Choose risk-first compliance that’s always on, built for you.
Go back to blogs
Security Controls: Types, Functions, and Best Practices
Last updated on
April 21, 2025
min. read

Cyber threats are escalating at an alarming pace, putting businesses at greater risk than ever. In 2024, the global average cost of a data breach surged to $4.88 million, reflecting a 10% increase from the previous year. Organizations are now facing an average of 1,876 cyberattacks per week—75% more than in 2023. To counter these risks, businesses rely on security controls—measures designed to prevent, detect, and respond to cyber threats effectively.
This blog will explore the different types of security controls, how they function, and why a layered security approach is crucial for safeguarding systems and data.
What are Security Controls?
Security controls are measures designed to protect systems, networks, and data from cyber threats. They help prevent, detect, and respond to security risks, minimizing vulnerabilities and limiting potential damage. By implementing these controls, organizations can strengthen their defenses against cyberattacks and data breaches.
Additionally, robust security controls are essential for meeting security compliance requirements, ensuring that organizations adhere to industry regulations and standards.
What are the main types of Security Controls?
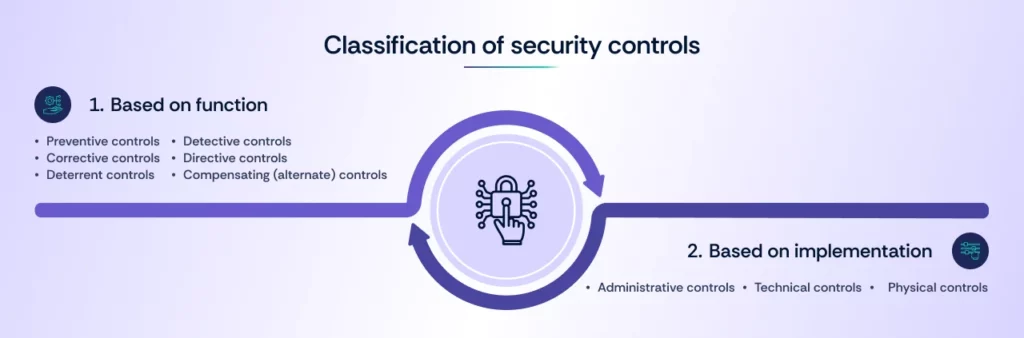
Security controls can be categorized into several types based on their function and implementation. The main types include:
1. Based on function
These security controls are categorized by how they respond to security threats and their role in an organization’s defense strategy.
1.1 Preventive controls
Preventive controls are proactive measures designed to stop security incidents or compliance violations before they occur. These controls help mitigate risks by establishing policies, procedures, and safeguards such as access controls, encryption, and security training.
- Purpose: Stop security incidents before they occur. However, they are not foolproof and can be bypassed by sophisticated attacks.
- Main function: Reduce the attack surface by blocking threats and preventing unauthorized access.
- Examples:
- Firewalls that block malicious traffic.
- Multi-factor authentication (MFA) to prevent unauthorized logins.
- Encryption to protect sensitive data.
- Security awareness training to prevent human error-based attacks.
1.2 Detective controls
Detective controls are security measures designed to identify and alert organizations to security incidents or policy violations after they occur.
- Purpose: Identify and alert organizations about security incidents by monitoring systems for suspicious activity.
- Main function: Provide visibility into security threats that may bypass preventive measures.
- Examples:
- Intrusion Detection Systems (IDS) that monitor network activity.
- Security Information and Event Management (SIEM) solutions for log analysis.
- Audit logs that track user activities.
- Anomaly detection tools that identify suspicious behavior.
1.3 Corrective controls
Corrective controls are measures implemented to respond to and fix security incidents or compliance violations after they have been detected. They aim to minimize damage, restore systems, and prevent recurrence.
- Purpose: Corrective controls step in when preventive and detective measures fail, helping organizations mitigate the impact of an incident.
- Main function: Ensure business continuity by mitigating the impact of breaches.
- Examples:
- Incident response plans to contain and recover from attacks.
- Data backups to restore lost or corrupted data.
- System patches to fix vulnerabilities after an attack.
- Malware removal tools to clean infected devices.
1.4 Directive controls
Directive controls are measures that guide, prescribe, or mandate security actions to prevent incidents and ensure compliance. They set expectations for behavior and processes through policies, guidelines, training, and standards.
- Purpose: Define security policies, guidelines, and compliance requirements.
- Main function: Provide a security framework to ensure preventive, detective, and corrective measures are properly implemented and followed.
- Examples:
- ISO 27001 and NIST security frameworks.
- Organizational security policies for access management.
- Acceptable use policies for company assets.
- Regulatory mandates like GDPR and HIPAA compliance.
1.5 Deterrent controls
Deterrent controls are security measures designed to discourage or prevent malicious actions by creating consequences or increasing the perceived risk of detection.
- Purpose: Discourage malicious actions by increasing the risk and consequences of attacks. They make it clear that unauthorized access attempts will be detected and acted upon.
- Main function: Reduce the likelihood of cyberattacks by warning attackers and internal users of security measures.
- Examples:
- Security warning banners on systems.
- Surveillance cameras in secure areas.
- Legal consequences for security violations.
- Visible security policies to deter insider threats.
1.6 Compensating (alternate) controls
Compensating controls are alternative security measures implemented when primary controls are not feasible or sufficient. They provide equivalent or additional protection to mitigate risks.
- Purpose: Provide alternative security measures when primary controls are not feasible or insufficient.
- Main function: Reduce security risks when certain preventive or detective controls are unavailable.
- Examples:
- Strong password policies when MFA cannot be used.
- Additional network monitoring when a firewall cannot be deployed.
- Manual security reviews when automated scanning tools are unavailable.
2. Based on implementation
These security controls are categorized based on how they are applied within an organization’s security environment.
2.1 Technical controls
Technical controls are security measures implemented through technology to protect systems, data, and networks.
- Purpose: Use technology to enforce security policies and protect digital assets.
- Main function: Provide automated security protections to detect, prevent, and mitigate cyber threats.
- Examples:
- Firewalls and network segmentation.
- Endpoint protection and antivirus software.
- Data encryption and access control mechanisms.
- Multi-factor authentication (MFA) for secure login.
2.2 Administrative controls
Administrative controls are policies, procedures, and guidelines that govern security practices and ensure compliance. They focus on managing people and processes rather than technology.
- Purpose: Govern security practices through policies, procedures, and training.
- Main function: Define and enforce security best practices and compliance requirements.
- Examples:
- Employee security awareness training programs.
- Risk assessment and compliance audits.
- Access control policies and privilege management.
- Vendor risk management and third-party security policies.
2.3 Physical controls
Physical controls are security measures designed to protect personnel, hardware, and data from physical threats.
- Purpose: Protect physical assets and restrict unauthorized access to facilities.
- Main function: Prevent physical breaches, theft, and damage to infrastructure.
- Examples:
- Security guards and access-controlled doors.
- Surveillance cameras and motion detectors.
- Biometric authentication (fingerprint, facial recognition).
- Locked server rooms and data center security.
A strong cybersecurity strategy requires a mix of function-based and implementation-based security controls to prevent, detect, and respond to threats effectively. Layering these controls creates a multi-tiered defense, ensuring comprehensive protection for digital, operational, and physical security risks.
Why are security controls critical for organizations?
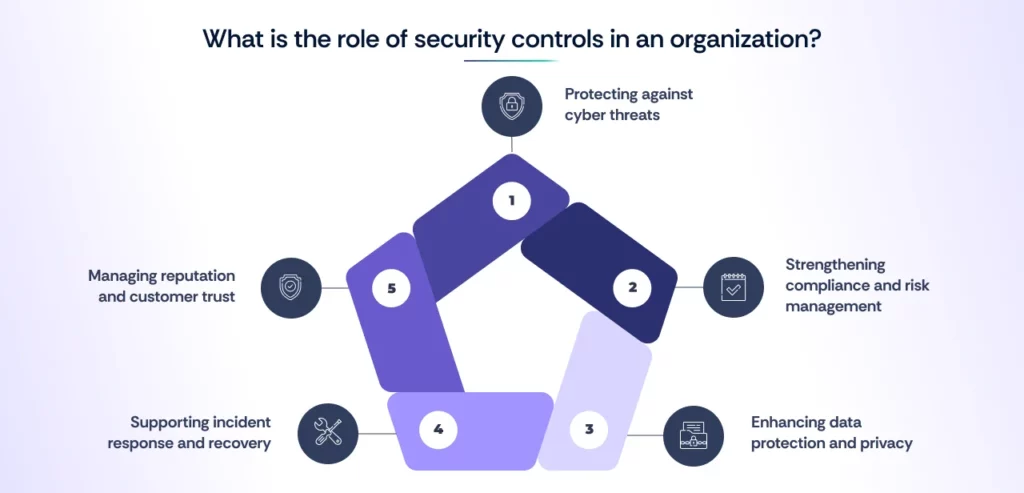
Security controls are essential for protecting systems, data, and networks from cyber threats, reducing risks, and ensuring compliance with industry regulations. Their primary roles include:
1. Protecting against cyber threats
- Prevent unauthorized access to sensitive data and systems.
- Detect and mitigate security breaches, reducing the impact of cyberattacks.
- Ensure business continuity by minimizing disruptions caused by security incidents.
2. Strengthening compliance and risk management
- Help organizations comply with security frameworks like ISO 27001, NIST, GDPR, HIPAA, and SOC 2.
- Support audit and reporting requirements by providing documentation and security logs.
- Reduce financial, legal, and reputational risks associated with non-compliance and data breaches.
3. Enhancing data protection and privacy
- Encrypt and safeguard sensitive information from unauthorized access.
- Enforce access controls to ensure only authorized users can interact with critical systems.
- Prevent data leaks and insider threats through monitoring and security policies.
4. Supporting incident response and recovery
- Enable quick detection and response to security incidents.
- Provide backup and recovery mechanisms to restore operations after an attack.
- Establish security policies and protocols for handling breaches efficiently.
5. Managing reputation and customer trust
- Strengthen customer confidence by demonstrating a commitment to security and compliance.
- Reduce reputational damage from data breaches and cyber incidents.
- Enhance brand value by maintaining a strong security posture and transparency in cybersecurity practices.
Mapping security controls with industry frameworks
Security controls are a fundamental requirement across multiple cybersecurity frameworks, ensuring organizations effectively manage risks and maintain compliance. Some key frameworks that define security controls include:
- NIST SP 800-53 – A comprehensive catalog of security and privacy controls used by U.S. federal agencies and widely adopted in various industries. It categorizes controls into families, such as access control, incident response, and risk assessment.
- ISO 27001 – Focuses on establishing an Information Security Management System (ISMS) with a structured approach to implementing security controls for risk management and compliance.
- SOC 2 – Defines security controls based on the Trust Services Criteria, ensuring data protection, confidentiality, and availability in service organizations.
- PCI DSS – Mandates security controls for organizations handling payment card data, emphasizing encryption, access controls, and continuous monitoring.
- HIPAA – Requires security and privacy controls to protect electronic protected health information (ePHI) in the healthcare industry.
- GDPR – Enforces strict data protection and privacy controls for organizations processing the personal data of EU citizens. It mandates encryption, access controls, data minimization, and breach notification protocols to ensure compliance.
NIST SP 800-53 is often used as a baseline for structuring security controls, and organizations can map their existing controls to these frameworks to achieve compliance across multiple standards. A well-defined security control strategy not only strengthens cybersecurity but also streamlines compliance efforts across different regulatory landscapes.
How do you choose the right security controls for your organization?
NIST Special Publication 800-53 Revision 5, or NIST security controls, comprises over 1,000 security and privacy controls, organized into 20 distinct control families. Not all organizations need to implement every security control written in the book.
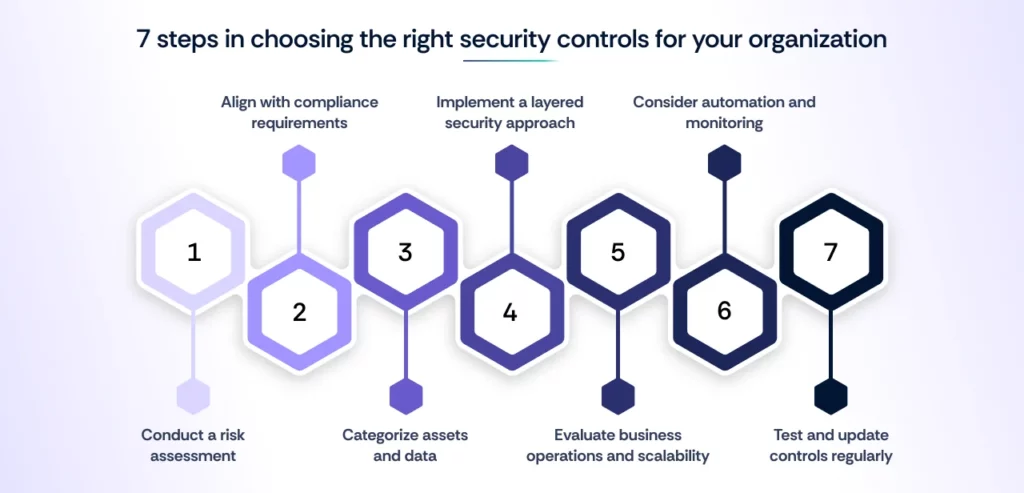
Selecting the right security controls requires a strategic approach based on risk, compliance, and business needs. Here’s how organizations can determine the most effective security controls:
- Conduct a risk assessment – Identify potential threats, vulnerabilities, and the impact of security breaches on your organization. This helps prioritize controls based on risk severity.
- Align with compliance requirements – Ensure controls align with industry frameworks depending on your regulatory obligations.
- Categorize assets and data – Identify critical assets and classify sensitive data to apply appropriate security controls, such as encryption for sensitive information and access controls for restricted systems.
- Implement a layered security approach – Choose a mix of preventive, detective, corrective, directive, deterrent, and compensating controls to ensure comprehensive protection.
- Evaluate business operations and scalability – Ensure that selected controls support your organization’s operational needs and can scale with future growth and evolving threats.
- Consider automation and monitoring – Leverage automated security tools for continuous monitoring, anomaly detection, and real-time threat response to enhance efficiency.
- Test and update controls regularly – Security threats evolve, so regularly assessing and updating security controls ensures they remain effective and aligned with emerging risks and compliance changes.
Simplifying your compliance journey with Scrut
Scrut streamlines security controls implementation and continuous management by automating control mapping to your required frameworks, providing a centralized dashboard for oversight, and enabling real-time compliance monitoring.
It simplifies audit readiness with automated evidence collection, enforces security policies, and integrates with cloud and identity management tools to detect and mitigate risks. By adopting a risk-based approach, Scrut helps organizations continuously manage and prioritize security measures, ensuring efficient resource allocation and a strengthened security posture.

FAQs
What is the difference between prevention and detection controls?
Prevention controls block threats before they occur, while detection controls identify and alert organizations about incidents that bypass preventive measures. Prevention stops attacks, whereas detection ensures missed threats are quickly addressed. Together, they create a layered security approach.
What is the difference between IT security and digital security controls?
IT security controls protect an organization’s infrastructure, including networks and servers, using firewalls, access controls, and encryption. Digital security controls have a broader scope, covering data privacy, online identity protection, and secure transactions. While IT security focuses on technical infrastructure, digital security extends to overall online safety and personal data protection.
How do security controls contribute to regulatory compliance?
Security controls support regulatory compliance by protecting sensitive data, mitigating risks, and enforcing security policies required by standards like ISO 27001, NIST, GDPR, and HIPAA. They prevent breaches, detect threats, and streamline audits, aiding risk assessments and compliance reporting while reducing fines and reputational risks.
What are NIST security controls?
NIST security controls are a set of guidelines defined in NIST Special Publication (SP) 800-53 to help organizations manage cybersecurity risks. These controls cover various aspects of security, including access control, data protection, incident response, and risk management.
How many security controls are in NIST SP 800-53?
NIST SP 800-53 Revision 5 includes over 1,000 security and privacy controls organized into 20 control families that address various cybersecurity requirements.
How do NIST security controls help with compliance?
NIST SP 800-53 serves as a baseline for various compliance frameworks, including ISO 27001, SOC 2, HIPAA, GDPR, and FedRAMP. Organizations can map their security controls to NIST guidelines to streamline compliance efforts.
Table of contents