CMMC Level 1 vs Level 2: How to know your required compliance level

The security of the supply chain is a non-negotiable frontier in national defense. The Department of Defense (DoD) established the Cybersecurity Maturity Model Certification (CMMC) 2.0 as its vital mechanism to standardize and elevate the cyber hygiene of the Defense Industrial Base (DIB). This program defines a tiered set of required practices to safeguard sensitive government information, ensuring a minimum baseline of trustworthiness.
While CMMC 2.0 defines three maturity levels, Foundational (Level 1), Advanced (Level 2), and Expert (Level 3), contract eligibility for the vast majority of DIB organizations centers on the first two tiers. The compliance journey, therefore, almost always focuses on CMMC Level 1 (Foundational) and CMMC Level 2 (Advanced). The correct application of these levels is fundamentally determined by the data an organization handles, specifically, whether it is basic FCI (Federal Contract Information) or the more sensitive CUI (Controlled Unclassified Information).
This blog serves as an expedition guide, helping you unravel the core differences between CMMC Level 1 vs Level 2, understand the assessment rigor of each, and precisely map your organization’s cybersecurity posture to the required maturity level for contract eligibility. The goal is to move from compliance complexity to verifiable cyber maturity.
CMMC Level 1: The foundational blueprint for cyber hygiene
The journey toward CMMC compliance commences here, at CMMC Level 1: Foundational. This tier is the essential entry point, establishing the non-negotiable minimum standard of cyber maturity required for any organization handling specific categories of unclassified government data.
2.1 The purpose: Safeguarding FCI
The primary objective of Level 1 is the protection of FCI. FCI is defined as non-public information provided by or generated for the Government under a contract. It is the necessary operational data, like contract numbers, delivery schedules, or internal correspondence, that provides the working "wrapper" for a contract, but is not designated for public release.
This level applies to the largest segment of the DIB, those contractors who only process, store, or transmit FCI and do not handle the more sensitive CUI.
2.2 The controls: A set of 17 basic practices
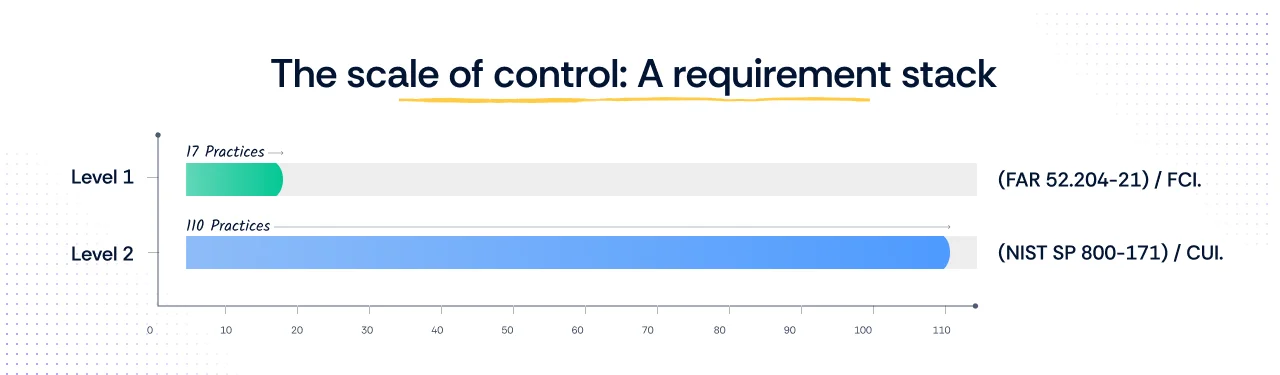
To achieve the Foundational level, an organization must implement the CMMC Level 1 requirements (17 practices). These practices are directly derived from the requirements stipulated in the Federal Acquisition Regulation (FAR) Clause 52.204-21, Basic Safeguarding of Covered Contractor Information Systems. This number of practices represents the foundational steps needed to establish a perimeter of basic cyber hygiene, serving as the essential first line of defense.
2.3 Key focus areas: Establishing the basics
The 17 practices are focused on establishing fundamental security controls across key domains. Unlike the procedural depth required at higher levels, Level 1 emphasizes "performance”, the successful execution of the specified control.
These focus areas ensure simple, necessary steps like using passwords, locking server room doors, and ensuring basic antivirus protection are consistently applied.
2.4 The assessment: Self-reliance
The assessment requirement for CMMC Level 1 reflects its foundational nature: an annual self-assessment.
The organization's Affirming Official is responsible for performing the assessment against the 17 practices and officially attesting to the results. These results must then be submitted to the DoD's Supplier Performance Risk System (SPRS). Crucially, unless specified in the contract for special cases, no third-party assessment by a C3PAO (Certified Third-Party Assessment Organization) is needed.
This self-assessment model emphasizes organizational ownership of compliance. For automation platforms like Scrut, this process is streamlined by providing the necessary control mapping, evidence collection workflows, and historical data to confidently prepare the final attestation package for submission.
CMMC Level 2: The advanced requirement for CUI
Climbing the next tier of compliance brings us to CMMC Level 2: Advanced. This level signifies a profound leap in cyber maturity, moving beyond basic hygiene to implement a comprehensive, institutionalized framework for protecting the nation's most sensitive unclassified data.
3.1 The purpose: Protecting CUI
The singular, mission-critical purpose of Level 2 is the robust protection of CUI. CUI is the sensitive core content of DoD programs, including technical data, research, intellectual property, and defense specifications. Any organization that processes, stores, or transmits CUI is required to meet Level 2 compliance.
This requirement applies to organizations handling sensitive defense data, where the compromise of this information could severely impact national security or the efficacy of military systems.
3.2 The controls: Alignment with NIST SP 800-171
Achieving Level 2 compliance demands the implementation of the CMMC Level 2 requirements (110 practices / NIST SP 800-171). These 110 controls are fully aligned with the requirements outlined in the National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171 Revision 2.
The adoption of the NIST standard means organizations must establish a formal, documented, and consistently executed program for managing cyber risk, demonstrating not just the performance of controls, but the institutionalization of cybersecurity processes across 14 security domains.
3.3 Key focus areas: Institutionalizing security
Level 2 practices require depth and documentation across all facets of an organization's security posture.
The requirement for an SSP and the allowance for a POA&M (with a limited 180-day window for critical control closure) underscores the expectation that compliance is a managed, verifiable program, not a mere checklist.
3.4 The assessment: A dual-track approach
The core assessment difference, CMMC self-assessment vs C3PAO, is key to Level 2 and is bifurcated based on the criticality of the CUI being handled, a reflection of the DoD's risk-based approach to validation:
- Triannual Third-Party Assessment (C3PAO):
This rigorous external audit, conducted every three years by a Certified Third-Party Assessment Organization, is mandatory for contracts involving "prioritized acquisitions." This typically applies to CUI that is deemed critical to national security, such as data related to weapon systems or command and control platforms.
- Self-assessment:
Organizations handling CUI associated with "non-prioritized acquisitions," where the data is deemed less critical to national security (e.g., related to general supplies or logistics), may perform an annual self-assessment. The results must still be formally submitted to the SPRS (Supplier Performance Risk System).
The DoD states that the CMMC 2.0 framework is designed to provide assurance that contractors can "adequately protect CUI at a level commensurate with the risk." This risk-based bifurcation of assessment requirements is the core mechanism for matching assurance rigor to data sensitivity.
For a platform like Scrut, this section highlights the critical role of providing automated evidence collection, POA&M tracking, and continuous compliance monitoring for all 110 controls, directly supporting organizations, whether they face the internal rigor of the self-assessment or the intense scrutiny of a C3PAO audit.
CMMC Level 1 vs Level 2: A direct comparison
Our expedition has now reached the critical phase of synthesizing our findings. The transition from Level 1 to Level 2 is more than a simple increase in controls; it represents a fundamental commitment shift in protecting sensitive data. Considerations regarding CMMC Level 2 cost and timeline are significant factors. The table below serves as a definitive chart to navigate the critical differences between CMMC Level 1 vs Level 2.
The critical takeaway for compliance
The stark contrast between Level 1 and Level 2—17 controls versus 110, self-attestation versus potential C3PAO audit, underscores the need for automated governance solutions. For any organization processing CUI, the documentation burden and the complexity of maintaining 110 practices continuously (e.g., required for a successful audit) are often the largest hurdles.
A compliance platform designed for the DIB, such as Scrut, is precisely positioned to ease this burden by automating evidence collection for the 110 controls, ensuring the organization maintains a POA&M readiness posture, and generating the necessary SSP documentation required for the C3PAO engagement.
How to know which level applies to your expedition
The definitive choice between CMMC Level 1 and Level 2 hinges entirely upon one critical factor: the type of government data your organization is authorized to access, store, process, or transmit. The data itself acts as your compass, pointing directly to the required compliance maturity.
1. The decisive factor: Data handling
The rules governing the applicability of the two primary levels are clear-cut:
- If your organization exclusively handles FCI and does not handle CUI, you are required to achieve CMMC Level 1.
- If your organization stores, processes, or transmits any quantity of CUI, you must achieve CMMC Level 2.
2. The hidden CUI hazard
While the rule is simple, its application requires meticulous internal scrutiny. It is easy to assume you only handle FCI, but CUI often infiltrates operational environments unintentionally. As curious explorers of your own internal workflows, you must investigate where this sensitive information may be residing:
- Emails: Attachments or body text containing specific technical or program details.
- Shared documents: Files labeled as "Proprietary," "Limited Distribution," or containing specific DoD markings that meet the CUI criteria.
- Design drawings and specifications: Technical data that is foundational to a defense product or service.
The presence of CUI in just one shared folder or a single employee's email instantly triggers the far more rigorous Level 2 requirements.
3. Navigating uncertainty
If you remain uncertain about the specific data type associated with a contract, the path forward is to seek definitive guidance:
- Review contract clauses: Scrutinize the contract's Statement of Work and applicable clauses, which often explicitly reference FAR 52.204-21 (for FCI) or the requirement to protect CUI.
- Consult the contracting officer: The Contracting Officer is the official government resource who can provide authoritative clarification on the required CMMC level for the acquisition.
Dispelling the myths: Common CMMC misconceptions
As a groundbreaking compliance framework, the CMMC program naturally attracts speculation. For organizations embarking on this process, it is essential to discard common misunderstandings that can lead to costly non-compliance. Our final act of exploration is to dispel five critical myths.
Myth 1: “Level 1 is optional.”
The reality: Level 1 is the Foundational minimum requirement for virtually every organization in the DIB that handles FCI, intended to be mandatory in most contracts (excluding COTS). It is the baseline assurance of basic cyber hygiene.
Myth 2: “Level 2 is only for primes.”
The reality: Any subcontractor, regardless of size, that processes, stores, or transmits CUI received from a prime must meet the CMMC Level 2 requirement for their CUI systems. The data dictates the level, not the contract tier.
Myth 3: “I can mix Level 1 and Level 2 systems.”
The reality: CMMC scoping is strict: if a network segment processes CUI, the entire enclave must comply with the 110 NIST SP 800-171 controls required for Level 2, even if it also handles FCI. Segmentation must be definitive.
Myth 4: “CUI is clearly labeled every time.”
The reality: Organizations cannot rely solely on the presence of a marking. If the information's content meets the official definition of CUI (e.g., sensitive technical details), it must be protected under Level 2 requirements regardless of labeling errors.
Myth 5: “Documentation doesn’t matter for Level 2.”
The reality: Documentation is paramount. Auditors (C3PAO) require the mandatory SSP and a managed POA&M to prove the institutionalization and repeatability of the 110 controls; performance alone is insufficient.
With these misconceptions clarified, the roadmap for compliance becomes clear. For organizations utilizing a compliance automation platform, these risks are easily mitigated by enforcing strict scoping and providing continuous, automated evidence management.
How Scrut guides the compliance expedition
An automation platform like Scrut serves as the essential toolkit for the entire CMMC journey, transforming the complex, continuous requirements into a verifiable and manageable program. It accelerates the initial readiness phase by helping organizations accurately scope their environments (Level 1 vs. Level 2), providing templates for the critical SSP and POA&M, and mapping controls instantly.
The core benefit is continuous compliance: Scrut uses automated integrations to collect evidence for the 17 or 110 controls 24/7, eliminating the manual friction of reporting and ensuring against compliance drift. This automated evidence collection and real-time monitoring guarantee organizations are continuously ready for the annual Level 1 self-assessment or the rigorous triennial Level 2 C3PAO audit, drastically reducing cost, time, and uncertainty.
Ready to turn CMMC complexity into guaranteed audit-readiness? Chart your compliance course with Scrut today.
The search results confirm that the core of CMMC Level 1 vs. Level 2 confusion revolves around data type, number of controls, and assessment requirements.
Frequently Asked Questions (FAQs)
How do I know if my organization needs CMMC Level 1 or Level 2?
The required level is determined by the data you handle. If you only handle FCI (Federal Contract Information), Level 1 is typically required. If you store, process, or transmit CUI (Controlled Unclassified Information), you must aim for Level 2 or higher. Always check the specific requirements outlined in your DoD contract.
What is the biggest difference in security controls between Level 1 and Level 2?
The difference is scale and complexity. CMMC Level 1 requires 17 basic cybersecurity practices, focused on fundamental cyber hygiene (like passwords and basic access control). CMMC Level 2 requires 110 practices, which are the full set of controls from NIST SP 800-171, demanding advanced security measures like MFA, encryption, incident response plans, and documented policies.
Is Level 1 certification done by self-assessment, and is Level 2 always a C3PAO audit?
Not always. Level 1 requires an annual self-assessment submitted to SPRS. For Level 2, there is a dual pathway:
- C3PAO Audit: A triennial audit is required for contracts involving CUI critical to national security ("prioritized acquisitions").
- Self-Assessment: An annual self-assessment is permitted for contracts involving non-critical CUI ("non-prioritized acquisitions").
What is the difference between FCI and CUI, and why does it affect the CMMC Level?
FCI is basic, non-public operational data (e.g., contract numbers, delivery schedules). CUI is more sensitive, regulated information that requires safeguarding by law (e.g., technical drawings, intellectual property). CUI poses a higher risk if compromised, which is why it mandates the more robust 110 controls of Level 2.
Can I use a Plan of Action and Milestones (POA&M) to achieve CMMC Level 2?
Yes, but with limits. CMMC 2.0 allows POA&Ms to address certain security control deficiencies identified during a Level 2 assessment. However, you must meet a minimum compliance score threshold (currently 88 out of 110 controls) before being granted conditional certification, and all gaps must be remediated within 180 days. Level 1 generally does not allow for a POA&M.
If I'm a subcontractor, does my CMMC level depend on the prime contractor?
Yes, indirectly. The CMMC requirement flows down the supply chain. If the prime contractor flows down CUI to you, you must meet the Level 2 requirements for the systems handling that data, regardless of your position in the chain or size. If you only handle the prime's FCI, Level 1 may suffice.


















