CMMC documents: Everything you need to stay audit-ready

The Cybersecurity Maturity Model Certification (CMMC) represents a rigorous journey, demanding verifiable maturity in an organization’s security posture beyond mere technical controls. In the 2020 DoD Data Strategy, Deputy Secretary of Defense David Norquist described the Department’s guiding principles as "foundational to all data efforts in the DoD," stressing that leaders must "manage, secure, and use data for operational effect." For DoD contractors, this means the integrity of CMMC documentation is the definitive success factor; without a documented, defensible security plan, there is no real foundation for compliance.
Achieving CMMC compliance demands distinct standards at each tier. CMMC Level 1 requires evidence for 17 basic practices (FAR 52.204-21) to protect Federal Contract Information (FCI). CMMC Level 2 is significantly more involved, requiring artifacts for 110 security controls (NIST SP 800-171) to protect Controlled Unclassified Information (CUI), explicitly mandating comprehensive CMMC documents like a System Security Plan (SSP). This strong, centralized documentation fulfills all CMMC documentation requirements, ensuring contractors are continuously "audit-ready" for the triennial CMMC audit.
This blog breaks down all the essential CMMC documents you need, from policies and procedures to SSPs, POA&Ms, and evidence packages, so you can stay organized, compliant, and fully prepared for CMMC Level 1 or Level 2 assessments.
Quick refresher: What is CMMC, and why do documents matter
The CMMC is accurately described as a maturity model or framework, established by the DoD to assess the security practices of the DIB, rather than a standalone standard. It is built upon established standards like NIST SP 800-171 and FIPS 200, serving as an institutional guide to evaluate how well contractors protect FCI and CUI. Achieving CMMC compliance is fundamentally about transforming security from ad hoc actions into repeatable, institutionalized processes, a necessary exploration for every entity in the supply chain.
Documentation is the non-negotiable proof point for this transformation. It plays a critical role in risk reduction by formalizing security procedures and providing the necessary evidence for passing a CMMC assessment. Comprehensive CMMC assessment documentation proves that controls are actively managed and adhered to over time, moving an organization toward a verifiable state of readiness for CMMC compliance.
The documentation requirements vary significantly across the CMMC levels. Level 1 focuses on protecting FCI and requires records of adherence to 17 basic controls. CMMC Level 2 raises the bar, with a focus on CUI. This level requires extensive CMMC documentation, including SSPs, policies, and detailed evidence for all 110 NIST SP 800-171 controls, highlighting the differences in sensitivity and expected maturity across the CMMC levels.
Types of CMMC documents you must maintain
Navigating a CMMC assessment requires a comprehensive set of CMMC documentation types, moving from strategic planning to granular operational proof. These documents define the scope, establish formalized processes, and provide the indispensable CMMC evidence that your security posture is mature and repeatable.
Scoping is the first step in every C3PAO assessment and defines exactly what the assessor will review. Key artifacts include the CMMC Assessment Scope document, a clear system boundary description (separate from the SSP), CUI flow diagrams, network segmentation details, an in-scope/out-of-scope system list, and documented decisions for any external service providers. These are required under the CMMC Assessment Process (CAP).
The key artifacts required to demonstrate maturity are:
- System Security Plan (SSP): The essential master document serving as the detailed roadmap for all security controls within the defined system boundary.
- Plans of Action & Milestones (POA&M): A living document used to track and manage remediation efforts for any identified deficiencies or unimplemented controls.
- CMMC policies and procedures: Policies outline the organizational intent and rules, while procedures explain the step-by-step implementation, demonstrating institutionalization of CMMC policies.
- Incident response plan: A specialized document governing the organization's formal reaction and mitigation steps for security events.
- Asset inventory and network diagrams: These define the system's scope, physical boundaries, and the specific assets handling FCI or CUI.
- Evidence logs: The core of any assessment encompasses configuration exports, access reviews, audit trails, and logs, providing continuous proof that all policies are actively followed and serving as necessary CMMC evidence.
Core CMMC documentation for Level 1
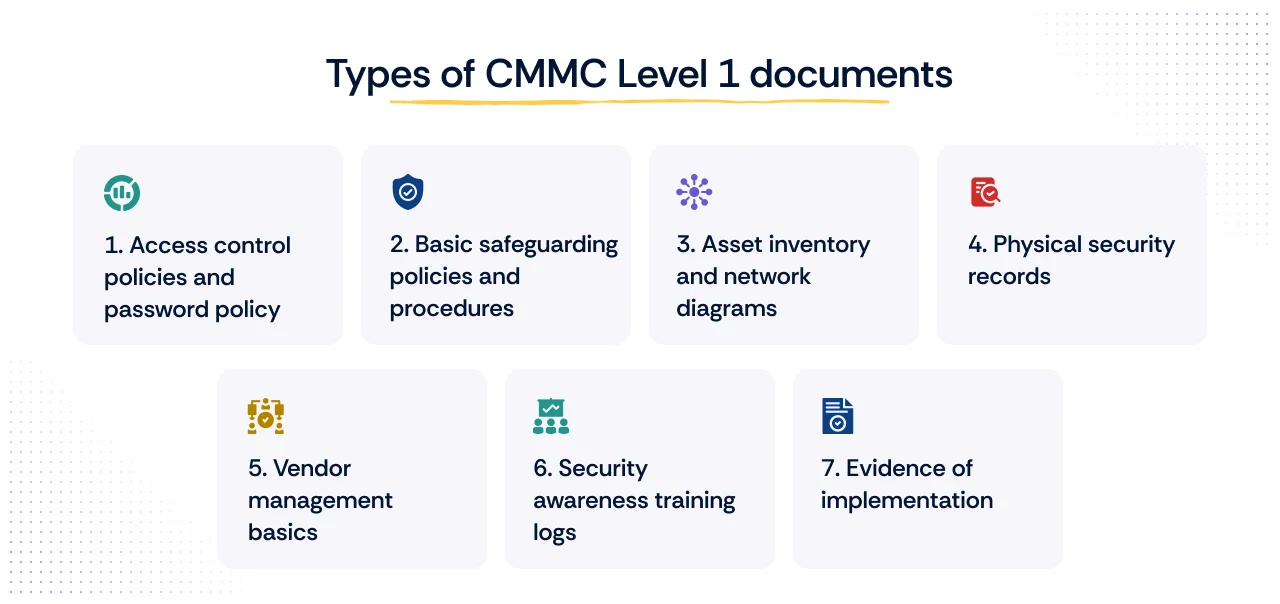
CMMC Level 1 represents the foundational tier, focusing on the basic safeguarding of FCI as mandated by FAR 52.204-21. While this level is characterized by self-assessment and does not strictly require a formal System Security Plan, the rigor behind the CMMC Level 1 documentation is essential for validating the continuous FCI safeguarding. The required artifacts move beyond mere records and serve as concrete Level 1 audit documents for a CMMC assessment.
The necessary documentation focuses heavily on operational procedures and proof of execution, directly supporting the 17 required practices:
A. Access control policies and password policy
These documents outline the controls for limiting system access (AC.L1-3.1.1) and dictating minimum password complexity. They establish the institutional rules for who can access FCI and how they authenticate. Access reviews form an integral part of CMMC certification.
B. Basic safeguarding policies and procedures
While a comprehensive SSP is not mandated, Level 1 requires simple written policies or procedures covering various practices. For example, documents governing media protection (MP.L1-3.8.3) and management of security flaws (SI.L1-3.14.1) ensure consistent application of controls.
C. Asset inventory and network diagrams
Cybersecurity asset management is foundational to defining the assessment boundary and identifying which systems handle or store FCI. Without a defined scope, effective security practices are impossible to prove.
D. Physical security records
Artifacts such as visitor logs, access-card swipe records, and documented facility entry-point controls provide concrete evidence that only authorised individuals have physical access to organisational systems, equipment, and operational environments, satisfying practice PE.L1-3.10.1 (‘Limit physical access to organisational info systems, equipment, and the respective operating environments to authorised individuals’) in the CMMC‑2.0 framework (Level 1).
E. Vendor management basics
Documentation outlining procedures for vendor access and system connections helps ensure that third-party risks are managed.
F. Security awareness training logs
Documentation proving that all users handling Federal Contract Information (FCI) have completed security-awareness training is mandatory evidence of compliance with practice AT.L1-3.2.1 (“Train employees on cybersecurity”) under the CMMC 2.0 Level 1 domain.
G. Evidence of implementation
This is the most critical category of CMMC evidence. It includes tangible artifacts, such as screenshots of firewall configurations, endpoint protection dashboards, user access reviews, and server hardening checklists. These documents provide undeniable proof that the mandated 17 practices are actually performed and functional for FCI safeguarding.
Core CMMC documentation for Level 2
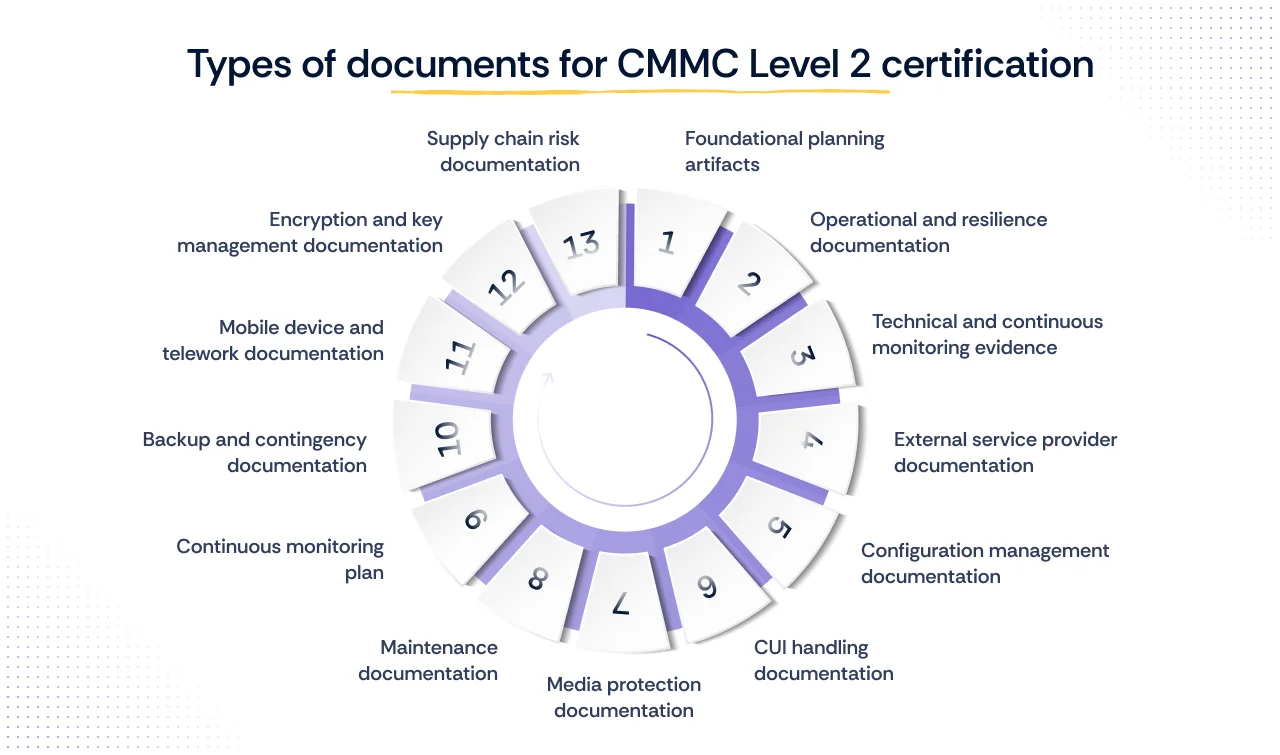
Achieving CMMC Level 2 represents the crucial step for CUI protection, requiring the implementation of all 110 security controls outlined in NIST SP 800-171. At this advanced tier, documentation moves from simple evidence of performance to formalized proof of institutionalization, becoming the primary focus of the C3PAO assessment. Incomplete or outdated documentation is a primary reason for failing an audit, making the integrity of CMMC Level 2 documentation the definitive measure of readiness.
A. Foundational planning artifacts
The assessment begins with two master documents that establish the compliance roadmap:
- Comprehensive System Security Plan (SSP): This document is the mandatory blueprint for CUI protection. It must provide a detailed explanation of the system boundary and, for each of the 110 NIST controls, describe precisely how the control is implemented within the organization’s environment. Assessors use the SSP as the roadmap to verify every practice and must be able to trace implementation details to verifiable evidence.
- Plans of Action and Milestones (POA&M): Required for conditional certification, the POA&M details a clear remediation path for any unimplemented controls, including resources, milestones, and assigned owners. CMMC requires these to be closed out within 180 days, underscoring the dynamic role of the POA&M in achieving full compliance.
B. Operational and resilience documentation
Level 2 mandates a deep suite of operational artifacts that demonstrate repeatable processes across all security domains:
- Detailed policies and procedures: Every security domain, from Access Control (AC) to System and Information Integrity (SI), requires formal, detailed procedures that explain the step-by-step methodology for meeting the 110 requirements. This includes specific configuration and change management records, ensuring all system modifications are documented and controlled.
- Risk assessment documentation: The Risk Management domain explicitly requires documented procedures for identifying, assessing, and mitigating system security risks. This documentation drives strategic prioritization of compliance efforts and informs decisions on control implementation.
- Resilience planning: Evidence of a tested Incident Response Plan is mandatory (IR controls). This plan must be supported by test records and coupled with documented business continuity and disaster recovery documents to prove system resilience against major disruptions.
- Security training and awareness: Moving beyond basic training, Level 2 requires evidence of role-based training, demonstrating that individuals with specific responsibilities (like system administrators or incident handlers) receive specialized instruction that is documented and verified.
C. Technical and continuous monitoring evidence
The bulk of the NIST 800-171 documentation consists of technical artifacts and logs that prove the effectiveness of security tools:
- Authentication evidence: Proof of multi-factor authentication (MFA) implementation for remote access and privileged access is mandatory, aligning with Identification and Authentication (IA) controls.
- Logging and monitoring artifacts: Comprehensive audit logs, configuration exports, and system monitoring records (AU and SI controls) must be maintained and easily retrievable to show continuous oversight of the CUI environment.
- Continuous monitoring evidence: To transition from intermittent audit preparation to perpetual readiness, documentation must demonstrate continuous monitoring. Automation platforms like Scrut Automation are vital here, as they seamlessly link live evidence from technical controls to the SSP, providing real-time assurance that the documented procedures are consistently performed.
D. External service provider documentation
The journey of CUI protection extends when an Organization Seeking Certification (OSC) relies on External Service Providers (ESPs), such as MSPs or cloud platforms. The ESP’s environment enters the assessment scope, making ESP documentation mandatory for assessors to verify control ownership.
Key artifacts required to define the security boundary and responsibility include:
- ESP inventory and boundary diagrams: Documentation listing all external providers and visualizing their connection points within the CMMC Assessment Scope.
- Shared Responsibility Matrix (SRM) / Customer Responsibility Matrix (CRM): The most crucial document, which explicitly maps every applicable CMMC control, defining precisely whether the OSC, the ESP, or both are responsible.
- FedRAMP authorization or equivalency evidence: For CSPs handling CUI under DFARS 252.204-7012, the OSC should be ready to show that the service meets FedRAMP Moderate or equivalent requirements (e.g., FedRAMP authorization package or formal equivalency documentation).
By maintaining this complete set of ESP documentation, the OSC ensures the assessor can trace control ownership, minimizing CMMC risks within the supply chain.
E. Configuration management documentation
Configuration management (CM) is foundational for maintaining the integrity and consistency of systems processing CUI. This domain, with its nine controls at Level 2, demands documentation that proves security is proactively established and enforced, not just manually configured once. Beyond simple screenshots, CM requires a defined, auditable process.
The necessary configuration management documentation suite includes:
- Configuration Management Plan (CMP): This procedural document defines the formal approach for all system changes, tracking, approvals, and implementation. It establishes the rules for control, covering the entire lifecycle of asset handling CUI.
- Baseline configuration standards: Mandatory for CM.L2-3.4.1, these standards document the known, trusted, and authorized security settings for all operating systems, applications, and network devices. Baselines serve as the definitive benchmark for system security.
- Secure configuration guidelines: Assessors look for documentation that references recognized hardening standards like CIS Benchmarks or DoD STIG guidelines. These documents show that the baseline configuration was derived from industry-accepted secure practices.
- Patch management and change records: The change management process is documented through detailed records that track, review, approve, and log all modifications to the baseline (CM.L2-3.4.3). Comprehensive patch management logs demonstrate the continuous system integrity required for CUI protection.
This detailed set of secure configuration documents ensures that the security posture remains stable and verifiable against the baseline configuration standards.
F. CUI handling documentation
Protecting CUI demands specialized CUI handling documentation that governs the information throughout its entire lifecycle. Assessors verify this mandatory documentation to confirm CUI is managed according to federal law (32 CFR Part 2002) and that policies are institutionalized.
This mandatory suite includes:
- CUI marking guide: Outlines mandatory rules for identifying CUI, ensuring personnel apply appropriate safeguarding controls.
- CUI storage and transmission rules: Procedures defining secure physical and digital storage locations, and mandating secure methods for internal and external CUI transmission.
- Encryption requirements for CUI: Documents specifying the mandatory use of FIPS-validated encryption when transmitting CUI outside the organizational boundary.
- CUI decontrol and destruction procedures: Processes aligned with NIST SP 800-88 that ensure information is properly decontrolled and permanently destroyed, preventing recovery and accidental disclosure.
Maintaining this rigorous set of documentation demonstrates maturity in data control and CUI protection.
G. Media protection documentation
The Media Protection (MP) domain of CMMC ensures the security of both digital and non-digital media containing CUI. Assessors require robust media protection documentation to verify that CUI is secured throughout its physical lifecycle, from storage to final disposal.
Mandatory procedures include:
- Media sanitization procedures: Documents, often aligning with NIST SP 800-88 standards, that detail the approved methods (destruction, purging) for sanitizing or destroying media containing CUI before its disposal or release for reuse.
- Removable media restrictions: Procedures that control the use of removable media on systems, including policies for prohibition, limited use, encryption, and the tracking of all such devices to maintain accountability.
- Labeling and handling guidance: Policies dictating the secure storage, physical control (check-out/check-in), and labeling of media with necessary CUI markings and distribution limitations. This prevents unauthorized access and disclosure during handling.
This documentation demonstrates rigorous CUI handling practices for physical assets.
H. Maintenance documentation
The Maintenance (MA) domain ensures that system maintenance, whether routine or emergency, does not create temporary vulnerabilities for CUI protection. Auditors require maintenance documentation that proves all activities are rigorously controlled, monitored, and securely managed across the lifecycle of assets.
Mandatory procedures and logs include:
- Controlled maintenance logs: Detailed logs and records (MA.L2-3.7.1) tracking all system maintenance, including dates, personnel, tools used, and authorization. This creates a transparent audit trail of all changes.
- Remote maintenance approval processes: Documented processes (MA.L2-3.7.5) for authorizing nonlocal sessions, requiring Multi-Factor Authentication (MFA), monitoring the connection, and ensuring immediate session termination upon completion.
- Vendor maintenance access rules: Formal rules (MA.L2-3.7.6) for controlling the tools, techniques, and personnel used. This includes supervision and strict access limits for vendor personnel without required security authorization.
This documentation demonstrates that CUI systems are secured even during periods of operational change, providing verifiable assurance of controlled maintenance.
I. Continuous monitoring plan
Achieving continuous audit readiness requires a documented continuous monitoring plan, which formalizes the ongoing vigilance required to protect CUI (CA.L2-3.12.3). This plan transitions compliance from a periodic checklist into a proactive, systematic process that maintains the integrity of the security controls.
The plan must explicitly document:
- Roles and responsibilities: Clearly defining who is accountable for monitoring activities, analysis, reporting, and updating the overall plan.
- Tools and frequency: Outlining the specific automated tools (e.g., SIEM, EDR) used for ongoing monitoring, along with defined frequencies for vulnerability scans, log reviews, and control assessments.
- Alert thresholds and escalation paths: Documented procedures establishing the baseline of normal system behavior, defining the thresholds for security alerts, and specifying the immediate escalation paths that initiate the Incident Response (IR) process.
This plan ensures that the documented security posture is tested and maintained in real time against evolving threats.
J. Backup and contingency documentation
The Recovery (RE) domain ensures that the organization can rapidly restore CUI and critical operations following a system disruption. Assessors review backup and contingency documentation to verify that CUI protection is assured, even during and after a disaster.
Mandatory artifacts that prove resilience include:
- Contingency Plan (CP): The strategic document outlining procedures for restoring the CUI environment and resuming operations after an adverse event.
- Backup policy: A detailed policy dictating the frequency, type, retention schedules, and secure storage of CUI backups, aligned with the relevant NIST SP 800-171 requirements for protecting backup CUI.
- Backup test records and recovery test evidence: Evidence showing that backup and recovery capabilities are periodically tested and effective, as expected by the CMMC Recovery (RE) practices at Level 2.
This documentation demonstrates institutional commitment to protecting CUI throughout all phases of recovery.
K. Mobile device and telework documentation
As the CUI environment extends to home offices and mobile endpoints, CMMC documentation must govern these remote access points to maintain CUI protection. Assessors verify that contractors have defined controls over all endpoints that fall outside the traditional office perimeter.
Mandatory documentation includes:
- Mobile device policy: Formal rules (AC.L2-3.1.18) controlling the connection and use of mobile devices, including requirements for encryption of CUI at rest, strong authentication, and mandated security applications.
- BYOD policy: If personally owned devices (BYOD) access CUI, this policy outlines strict security controls, monitoring parameters, and data segregation requirements that the personal device must satisfy to remain compliant.
- Telework security guidelines: Comprehensive guidelines (PE.L2-3.10.6) securing alternative work sites. These specify physical security rules (locking devices, protecting documents) and mandate technical controls like VPNs and MFA for remote access.
This documentation ensures compliance with the CUI, regardless of the employee's physical location, addressing the security challenges of remote work.
L. Encryption and key management documentation
Encryption and key management documentation is critical for safeguarding the confidentiality of CUI, particularly when data is outside the secure boundary (SC.L2-3.13 controls). Assessors require comprehensive procedures to verify that cryptographic mechanisms are correctly applied and securely managed.
Mandatory artifacts include:
- Encryption standards for data at rest/in transit: Documentation specifying the FIPS-validated cryptography used to protect CUI on mobile devices (data at rest) and during transmission over untrusted networks (data in transit).
- Key management procedures: Formal procedures detailing the entire lifecycle of cryptographic keys, covering their generation, distribution, storage, and destruction to prevent unauthorized access.
- Certificate inventory and configuration: A complete certificate inventory of all TLS certificates and private keys, supported by documented VPN and TLS configuration protocols that secure remote access and CUI transmission sessions.
This documentation demonstrates institutional control over cryptographic defenses, a fundamental element of CUI protection.
M. Supply chain risk documentation
The supply chain risk documentation verifies that the organization proactively addresses security risks introduced by external parties and subcontractors (SR.L2-3.14 controls). This ensures that CUI protection is consistently maintained throughout the entire defense industrial base.
Mandatory artifacts required for a CMMC assessment include:
- Supplier risk management policy: A formal policy detailing the process for identifying, assessing, and continuously monitoring risks posed by vendors and external systems connected to the CUI environment.
- Vendor evaluation records: Documentation of due diligence, including background checks or third-party assessment results, that verify a vendor’s security capabilities before engagement.
- Subcontractor CUI-handling agreements: Formal contracts ensuring that CUI-handling requirements are flowed down to all subcontractors who handle or access CUI, as mandated by DFARS.
This documentation demonstrates institutional control over third-party risk.
Core CMMC documentation for level 3
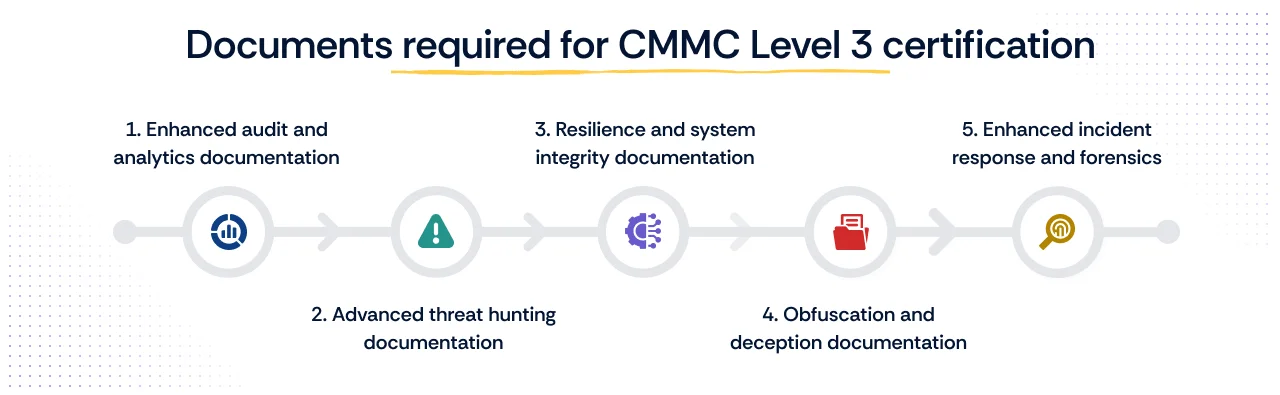
CMMC Level 3 is reserved for contractors supporting the most sensitive DoD programs, requiring enhanced security controls and adversary-focused protections. This tier aligns with the demanding requirements of NIST SP 800-172, going beyond Level 2’s foundational controls.
CMMC Level 3 documentation must include all Level 2 artifacts (SSP, POA&M, 110 policies) and demonstrate institutionalized maturity across the entire organization. Key additions include:
- Proactive Detection and Response Strategies: Detailed procedures for threat hunting, forensic analysis, and advanced incident response capabilities.
- Enhanced Resilience Plans: Comprehensive organizational documentation demonstrating high-level recovery and continuity protocols designed to defeat sophisticated Advanced Persistent Threats (APTs).
- Verification Evidence: Records of advanced security testing, such as Red Team or penetration testing, which prove the effectiveness of the enhanced controls.
Documentation at this level must prove that security is proactive, adaptive, and resilient, ensuring the highest level of CUI protection.
A. Enhanced audit and analytics documentation
CMMC Level 3 demands documentation of advanced detection capabilities to counter sophisticated threats. This goes far beyond basic log retention, requiring proof of dynamic analysis and threat hunting.
Mandatory documentation includes:
- SIEM correlation rules and tuning: Detailed documents explaining the logic and thresholds used in the Security Information and Event Management (SIEM) system to correlate events and generate actionable alerts, minimizing false positives.
- Advanced audit analytics: Documentation proving the use of automated techniques (AU.L3-3.3.6) to analyze audit logs for patterns indicative of malicious or unauthorized behavior.
- Insider threat monitoring and behavioral analytics: Procedures and evidence detailing the tools used to monitor user activity, establish baselines of normal behavior, and flag anomalies to detect potential insider threats (AU.L3-3.3.7).
This documentation confirms the organizational ability to detect and respond to threats that evade conventional defenses.
B. Advanced threat hunting documentation
CMMC Level 3 requires advanced threat hunting documentation (CA.L3-3.12.4) to prove the organization is proactively searching for, rather than just reacting to, sophisticated threats. This demonstrates an adversary-focused approach to CUI protection.
Mandatory artifacts include:
- Threat hunting procedures: Formal, repeatable procedures outlining the methodology used to search logs and network data for indicators of compromise (IOCs) or undetected malicious activity.
- Adversary behavior analysis: Documentation detailing the specific Tactics, Techniques, and Procedures (TTPs) of relevant threat actors, which guides the focus of the hunt team.
- Threat intelligence ingestion processes: Procedures for sourcing, validating, and automatically integrating external threat intelligence feeds to inform SIEM correlation rules and active hunt activities.
- Hunt team workflows: Documentation detailing how hunts are initiated, executed, and how findings are escalated into the formal incident response or remediation lifecycle.
This suite proves the institutionalization of proactive defense.
C. Resilience and system integrity documentation
CMMC Level 3 requires documentation proving cyber resiliency and damage-limiting operations against Advanced Persistent Threats (APTs). This focus on system integrity and rapid recovery is derived from NIST SP 800-172 controls.
Mandatory documentation includes:
- System isolation procedures: Policies and network diagrams (SC.L3-3.13.4e) detailing the logical or physical separation of CUI processing environments to minimize the damage and scope of a potential compromise.
- Secure boot and hardware integrity validation: Procedures and logs proving the use of technologies like Trusted Platform Modules (TPMs) and secure boot mechanisms to continuously validate the integrity of system components and firmware against tampering.
- Rapid recovery plans: Enhanced plans and test records outlining resilient recovery pathways that ensure mission assurance and the rapid recovery of CUI, often involving immutable backups and automated recovery solutions.
This documentation demonstrates the institutional ability to protect CUI integrity and guarantee system survivability.
D. Obfuscation and deception documentation
CMMC Level 3 is unique in requiring active defense, where obfuscation and deception documentation proves the organization’s ability to proactively misdirect and confuse adversaries. This moves defense beyond prevention to manipulation, demonstrating a mature approach to CUI protection.
Mandatory artifacts include:
- Honeytokens and decoy assets: Policies and procedures (SC.L3-3.13.16e) detailing the deployment and monitoring of intentionally false assets, credentials (honeytokens), or network segments designed to lure and detect an adversary.
- Deception techniques: Documentation outlining the active methods used to confuse or frustrate an adversary post-breach, such as manipulating false environmental data or altering perceived system configurations.
- Adversary misdirection documentation: The strategic plan showing how the deployed decoy assets and deception techniques are used to draw the adversary away from genuine CUI, protecting the critical information.
This documentation suite demonstrates a highly evolved, adversary-focused security posture.
E. Enhanced incident response and forensics
CMMC Level 3 requires enhanced incident response capabilities to counter Advanced Persistent Threats (APTs), necessitating documentation that supports deep investigation and rapid recovery. This moves the response from simple remediation to full-scale forensic analysis.
Mandatory artifacts include:
- Forensic readiness plans: Proactive documentation detailing the procedures, tools, and roles required for efficiently collecting, preserving, and analyzing digital evidence (IR.L3-3.6.1e). This ensures data integrity for post-incident review.
- Deep incident analysis documentation: Procedures and records that go beyond containment to conduct thorough root cause analysis, mapping the adversary’s Tactics, Techniques, and Procedures (TTPs) within the CUI environment.
- Reverse engineering workflows: Documentation outlining the technical processes for analyzing captured malicious code or attack artifacts to fully understand the threat and develop better defensive countermeasures.
This suite proves institutional commitment to damage-limiting operations and sophisticated threat analysis.
Mandatory documents for CMMC assessments
Third-party assessments, particularly for CMMC Level 2, are structured around the principle of 'document, implement, and prove'. Certified Third-Party Assessor Organizations (C3PAOs) meticulously examine artifacts to verify that an Organization Seeking Certification (OSC) has fully institutionalized the required security practices for CUI protection. These CMMC assessment artifacts serve as the definitive CMMC audit documents and are mandatory for beginning the formal review process.
The C3PAO's review begins with an analysis of strategic documentation before moving to technical evidence.
A. Strategic and foundational documentation
- System Security Plan (SSP): This is the mandatory master document for any assessment involving CUI (Level 2). It must be comprehensive, detailing the system boundary, scope, and exactly how the organization implements each of the 110 NIST SP 800-171 controls. The SSP is the assessor’s roadmap for the entire engagement.
- Plans of Action and Milestones (POA&M): If the organization is seeking conditional Level 2 certification, a POA&M is mandatory. It must clearly outline any unfulfilled controls, assign ownership, and define a remediation timeline, which CMMC currently limits to 180 days.
- Policies and procedures: Assessors require a full set of written CMMC policies that reflect organizational intent and detailed procedures that explain the step-by-step methodology for executing all 110 controls. This shows the repeatability and institutionalization of the security program.
- Contractor affirmations or attestations: For both Level 1 and Level 2, an annual contractor affirmation from a senior executive is required to be submitted to the Supplier Performance Risk System (SPRS), formally attesting to the organization's compliance status.
B. Technical and evidentiary documents
The C3PAO validates the strategic documents against live system configuration and operational records:
- Evidence package mapped to each practice: This is the core of the C3PAO documentation request. The evidence package is a collection of artifacts, including screenshots, configuration files, access review logs, and audit trails, that directly map to and prove the implementation of every security practice. Automation is key to continuously maintaining this crucial evidence.
- Inventory of assets processing FCI/CUI: A detailed list of all devices, applications, servers, and cloud services that store, process, or transmit FCI or CUI is mandatory to define the exact assessment scope and boundary.
- Network diagrams: Assessor teams require current network diagrams showing the flow of CUI and the segmentation of the CUI environment (enclave) from the non-CUI environment.
- Policies showing enforcement and version control: Documentation must demonstrate an enforced process for regular review, version control, and approval of all security documents. Assessors check to ensure policies are current and that employees are working from the most recent versions.
- Incident records (where applicable): Any records pertaining to previous security incidents or breach history must be available for review to demonstrate the effectiveness and operational success of the Incident Response Plan.
- Previous assessment reports (if any): Any reports from prior NIST SP 800-171 self-assessments or mock audits are used by the assessor to understand the history of compliance gaps and remediation efforts.
Fresh evidence: Automation collects real-time logs, configurations, and screenshots continuously:
How Scrut can help you stay audit-ready
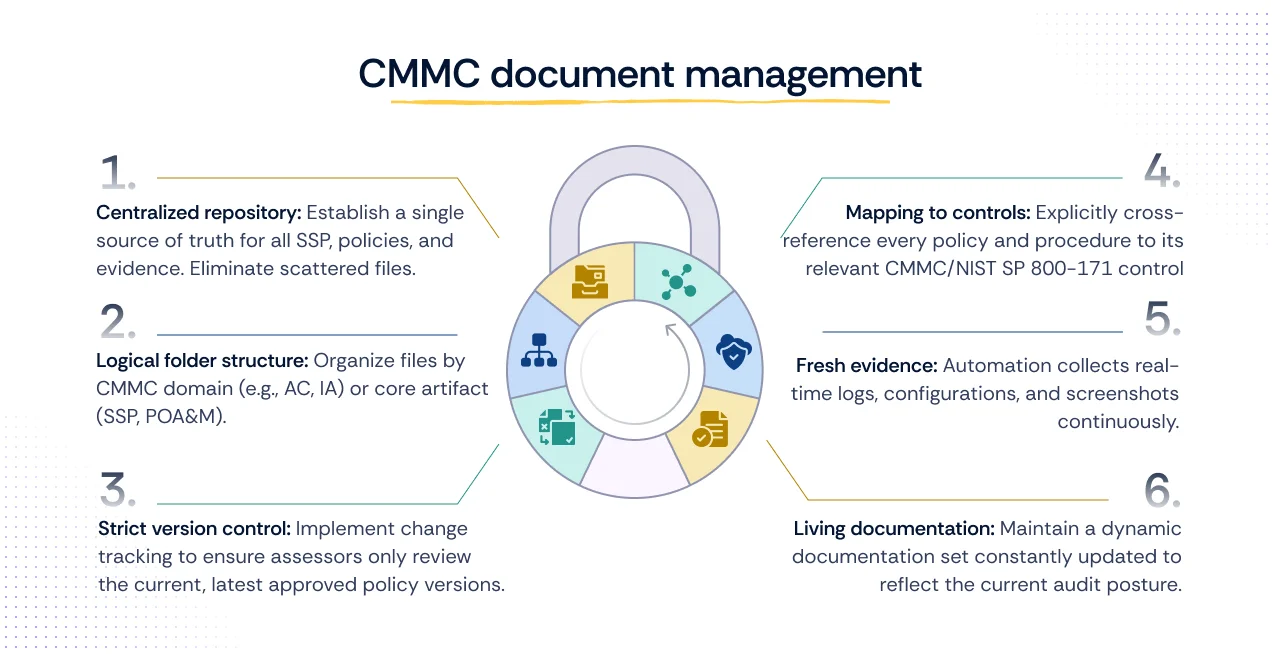
The complexity of CMMC documentation and the imperative for continuous CUI protection necessitate a shift from manual effort to intelligent CMMC automation. Scrut transforms the compliance process by serving as an end-to-end compliance automation platform, ensuring DoD contractors maintain perpetual audit readiness.
Scrut eliminates manual documentation gaps through several key capabilities. It provides automated evidence collection, seamlessly integrating across cloud environments, applications, and devices to gather logs, configuration settings, and screenshots. This establishes a single, continuous source of truth. The platform features pre-mapped controls, which automatically link collected evidence and required artifacts to the 110 NIST SP 800-171 practices, addressing the critical mistake of missing control-to-artifact mapping.
Furthermore, Scrut centralizes document management and continuously monitors your security posture. This assures the SSP reflects current reality and allows for instant, auditor-friendly exports of the entire CMMC evidence package. By automating evidence maintenance and consolidating documentation, Scrut dramatically reduces the time and effort required to navigate a C3PAO assessment.
Ready to transform your CMMC documentation from a compliance burden into a source of continuous assurance? Take the definitive step toward CUI protection and verifiable maturity.

Frequently asked questions about CMMC documentation
What is CMMC documentation?
CMMC documentation includes the mandatory artifacts, policies, procedures, and evidence logs required by the DoD to prove a contractor's security practices are mature, repeatable, and effective at protecting FCI and CUI.
What documents are mandatory for a CMMC level 2 audit?
The core documents are the System Security Plan (SSP), Plans of Action and Milestones (POA&M), comprehensive security policies and procedures, and a full evidence package mapped to all 110 NIST SP 800-171 controls.
What is the difference between CMMC level 1 and level 2 documentation?
Level 1 documentation focuses on evidence of performance for 17 basic practices protecting FCI. Level 2 requires formal, institutionalized documentation, notably a comprehensive SSP and detailed procedures, to protect CUI.
Why is the SSP so important for CMMC documentation?
The SSP is the mandatory blueprint for your CUI environment. It serves as the assessor's roadmap, detailing exactly how the organization implements every required security control, and is the first document reviewed.
What is a POA&M in CMMC documentation?
A Plan of Action and Milestones (POA&M) is a document that tracks remediation plans, milestones, and timelines for any security controls that are not yet fully implemented, a requirement for achieving conditional CMMC certification.
What types of CMMC evidence do assessors look for?
Assessors look for tangible proof, including automated audit logs, configuration screenshots, access review records, and system monitoring artifacts, all linked to specific controls.
How can CMMC documentation be kept "living"?
Documentation is kept "living" by using continuous monitoring and compliance automation platforms, which automatically update evidence and sync the SSP with the current security posture.


















