CMMC certification process: A complete step-by-step guide

The Defense Industrial Base (DIB), a critical component of national security, is an increasingly frequent target of sophisticated cyberattacks. This persistent threat to the supply chain led the Department of Defense (DoD) to refine its cybersecurity mandate, culminating in the Cybersecurity Maturity Model Certification (CMMC) 2.0 program. As the DoD has officially launched its phased rollout, which began in November 2025, DoD contractor requirements for securing sensitive information are now contractually enforceable.
This shift moves beyond self-attestation, focusing on verifiable assurance that contractors can adequately protect Federal Contract Information (FCI) and Controlled Unclassified Information (CUI). The core of this effort is ensuring that all entities entrusted with CUI meet the strict requirements of NIST SP 800-171, with compliance status and scores recorded in the Supplier Performance Risk System (SPRS).
The DoD's commitment to enhancing cyber resilience is evident, with the CMMC 2.0 framework streamlining requirements into three distinct levels, making the CMMC certification process a vital strategic priority for any company seeking to maintain or gain DoD contracts.
Deciphering CMMC 2.0 certification: Levels of assurance
The CMMC 2.0 framework moves beyond mere documentation, requiring defense contractors to demonstrate the implementation and maturity of cybersecurity controls based on the sensitivity of the information they handle. What constitutes "certification" varies fundamentally across the three assessment levels, reflecting the risk-based approach to securing the supply chain.
For a comprehensive understanding of the CMMC 2.0 program, including the final rule details, you can refer to the official DoD Chief Information Officer's CMMC page:
CMMC level 1: Foundational (basic safeguarding of FCI)
- What certification means: For Level 1, certification is achieved through a required annual self-assessment.
- Requirements and controls: This level requires compliance with the 17 basic safeguarding requirements for Federal Contract Information (FCI), derived from Federal Acquisition Regulation (FAR) clause 52.204-21. These controls represent basic cyber hygiene.
- Assessment: The organization conducts a self-assessment annually.
- Affirmation: A senior company official must affirm compliance, with the results uploaded to the SPRS. No Plan of Action & Milestones (POA&Ms) are permitted; all 17 practices must be fully implemented at the time of affirmation.
CMMC level 2: Advanced (protection of CUI)
- What certification means: For Level 2, the meaning of certification splits based on the criticality of the contract and the CUI involved.
- Requirements and controls: This level requires the implementation of all 110 security requirements detailed in NIST Special Publication (SP) 800-171 Revision 2, which are designed to protect CUI.
- Assessment Type 1: Third-Party Assessments (for prioritized acquisitions): Most contractors handling CUI on critical programs will require a triennial third-party assessment conducted by an accredited CMMC Third-Party Assessment Organization (C3PAO).
- This formal audit results in a conditional or final CMMC certificate, which is valid for a period of three years.
- Assessment Type 2: Self Assessment (for non-prioritized acquisitions): Contractors working on contracts deemed less critical by the DoD may be permitted to use an annual self-assessment, similar to Level 1. This eligibility must be explicitly stated in the contract solicitation.
- Affirmation: Regardless of the CMMC assessment type (C3PAO or self), an annual affirmation of compliance must be submitted to maintain the three-year certification or assessment status. POA&Ms are generally permitted for a limited number of non-critical controls, which must be closed out within 180 days to achieve a final certification.
CMMC level 3: Expert (protection against APTs)
- What certification means: Certification at Level 3 represents the highest level of assurance, reserved for the most sensitive CUI and critical defense programs.
- Requirements and controls: This level builds upon all 110 NIST SP 800-171 requirements (Level 2) and adds a subset of approximately 24 enhanced security requirements from NIST SP 800-172, specifically targeting protection against Advanced Persistent Threats (APTs).
- Assessment: This level requires government assessments only, conducted every three years by the Defense Contract Management Agency’s (DCMA) Defense Industrial Base Cybersecurity Assessment Center (DIBCAC).
- Pre-requisite: An organization must have achieved a final Level 2 certification (via a C3PAO assessment) for the same assessment scope before pursuing Level 3.
- Affirmation: Annual affirmations of compliance are also required to maintain this expert status.
The CMMC compliance process
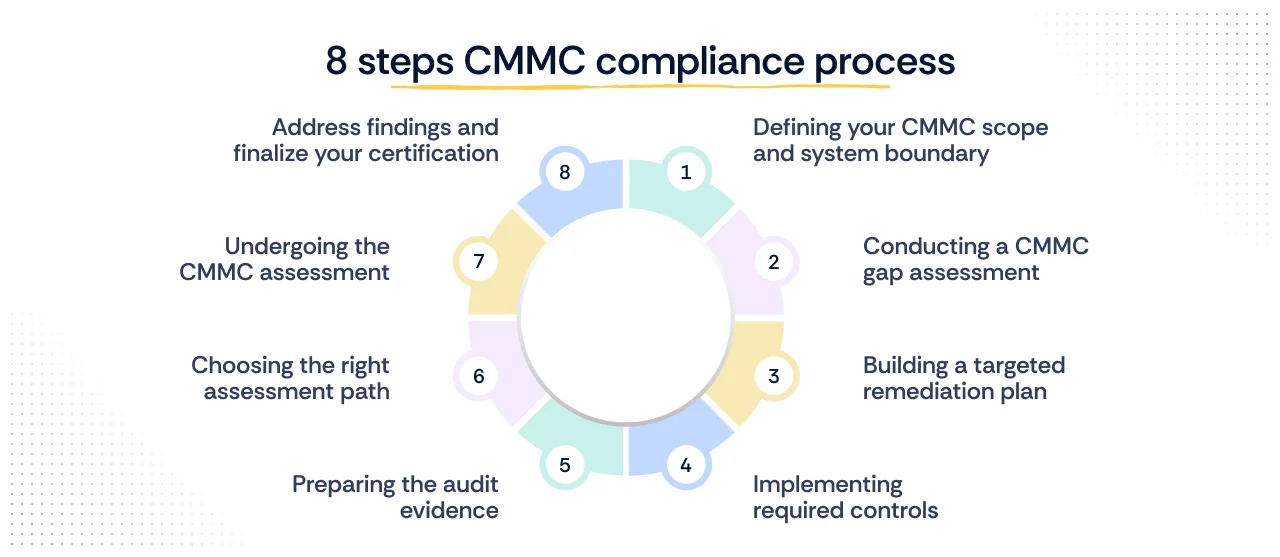
The CMMC certification process is a structured, phased process designed to build a robust and continuously compliant security posture. It moves from defining the boundaries of sensitive data to implementing, documenting, and validating the necessary security controls. These steps are critical for any organization seeking to meet DoD contractor requirements and effectively protect CUI under the CMMC 2.0 framework.
Step 1: Defining your CMMC scope and system boundary
The critical first move toward a successful CMMC certification process is accurately defining your assessment scope. This involves identifying the CUI environment, every location where CUI is stored, processed, or transmitted. You must clearly map all assets, users, applications, and cloud services that interact with CUI or the less sensitive FCI scope (for Level 1).
This mapping establishes the system boundary, the logical and physical perimeter subject to assessment. Failure to correctly scope is a significant risk; under-scoping leaves CUI vulnerable, while over-scoping dramatically increases the cost of implementing the necessary controls. A smart strategy is to leverage enclaves, isolating CUI within a secure segment to minimize the system boundary and streamline compliance efforts against the NIST SP 800-171 requirements for CMMC 2.0.
Step 2: Conducting a CMMC gap assessment
The second crucial step involves performing a rigorous gap analysis to measure your current security posture against the mandatory CMMC practices. This process compares the security controls implemented within your defined system boundary against the specific requirements of your target level.
- Level 2 Focus: For organizations handling CUI, this means meticulously comparing existing controls with the 110 requirements of NIST SP 800-171.
- Level 1 Focus: For FCI protection, the comparison is against the 17 basic safeguarding requirements derived from FAR 52.204-21.
This assessment must peel back the layers of the organization to identify not just technical weaknesses, but also process and documentation gaps. Crucially, the analysis must uncover how external relationships affect compliance, addressing control inheritance from cloud providers and defining shared responsibilities with all external service provider partners. The resulting gaps form the basis for your POA&M, which is essential for achieving CMMC certification.
Step 3: Building a targeted remediation plan
The gap analysis findings serve as the blueprint for creating a robust remediation plan, formally documented as a POA&M. This plan is crucial for managing the path to full control implementation.
The first action is to prioritize all deficits using a risk-based approach, focusing first on the highest-impact findings related to protecting CUI. Each remediation task must be clear, with specific assignments for owners, allocated budgets, and definitive deadlines. Crucially, the plan must incorporate policy updates and process changes, as compliance is often more about operational rigor than mere technology deployment.
The CMMC 2.0 Final Rule places strict limits on the POA&M. It is a temporary fix, not a strategy. For Level 2, an organization can receive Conditional Certification if it meets a minimum score threshold and agrees to remediate all open items within 180 days of the assessment. However, certain high-value, critical requirements, such as those related to Multi-Factor Authentication (MFA), cannot sit on a POA&M; they must be fully implemented at the time of the initial assessment to maintain eligibility for defense contracts.
Step 4: Implementing required controls
With a POA&M in place, the next phase is the actual control implementation. This involves turning the theoretical requirements into operational reality across your CUI environment. For Level 2, the goal is to fully implement all 110 requirements from NIST SP 800-171, covering both technical controls (e.g., system configuration, access restrictions) and operational policies.
However, compliance is not solely about technology; it hinges on demonstrating maturity. A significant portion of this step is updating essential documentation. This includes revised policies, procedures, system security plans (SSPs), network diagrams, asset inventories, and evidence of mandatory employee training. The goal is to avoid drowning in documentation and instead focus on clarity and consistency that brings the controls to life. This operational rigor is essential.
Crucially, this phase establishes a culture of continuous monitoring. The documentation, system configurations, and operational evidence must be treated as living documents, constantly updated to ensure ongoing compliance.
Step 5: Preparing the audit evidence
The penultimate step before a formal assessment is the methodical preparation of comprehensive audit evidence, often referred to as artifacts. This phase requires the organization to shift from control implementation to demonstrative proof, showing an external assessor that the security framework is not only documented but also actively operating.
Acceptable evidence spans various formats, including policy documents that define the rules, configuration baselines, system diagrams, and inventory lists that define the scope. Crucially, it also includes operational proof, such as logs, screenshots of security tool dashboards, training records, and incident response artifacts. This evidence must demonstrate ongoing compliance and effective operation of the 110 requirements for Level 2. Key documents like the SSP and the POA&M must be finalized and fully supported by this evidence.
Step 6: Choosing the right assessment path
Selecting the correct assessment path is defined by your target CMMC level and the specific DoD contractor requirements stated in the contract solicitation. This choice dictates whether you undergo a third-party audit or a self-attestation.
- Level 1 (FCI): Requires an annual self-assessment, affirmed by senior management and reported to SPRS.
- Level 2 (CUI): The path splits. Non-prioritized acquisitions allow for an annual self-assessment. However, the majority of contractors handling CUI will require a triennial assessment by a CMMC C3PAO. The C3PAO is an accredited entity responsible for verifying compliance with the 110 requirements of NIST SP 800-171.
- Level 3 (Advanced CUI): Requires a triennial assessment conducted solely by the government’s DIBCAC.
It is crucial to verify the availability of an accredited C3PAO early, as scheduling and preparation are time-intensive. Successful completion of the assessment, whether self-assessment or formal audit, leads to the validated compliance status necessary to bid on CMMC-mandated contracts, thereby completing the CMMC certification process.
Step 7: Undergoing the CMMC assessment
The final step in the CMMC certification process is the formal assessment, whether conducted by a C3PAO for Level 2 or by the DIBCAC for Level 3. The CMMC assessment is a comprehensive audit designed to validate that the security practices are operating effectively within the defined system boundary.
The process involves several key activities:
- Documentation review: The assessor scrutinizes the SSP and POA&M, ensuring all required policy documents and operational artifacts are present.
- Interviews: Personnel are interviewed to verify their understanding and execution of security procedures.
- Sampling and testing: The assessor selects a sample of systems and processes for technical testing and review, verifying the existence of objective evidence such as configuration settings and logs.
Each of the 110 requirements (for Level 2) is graded on an "Implemented/Not Implemented" basis. Any finding of "Not Implemented" directly impacts the final score. Resilience is crucial, as cybersecurity is a trampoline, not a wall; teams must be ready to quickly address and bounce back from minor findings, especially those that can be addressed within the limited POA&M for conditional certification. The assessor's validation confirms the organization's sustained readiness to protect CUI.
Step 8: Address findings and finalize your certification
The final segment of the CMMC certification process involves responding to the assessment findings and formally achieving your compliance status. Following the audit, any identified gaps or deficiencies must be addressed via swift and effective corrective actions.
- POA&M closure: For conditional Level 2 certifications, the organization must complete all open POA&M items, those limited, non-critical requirements, and submit conclusive audit evidence of their implementation to the C3PAO within the strict 180-day deadline. This evidence demonstrates that all remediation tasks are fully closed.
- Certification decision: Once all requirements are validated, the assessor forwards the final report for quality assurance and the ultimate certification decision. The organization then receives a formal certification (for C3PAO-assessed Level 2 and DIBCAC-assessed Level 3) or a final validation (for self-assessment Level 1 and certain Level 2 contracts).
- SPRS submission: The certification status or final compliance assertion is then submitted to the SPRS. This step is critical, as it is the official record the DoD uses to verify that the contractor meets the cybersecurity posture required by the contract, confirming full adherence to the DoD contractor requirements.
How long does the CMMC certification process take?
The total duration of the CMMC certification process is highly variable, primarily dependent on your organization's current cybersecurity maturity (the readiness timelines) and the target level under CMMC 2.0.
How Scrut helps you accelerate the CMMC certification process
Scrut helps you move through the CMMC certification process with fewer hurdles by automating the work that usually slows teams down. You get CMMC automation that collects evidence in the background, maps every requirement to the right control, and tracks training management without chasing spreadsheets.
With 100+ integrations and automated tests that run every day, you stay in continuous compliance instead of scrambling right before an assessment. Workflows keep owners aligned, document updates move in sync, and your entire CUI environment stays visible in one place.
The result feels less like a paper chase and more like a choreographed dance where every step has a clear purpose. Scrut helps you think ahead so you never risk a last-minute scramble or a missed requirement.

FAQs
What is CMMC 2.0, and who must comply?
CMMC 2.0 (Cybersecurity Maturity Model Certification) is a Department of Defense (DoD) program designed to verify that DoD contractor requirements for cybersecurity are met throughout the Defense Industrial Base (DIB). All contractors and subcontractors handling Federal Contract Information (FCI) or Controlled Unclassified Information (CUI) on non-federal systems must comply with the required CMMC level specified in the contract solicitation.
What are the key differences between the CMMC levels for certification?
The three levels define the required assessment and controls:
- Level 1 (Foundational): Protects FCI using 17 basic requirements. Certification is via an annual self-assessment submitted to SPRS.
- Level 2 (Advanced): Protects CUI using the 110 requirements of NIST SP 800-171. Certification requires a triennial third-party assessment by a C3PAO for most contracts, or an annual self-assessment for non-prioritized acquisitions.
- Level 3 (Expert): Protects high-value CUI against Advanced Persistent Threats (APTs), requiring a subset of NIST SP 800-172 controls and a triennial government assessment by the DIBCAC.
Is a Plan of Action & Milestones (POA&M) allowed for CMMC 2.0?
POA&Ms are not permitted for CMMC Level 1. They are permitted for Level 2 and Level 3, but with strict limitations. The DoD Final Rule mandates that certain critical security practices (like Multi-Factor Authentication for CUI) cannot be placed on a POA&M and must be fully implemented at the time of assessment. All permitted POA&M closure items must be remediated and verified within 180 days of receiving Conditional Certification.
How is the CMMC assessment scope defined?
Scoping defines the system boundary of the information system subject to assessment. This is critical for managing the CMMC certification cost. The scope encompasses all assets (people, technology, and facilities) that process, store, or transmit CUI (the CUI environment) and all security protection assets (SPAs) that secure that environment. Organizations often use an enclave strategy to reduce the overall system boundary.
How often must CMMC certification be renewed?
CMMC certification requires verification on a recurring cycle:
- Level 1 requires an annual self-assessment and affirmation of continued compliance.
- Level 2 and Level 3 require a full reassessment every three years (triennial), plus an annual affirmation of continued compliance submitted to SPRS. This ensures sustained compliance and effective monitoring of the CUI environment.


















