NIST SP 800-171 explained with a downloadable compliance checklist

As the custodians of sensitive national information, defense industrial base (DIB) companies face a relentless barrage of sophisticated cyber threats. The security of the nation's supply chain hinges upon the robustness of the cyber posture of every Department of Defense (DoD) contractor. This is not merely an IT concern; it is a strategic business imperative. Cybersecurity expert Roger Spitz, in his book Disrupt With Impact: Achieve Business Success in an Unpredictable World, observed, "Epistemic security now rivals the significance of national security," a sentiment that captures the gravity of the challenge.
This framework for protection is codified in NIST SP 800-171, which provides the foundational NIST 800-171 requirements for protecting Controlled Unclassified Information (CUI) on nonfederal information systems. Mandated by the Defense Federal Acquisition Regulation Supplement (DFARS) 252.204-7012 clause, compliance with these requirements has long been a self-attested standard.
However, the introduction of CMMC 2.0 signals a pivotal shift toward verifiable security, raising the stakes for all organizations handling CUI. You need an active, questioning mindset to protect your systems the right way and keep your organization eligible for the DoD work that matters.
You will learn what NIST SP 800-171 requires, how it connects to CMMC (especially Level 2), who must comply, the key controls and documentation involved, and the practical steps to implement it.
What is NIST SP 800-171, and why does it matter?
NIST SP 800-171 is a foundational security framework published by the National Institute of Standards and Technology. Its explicit purpose is to provide recommended security requirements for protecting the confidentiality of CUI when that data is resident in nonfederal information systems and organizations. This collection of 110 NIST 800-171 requirements is organized into 14 security requirement families, establishing a comprehensive cyber defense posture.
The imperative for adopting the NIST SP 800-171 framework stems directly from DoD. Any organization, be it a prime contractor or a subcontractor, that processes, stores, or transmits CUI in non-federal systems or organizations in connection with a DoD contract is required to adhere to these requirements. The requirement is legally binding through the DFARS 7012 compliance clause (Defense Federal Acquisition Regulation Supplement clause 252.204-7012).
The current state of contractor readiness further explains why these requirements matter. A 2024 study conducted by Merrill Research and published by CyberSheath reported that only 4% of surveyed defense contractors believed they were fully prepared for CMMC certification, and the average SPRS self-assessment score was -12, well below the expected threshold.
This framework sits at the center of defense cybersecurity contracts because CUI, while unclassified, often includes sensitive technical designs, strategic plans, and proprietary information crucial to national security. Compliance with NIST SP 800-171 serves as the crucial CMMC baseline for the higher tiers of the Cybersecurity Maturity Model Certification (CMMC) program, specifically forming the core of CMMC Level 2 requirements. For any company seeking to remain an eligible partner to the DoD, rigorous implementation of these requirements is non-negotiable.
How NIST SP 800-171 relates to CMMC 2.0 Level 2
For the DIB contractors handling CUI, understanding the exact nature of the NIST 800-171 alignment with CMMC 2.0 is paramount. In the simplest terms, CMMC Level 2 is the DoD verification and certification framework for the implementation of the NIST SP 800-171 requirements.
The direct technical equivalence
At its core, CMMC Level 2 directly adopts the 110 NIST 800-171 requirements as its complete set of technical and procedural practices. There is no variance in the security practices themselves. If an organization achieves a CMMC Level 2 certification, they have successfully implemented every one of the security requirements prescribed by NIST SP 800-171, which has been the binding mandate under DFARS 7012 compliance since 2017.
This alignment means that the work undertaken for NIST 800-171 implementation directly supports the move toward CMMC compliance. The focus remains on establishing and maintaining a robust security posture capable of CUI protection. Achieving a certified CMMC Level 2 validates this posture.
The critical shift: From attestation to verification
The crucial distinction between the two frameworks lies in the concept of verification and accountability. Prior to CMMC 2.0, adherence to NIST 800-171 relied heavily on self-attestation, where a contractor would submit their score to the DoD’s Supplier Performance Risk System (SPRS). While organizations were still required to meet the NIST 800-171 requirements list, the DoD recognized that this system lacked consistent external validation.
CMMC 2.0 addresses this gap by layering a mandatory assessment requirements structure on top of the NIST framework. The CMMC Final Rule solidifies this model, forcing DIB contractors to choose one of two CMMC assessment paths:
- Self-assessment path: For non-prioritized acquisitions, the DoD permits an annual self-assessment for CMMC Level 2, with the results still reported to SPRS.
- Third-party assessment path: For organizations handling CUI on critical programs, a triennial (every three years) assessment by a Certified Third-Party Assessment Organization (C3PAO) is required. This certification is a non-negotiable prerequisite for contract award, a significant escalation from the previous self-attestation model.
CMMC 2.0 and the NIST 800-171 compliance guide
The CMMC framework effectively elevates the NIST 800-171 requirements from an 'honor system' to an auditable certification model, acting as the definitive CMMC baseline for the defense industry. It mandates rigorous CMMC documentation and processes to ensure practices are sustained and repeatable.
Furthermore, the inclusion of CMMC Level 1 (for Federal Contract Information, or FCI) and the planned inclusion of CMMC Level 3 (which incorporates the advanced, enhanced security requirements of NIST SP 800-172) ensure a tiered, scalable approach to cybersecurity across the entire supply chain. For any DoD contractor cybersecurity strategy, mastering the NIST SP 800-171 framework is the essential first step toward achieving verifiable CMMC certification.
Who needs to comply with NIST SP 800-171?
Compliance with the NIST SP 800-171 framework is a contractual imperative, not an optional security recommendation. It is legally mandated through DFARS clause 252.204-7012. The requirement applies broadly across DIB:
- DoD contractors: All prime contractors with the Department of Defense who handle, process, store, or transmit CUI in their information systems must comply with the 110 NIST 800-171 requirements.
- Subcontractors and defense suppliers: The compliance requirements must be flowed down through the entire multi-tiered contract structure. Any lower-tier subcontractors or defense suppliers who receive, generate, or access CUI are equally obligated to secure their CUI environment according to the NIST framework.
- DFARS clause linkage: The requirement for compliance is primarily driven by the presence of the DFARS 7012 compliance clause in the contract. This clause not only mandates the implementation of the NIST requirements but also outlines the mandatory incident reporting protocol.
- Supply chain security focus: Compliance is crucial for maintaining overall national supply chain security. The cyber posture of the largest defense firms is only as strong as the weakest link in their network of DoD contractors. The inability of any entity to implement the NIST 800-171 checklist and related requirements can result in loss of contract eligibility.
Exploring the 14 NIST SP 800-171 requirement families
The NIST SP 800-171 requirements are designed to be a comprehensive and cohesive set of cybersecurity practices, structured into 14 distinct requirement families. These families provide a logical grouping for the 110 NIST 800-171 requirements that organizations must implement to safeguard their CUI environment. Understanding these groupings is the first step in creating a rigorous NIST 800-171 compliance guide.
Here is an overview of the 14 NIST 800-171 control families:
NIST SP 800-171 versus CMMC 2.0: Bridging the accountability gap
While NIST SP 800-171 and CMMC Level 2 share the identical set of 110 NIST 800-171 requirements, their governance models are fundamentally different. The gap between them is one of verification and demonstrable rigor. Under the legacy DFARS 7012 clause, adherence to NIST 800-171 was largely based on self-attestation and a score reported to SPRS.
CMMC 2.0 closes this gap by institutionalizing a mandatory CMMC Level 2 assessment. The framework shifts the focus from simply implementing the requirements to proving they are sustained and managed. This involves rigorous CMMC documentation, including the System Security Plan (SSP) and various policies and procedures.
Depending on the criticality of the contract, the CMMC implementation timeline culminates in either a triennial CMMC C3PAO or an annual self-assessment. This move from the honor system to a verifiable audit model, the core difference between self-assessment vs third-party audit, is designed to drastically enhance DoD contractor cybersecurity and supply chain resilience. Organizations must prepare not just for technical security, but for audit readiness.
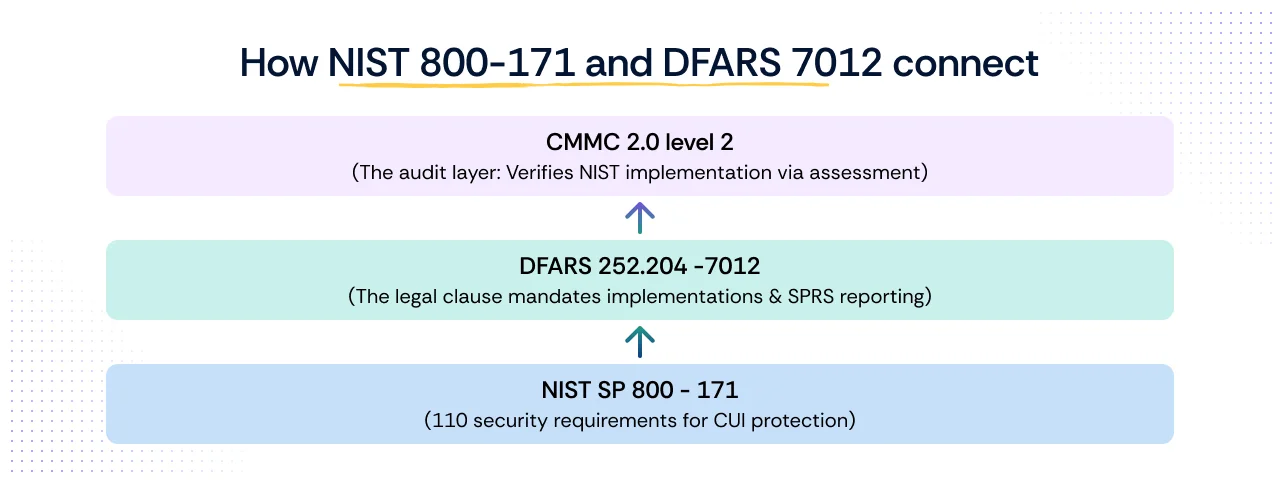
How NIST 800-171 and DFARS 7012 connect
The relationship between NIST 800-171 and DFARS 7012 is one of legal enforcement and technical implementation. DFARS clause 252.204-7012, titled "Safeguarding Covered Defense Information and Cyber Incident Reporting," is the legal cybersecurity clause inserted into contracts by DoD. This clause mandates two primary actions for contractors:
- Mandatory implementation: The clause requires the contractor to implement, at a minimum, the 110 NIST 800-171 requirements to provide "adequate security" for CUI.
- DoD reporting: Compliance is monitored via the SPRS score. DFARS 7012, strengthened by related clauses, requires contractors to perform a NIST 800-171 self-assessment using the DoD assessment methodology. The resulting summary score must be reported to the DoD’s SPRS.
This DoD reporting mechanism makes the performance of the NIST 800-171 self-assessment a mandatory contractual step. Furthermore, the clause requires contractors to report any cyber incidents within 72 hours of discovery.
Ultimately, DFARS 7012 established the compliance expectation, while CMMC Level 2 now provides the formal verification process built directly upon this foundational compliance requirement.
Documentation required for NIST SP 800-171 compliance
Achieving and demonstrating compliance with the NIST SP 800-171 requirements is a documentation-heavy endeavor. The DoD relies on comprehensive, auditable records to verify that a contractor has fully implemented the 110 NIST 800-171 requirements. These documents are the backbone of any successful CMMC Level 2 assessment and form the essential CMMC documentation.
Here are the major documents required for compliance (check the full list in the attached checklist):
- System security plan (SSP): The centerpiece of compliance, the NIST 800-171 SSP provides an overview of the organization’s system, the system boundaries of the environment processing CUI, and describes how each of the 110 requirements is met.
- Plan of action & milestones (POA&M): This document details any NIST 800-171 requirements that are not yet fully implemented. It must include a timeline, resources required, and milestones for completing each deficiency. Under CMMC 2.0, there are limitations on which requirements can be in a POA&M.
- CUI flow diagram: This critical visual document maps out exactly where CUI enters, resides, is processed, and is transmitted throughout the system. This directly ties to CMMC scoping documentation by defining the CUI flow and the system boundary.
- Network boundary diagram: A technical diagram illustrating the logical and physical segmentation of the system components, clearly delineating the CUI environment from non-CUI systems.
- Policies & procedures: Comprehensive, formally approved documents that dictate the organization's rules and operational steps for all 14 requirement families, covering areas like Access Control and Configuration Management.
- Incident response plan: A documented, tested strategy outlining the processes for detecting, analyzing, containing, and recovering from a cyber incident, per the Incident Response family requirements.
- Risk assessment report: Documents the process used to identify threats and vulnerabilities to the CUI environment, assessing the potential impact and likelihood of compromise, as required by the Risk Assessment family.
- Scoping documentation (CMMC): Formal documentation clarifying the asset types within the CMMC scoping (e.g., CUI Assets, Security Protection Assets) to clearly define the assessment boundary and ensure the NIST 800-171 requirements list is applied correctly.
- External service provider (CMMC ESP) documentation: Records detailing how cloud services or other external providers manage the security of CUI, including any shared responsibility matrix, ensuring that the necessary requirements flow down to them.
- Audit & logging documentation: Records demonstrating continuous monitoring and retention of system and network events. This includes documentation on audit mechanisms, review schedules, and storage, which is particularly vital for organizations preparing for potential CMMC Level 3 requirements.
Common challenges in NIST 800-171 and CMMC compliance
Organizations pursuing NIST 800-171 compliance and eventual CMMC Level 2 assessment often encounter hurdles related to complexity and resource allocation. Overcoming these CMMC challenges requires a strategic and clear approach, particularly in technical and documentation areas.
Scrut simplifies NIST 800-171 compliance
The complexity of implementing 110 NIST 800-171 requirements and maintaining continuous readiness for a CMMC Level 2 assessment makes the use of specialized compliance automation platforms essential for modern DoD contractor cybersecurity.
Scrut is designed to simplify and accelerate this daunting process. These tools connect directly to an organization’s IT infrastructure, security tools, and cloud environments to automate the most time-consuming aspects of compliance:
- Evidence collection: Automation platforms continuously map security settings, system configurations, and user access logs to the specific NIST 800-171 requirements. This real-time, automated evidence collection drastically reduces the manual effort required for audits.
- Continuous monitoring: At Scrut, the controls are monitored on a daily basis, providing immediate alerts when a security setting deviates from compliance. This ensures the organization maintains the required security posture long after initial implementation, addressing the crucial "sustained compliance" challenge.
- Documentation maintenance: By centralizing evidence, the platforms simplify the creation and maintenance of the NIST 800-171 SSP and POA&M. This dedicated NIST 800-171 automation ensures the required CMMC documentation is always audit-ready, transforming the journey toward CMMC compliance from a manual, quarterly scramble to an integrated, real-time function.
Secure your defense future today!
Ready to transform your NIST 800-171 implementation into verifiable CMMC compliance? Explore how Scrut automation provides the continuous monitoring and automated evidence collection required to confidently pass your CMMC Level 2 assessment.

FAQs
1. Who is legally required to comply with NIST SP 800-171?
Any DoD contractor (prime or subcontractor) that processes, stores, or transmits Controlled Unclassified Information (CUI) on nonfederal information systems must comply. This is mandated by the DFARS 7012 clause (252.204-7012) in their contracts, which requires the implementation of the 110 NIST 800-171 requirements.
2. Is NIST 800-171 the same as CMMC Level 2?
No, they are not the same, but they are fully aligned. CMMC Level 2 uses the 110 NIST 800-171 requirements as its technical baseline. The key difference is that CMMC 2.0 adds a verification requirement, mandating either a formal CMMC third-party assessment (C3PAO) or an executive-led self-assessment, which elevates the level of required rigor and accountability.
3. What is the most critical compliance document I need for NIST 800-171?
The most critical document is the System Security Plan (SSP). The NIST 800-171 SSP describes the boundary of your CUI environment and details how your organization has implemented or plans to implement all 110 security requirements. It is a mandatory requirement for both DFARS and CMMC compliance.
4. What is a POA&M, and how does it relate to NIST 800-171 and CMMC?
A POA&M (Plan of Action & Milestones) is a document that lists all security requirements from the NIST 800-171 requirements list that are not yet fully implemented. Under CMMC Level 2, the use of a POA&M is allowed for non-critical requirements, but it is limited, and critical requirements must be implemented before certification can be granted.
5. What is the importance of the SPRS score in the compliance process?
The SPRS score is the numerical result of your NIST 800-171 self-assessment using the DoD Assessment Methodology. This score must be reported to the DoD's Supplier Performance Risk System (SPRS) and is a contractual obligation under the DFARS clause. It provides the DoD with visibility into your organization's current level of NIST 800-171 implementation.
6. Which NIST 800-171 requirement family is most commonly failed by contractors?
Historically, one of the most frequently challenged areas involves the System & Communications Protection (SC) family, specifically requirements related to implementing strong encryption and network segmentation. Additionally, the Incident Response (IR) and Audit & Accountability (AU) families, which require testing and continuous monitoring, are often cited as CMMC challenges due to the need for advanced technical capabilities and sustained operation.