIST SP 800-171 practices. It is aimed at protecting critical programs from advanced threats, and assessments are government-led.
What is the process for CMMC compliance?
CMMC 2.0 builds directly on existing DoD cybersecurity requirements under DFARS and NIST SP 800-171. While the process may appear complex, viewing it as an extension of your current obligations makes it much more manageable. Whether you’re a small subcontractor or a large prime contractor, following these steps will help you prepare for certification once full enforcement begins.
Step 1 – Review your contracts and DFARS clauses
Start by reviewing your DoD contracts and solicitations to determine what type of data you handle and which DFARS clauses apply.
- DFARS 252.204-7012 requires compliance with NIST SP 800-171 for protecting Controlled Unclassified Information (CUI).
- DFARS 252.204-7021 introduces the CMMC program and specifies the level of certification required for a contract once enforcement begins.
If your organization handles only Federal Contract Information (FCI), you’ll likely need Level 1 certification. If you process or store CUI, Level 2 or Level 3 will apply. Understanding your data classification is the foundation of your compliance path.
Step 2 – Identify your CMMC level
CMMC 2.0 includes three progressive levels, each with distinct requirements:
1. Level 1 (Foundational): For contractors handling only FCI. Requires an annual self-assessment and affirmation submitted to the Supplier Performance Risk System (SPRS).
2. Level 2 (Advanced): For organizations handling CUI. Aligns with the 110 controls in NIST SP 800-171.
- Non-prioritized contracts require an annual self-assessment.
- Prioritized contracts require a Certified Third-Party Assessor Organization (C3PAO) assessment every three years.
3. Level 3 (Expert): For contractors handling the most sensitive CUI. Incorporates additional NIST SP 800-172 controls and requires a DoD-led assessment every three years.
Step 3 – Evaluate and report your NIST SP 800-171 implementation
Before beginning your CMMC journey, ensure your SPRS score is accurate and up to date.
- Conduct a self-assessment using the DoD Assessment Methodology to measure how fully you’ve implemented the 110 NIST SP 800-171 controls.
- Maintain a System Security Plan (SSP) describing your current security posture and a Plan of Action and Milestones (POA&M) outlining remediation steps for any gaps.
- Submit your self-assessment score to SPRS, and update it at least every three years or whenever significant security changes occur.
Step 4 – Define the scope of your environment
Map out all systems, assets, and networks that process FCI or CUI. Accurate scoping helps you focus compliance efforts on the relevant areas, minimizing unnecessary work and cost.
Step 5 – Conduct a readiness assessment
Most organizations benefit from working with a Registered Provider Organization (RPO) to identify gaps before a formal assessment. RPOs are authorized by The Cyber AB (formerly the CMMC Accreditation Body) and specialize in helping contractors prepare documentation, strengthen controls, and align with their target level.
Step 6 – Undergo the required assessment
Plan your formal evaluation based on your determined level:
Level 1: Annual self-assessment and affirmation.
Level 2: Either self-assessment or C3PAO-led review (depending on prioritization).
Level 3: DoD-led assessment for high-priority programs.
Assessments typically include document review, staff interviews, and verification of implemented controls.
Step 7 – Remediate and certify
If deficiencies are found, update your POA&M and address them within the allowed time frame. Once compliance is verified, certification is issued through the Cyber AB’s accreditation ecosystem.
Step 8 – Maintain and improve your cybersecurity maturity
CMMC certification remains valid for three years, with annual affirmations. However, compliance is not a one-time event. Continuous monitoring, incident reporting, and periodic updates to your SSP ensure ongoing alignment with DoD requirements. CMMC’s ultimate goal is to foster a culture of continuous cybersecurity improvement, not just checklist compliance.
What are the benefits of being CMMC compliant?
Achieving CMMC compliance is more than a contractual requirement; it strengthens your organization’s cybersecurity posture and builds trust with the Department of Defense and other stakeholders. Beyond meeting DoD standards, compliance brings practical advantages that improve operations and reduce risk.
Key benefits include:
- Enhanced data protection: Compliance ensures that Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) are secured, reducing the risk of data breaches or unauthorized access.
- Supply chain trustworthiness: Verified compliance signals to the DoD and other partners that your organization can be trusted to handle sensitive information, strengthening your role within the defense supply chain.
- Eligibility for DoD contracts: Meeting the required CMMC level is essential for bidding on and winning contracts, opening up business opportunities in the defense sector.
- Reduced audit stress: Proper documentation, policies, and evidence collection streamline assessments and make audits less stressful for your team.
- Competitive advantage: Demonstrating verified cybersecurity maturity sets your organization apart, showing clients and partners that you take data security seriously.
- Standardized cybersecurity posture: CMMC provides a clear, unified framework for the entire Defense Industrial Base. This eliminates confusion and replaces a patchwork of different client requirements with a single, well-defined standard.
- Improved overall security hygiene: The practices required by CMMC (especially at Level 2) are fundamental cybersecurity best practices that protect against a wide array of common attacks. This means your entire business, not just the government data, becomes more resilient against cyber threats, reducing the risk of downtime, data loss, and reputational damage.
How much does CMMC compliance cost?
The cost of achieving CMMC compliance can vary based on several factors, including the organization's size, the level of certification required, and the complexity of its information systems.
While the DoD does not provide specific cost figures, it does acknowledge that organizations will incur costs to implement existing contract requirements for safeguarding information.
Here are some rough estimates:
Level 1 (Foundational): Typically ranges from $5,000 to $15,000, focusing on basic cybersecurity practices for protecting Federal Contract Information (FCI).
Level 2 (Advanced): Ranges from $50,000 to over $200,000, depending on the organization's size and complexity. This level requires compliance with 110 practices from NIST SP 800-171.
Level 3 (Expert): Ranges from $100,000 to $500,000, especially for larger organizations with complex systems. Level 3 compliance includes all Level 2 requirements plus additional practices from NIST SP 800-172.
These estimates are general and can vary based on factors such as the organization’s existing cybersecurity posture, the scope of the assessment, and the resources available for implementation. It's advisable for organizations to conduct a thorough assessment to determine the specific costs associated with achieving the desired CMMC level.
What happens after CMMC compliance?
After your organization achieves CMMC certification, maintaining ongoing compliance is essential. For Level 1, this means completing an annual self-assessment and affirmation. Level 2 and Level 3 certifications are generally valid for three years, with annual affirmations recommended to ensure continued adherence.
During this period, it is important to keep your cybersecurity practices up to date, especially if you continue to handle FCI or CUI. Continuous monitoring, policy updates, and addressing any gaps will help you stay prepared for future assessments.
CMMC requirements may evolve as the Department of Defense updates guidance or introduces new standards, and organizations are expected to adapt accordingly. When the certification period ends, renewal or reassessment is required.
Renewal is usually less costly than the initial certification, as much of the required documentation and controls are already in place. By planning ahead and maintaining strong cybersecurity practices, your organization can ensure the certification remains valid while reducing the effort needed for future assessments.
How does CMMC differ from NIST SP 800-171 or FedRAMP?
CMMC, NIST SP 800-171, and FedRAMP all focus on cybersecurity, but they serve different purposes. CMMC is a DoD certification required for contractors handling FCI and CUI. NIST SP 800-171 is a set of practices for protecting CUI but does not provide certification.
FedRAMP focuses on cloud security for federal systems, and some contractors that provide cloud services must also comply with its requirements.
All three share a common goal: protecting sensitive information through structured, risk-based controls. Organizations compliant with NIST or FedRAMP may find it easier to meet some CMMC requirements, but additional steps are needed for certification.
How Scrut helps with CMMC compliance
Scrut simplifies CMMC preparation by centralizing policies, controls, evidence, and audit management in one platform. It offers 150+ pre-built, version-controlled policies and 1400+ controls pre-mapped across 60+ frameworks, helping organizations reduce duplication and streamline efforts. Up to 70% of manual compliance tasks can be automated, and audit-ready evidence can be collected via 100+ integrations.
With unified risk and compliance workflows and end-to-end support from compliance experts, Scrut helps organizations prepare efficiently, stay organized, and confidently meet CMMC requirements.

FAQs
Does every DoD contractor need CMMC certification?
Not every contractor needs certification. It depends on whether your organization handles Federal Contract Information (FCI) or Controlled Unclassified Information (CUI) and the specific requirements of your DoD contract.
Is CMMC mandatory?
Yes, CMMC certification is mandatory for contractors bidding on or holding DoD contracts that include FCI or CUI. The required level will be specified in the contract. Full enforcement of CMMC 2.0 begins with the final rule implementation on 10 November 2025, so contractors must be prepared to meet the required level from that date onward.
Can I self-certify for CMMC?
Self-assessment is always required for Level 1. For Level 2, organizations handling non-prioritized programs may also complete a self-assessment, while prioritized programs require evaluation by a Certified Third-Party Assessor Organization (C3PAO). Level 3 assessments are conducted by the DoD and cannot be self-certified.
Who conducts CMMC audits?
Certified Third-Party Assessor Organizations (C3PAOs) conduct audits for Levels 2, while Level 3 assessments are led by the DoD. Level 1 can be self-assessed by the organization.
How long does it take to get certified?
Preparation typically takes 6–12 months, depending on the size and complexity of your organization. The assessment itself usually takes 3–5 days, with results issued within 90 days.
What are common pitfalls to avoid?
Common challenges include scoping errors, missing documentation, underestimating preparation time, lacking technical expertise, and mismanaging Plans of Action & Milestones (POA&Ms). Starting early and carefully scoping your systems helps reduce risk and ensures readiness.


















